Malicious party hijacks 24% of Tor network
Posted on
by
Joshua Long

You may have heard of Tor, a distributed network designed to anonymize users’ online activities. While that sounds great for protecting one’s privacy, Tor has a number of major flaws.
Let’s briefly review what Tor is, and then let’s take a look at the most recent research into why it’s unsafe.
What is Tor?
Tor was originally an acronym for The Onion Router. Its main objective is to anonymize online activity.
The Tor network uses randomly chosen routes, consisting of “relays” and “exit nodes” offered by many anonymous parties. A relay is a computer that passes on your network requests to another computer on the Tor network. An exit relay, or exit node, is the computer through which your traffic emerges onto the Internet to reach its destination. If you load a Web site through Tor, the Web server will think the exit node’s IP address is your own computer’s IP address.
Is Tor really private, anonymous, and safe to use?
There are numerous privacy concerns about how the Tor network operates, and many theoretical and real-world Tor attacks have been documented. Law enforcement agencies have apprehended criminals who mistakenly believed that Tor was keeping them anonymous.
Malware has even been injected into Tor traffic by malicious parties. If you use Tor, it’s wise to use good anti-malware software with real-time scanning. We recommend Intego VirusBarrier (part of Mac Premium Bundle), or Intego Antivirus for Windows.
One major issue is that anyone can operate a Tor relay—which makes it easy for intelligence agencies and malicious parties to spy on, and potentially modify, Tor traffic.
One malicious party controlled 24% of all Tor exit nodes
Here’s the most recent example of a real-world Tor attack that demonstrates why it’s unsafe.
According to a report published on Saturday, a single unidentified threat actor controlled 23.95% of all Tor exit relays on May 22, 2020. The report states that as of August 8, the same attacker still controlled more than 10% of all exit nodes.
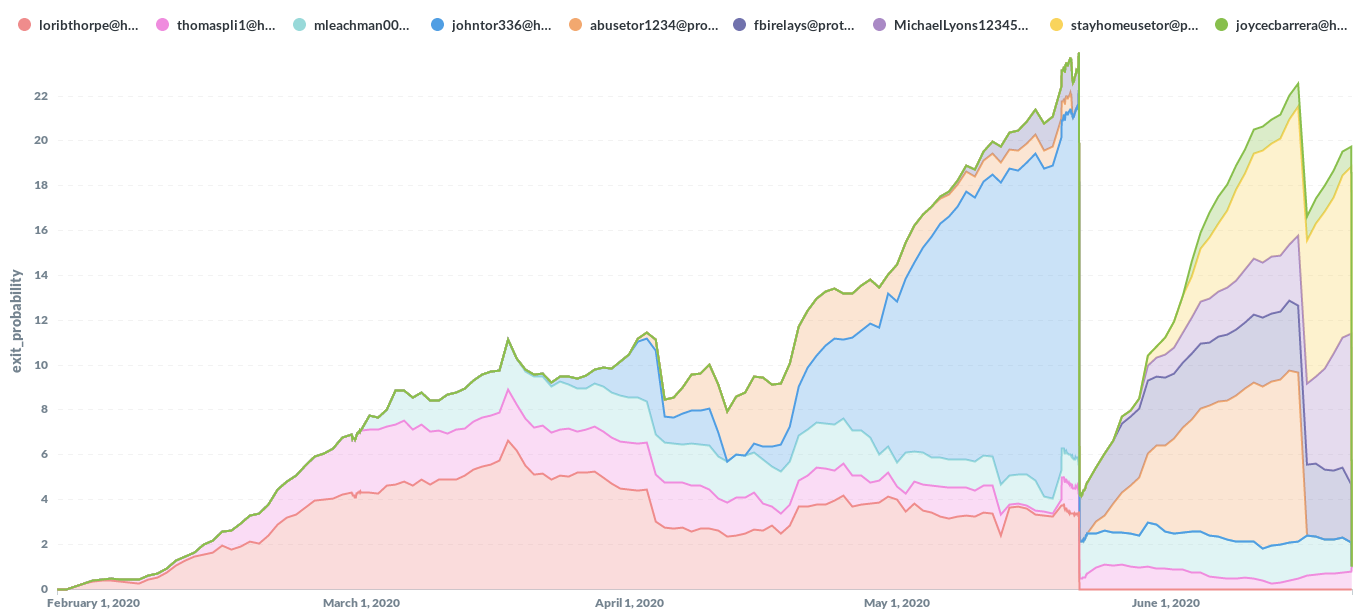
Nearly 24% of all Tor exit nodes were controlled by a single attacker on May 22. Image: nusenu
The threat actor is engaging in a man-in-the-middle attack to remove security from some Web traffic. When certain traffic passes through the relay, it downgrades the connection from HTTPS to HTTP. It then replaces Bitcoin addresses within the page, in an attempt to make money for the attacker.
It’s worth noting that the attacker might also be monitoring the traffic for sensitive or personally identifiable information.
According to ZDNet, a similar but much smaller-scale attack occurred in 2018.
Using a trusted VPN is better than Tor for privacy and security
Given how easy it is for spies and hackers to create their own Tor relays and monitor (or even modify) traffic, we cannot recommend using Tor as a means of protecting your privacy.
The better choice for protecting your privacy and security is to use a trusted VPN. The acronym VPN stands for virtual private network. When using a VPN on your computer or mobile device, the VPN hides your IP address from the destination servers. If you’re concerned about someone potentially obtaining logs of your activity from the VPN provider, use a VPN with a no-log policy.
Also, avoid using any so-called “free” VPN services. Any high-quality VPN service is expensive to operate. If users aren’t paying money for the service, consider how the company generates revenue. If it’s unclear how they can afford to run a VPN, they may be monitoring traffic and selling user data.
Intego recommends and trusts the following VPN providers: Private Internet Access, CyberGhost, and ZenMate. Each offers promotional discounts when you sign up.
To learn lots more about VPNs and some of their many benefits, check out our featured article, Why you should use a VPN on Mac and iOS — and How To.
How can I learn more?
 Each week on the Intego Mac Podcast, we discuss the top security and privacy concerns for users of Apple products. For example, we talked about the latest Tor attack in episode 148. Be sure to subscribe to make sure you never miss the latest episode.
Each week on the Intego Mac Podcast, we discuss the top security and privacy concerns for users of Apple products. For example, we talked about the latest Tor attack in episode 148. Be sure to subscribe to make sure you never miss the latest episode.
You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
Follow Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).