Malware + Recommended + Security News
AceDeceiver Malware Can Infect Non-Jailbroken iOS Devices
Posted on
by
Graham Cluley

I’ve said it before, and I’ll no doubt say it again — if you care about your iPhone or iPad’s security, then you won’t resort to jailbreaking.
Be that as it may, a newly-discovered malware attack, which can infect non-jailbroken devices without the user’s knowledge, may have shaken the confidence of many, and sent shivers down the spines of some.
Security researchers at Palo Alto Networks have described in detail a Trojan horse that is capable of infecting factory-configured iPhones and iPads.
The Trojan, dubbed AceDeceiver, infects iOS devices in an ingenious way — exploiting flaws in Apple’s anti-piracy DRM software, known as FairPlay.
Here is how the researchers describe AceDeceiver’s novel method of infecting your iPhone or iPad:
“Apple allows users [to] purchase and download iOS apps from their App Store through the iTunes client running in their computer. They then can use the computers to install the apps onto their iOS devices. iOS devices will request an authorization code for each app installed to prove the app was actually purchased. In the FairPlay MITM attack, attackers purchase an app from [the] App Store then intercept and save the authorization code. They then developed PC software that simulates the iTunes client behaviors, and tricks iOS devices to believe the app was purchased by [the] victim. Therefore, the user can install apps they never actually paid for, and the creator of the software can install potentially malicious apps without the user’s knowledge.”
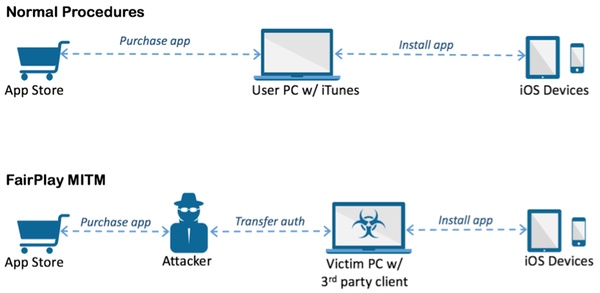
The only silver lining is that it appears that you are only likely to be in the firing line if you connect your iPhone or iPad to your Windows PC and live in China.
Palo Alto Networks has warned, however, that it would be relatively simple for the malicious code to be tweaked to infect victims in other countries too.
For the attack to succeed, the Windows computer—which is to be connected to the iOS device—has to have already been compromised with malware.
The hackers do this, say Palo Alto Networks’s researchers, with a program called “爱思助手 (Aisi Helper),” which acts as the “man-in-the-middle” of this MITM attack. The potential for using such a method for large-scale attacks against iOS devices has previously been proposed in research papers, but has not been seen in the wild.
Aisi Helper is promoted as software that provides various services for iPhone and iPad owners, including system backup, clean-up, device management and jailbreaking.
However, according to the researchers, Aisi Helper also silently installs a malicious app to any connected iOS devices. Presently, it appears that the malicious app connects to a third-party iOS app and game store that asks users to enter their Apple ID passwords.
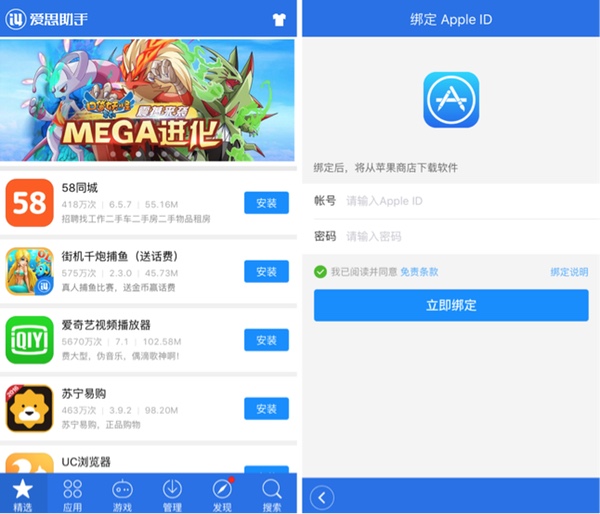
Many of the apps offered in the store are pirated, and — despite assurances — passwords entered by users are reportedly sent to servers under the control of Aisi Helper’s developers.
To aid further in the spread of the malware, the researchers claim that visiting the Aisi Helper website from a desktop computer prompts users to install the client software, which in turn will spread the AceDeceiver Trojan.
Meanwhile, if a user visits the website from an iOS device, an enterprise certificate-signed version of the Aisi Helper iOS client is recommended for installation.
The security researchers who uncovered the AceDeceiver Trojan say that it managed to penetrate the official Apple app store, posing as a wallpaper app, and seemingly avoiding detection by Apple’s Gatekeeper by only executing controversial behaviour if it determined it was running on a device in mainland China.
What can you do to protect yourself from AceDeceiver?
Apple removed the three Trojan apps from its App Store in late February, but the Aisi Helper Windows program can still install the apps to non-jailbroken iDevices using the FairPlay MITM attack.
If you ever installed the Aisi Helper software, in either its Windows client or iOS app incarnation, it is probably sensible to remove it and change your Apple ID passwords at your earliest opportunity. Furthermore, it would be wise to enable two-factor authentication for your Apple ID.
Users of Intego VirusBarrier with up-to-date definitions can detect the known components of the malware as iOS/AceDeceiver, and can detect the W32 tools used for it as W32/AceDeceiver.
Furthermore, if you are a business, check for unknown or unusual enterprise provisioning profiles and whether any managed Apple devices are showing the following bundle identifiers: aisi.aisiring, aswallpaper.mito, aswallpaper.mito, i4.picture.
Although the threat of AceDeceiver may be small for those of us who are based outside China, or who never attach our iDevices to a Windows computer, there is clearly the potential for this technique to be abused in other attacks by online criminals.
And it is also important to note that it has been possible to infect non-jailbroken iOS devices with malware before.
As we have reported in the past, targeted attacks have used the ad-hoc or enterprise provisioning features that Apple provides for app developers to beta-test their software or companies who wish to roll out their own apps to staff.
These types of attacks, however, were fairly specialised. The methodology used by AceDeceiver has the potential to infect many more iOS users, particularly if other criminals choose to follow in its footsteps.
So, going back to my earlier claim that jailbroken iDevices are less secure than their non-jailbroken cousins — is that still true in light of AceDeceiver?
Yes, it undoubtedly remains the case that there are good security reasons why you should never jailbreak your device, as you are introducing more risks. It’s just that those of us who chose not to jailbreak our iPhones and iPads are a little less safe than we thought before.
Editor’s Update, March 17: This post was updated for accuracy and comprehensiveness. See below for details.
The AceDeceiver Trojan functions with a Windows application, parading as an iOS utility, which is able to infect iOS devices with malicious apps. Users are tricked into providing their Apple ID and password, giving attackers access to their credit card numbers and other personal data.
Have you unwittingly dowloaded one of the three infected applications? The following apps were published on the App Store starting last year, appearing as utilities to browse and download wallpapers for your device:
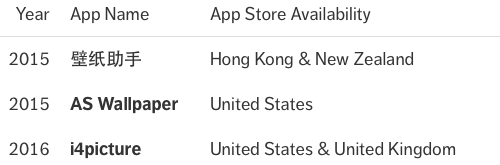
If you downloaded any of these applications, delete them from your iOS device and iTunes library. Intego VirusBarrier will also detect the Trojan as iOS/AceDeceiver.
Editor’s Update, March 18: Intego is experiencing high call volume from customers asking about anti-virus protection for iPhones and iPads, and whether or not it is possible to use VirusBarrier for Mac to scan for malware on iOS devices.
While Apple made a head scratching decision to eliminate the category of anti-virus and anti-malware products from their iOS App Store, and removed VirusBarrier iOS, our VirusBarrier for Mac customers are unaffected by this decision. VirusBarrier for Mac still scans for viruses on iOS devices; it will find and eradicate viruses found in document directories on iPhones and iPads.
You can scan your iOS devices with VirusBarrier when they are connected directly to your Mac. For additional information on how to do this, visit this page on our support site.