What is SMS? How It works, why it’s insecure… and why we still need it
Posted on
by
Kirk McElhearn and Joshua Long

When Steve Jobs introduced the iPhone in 2007, he said, “the killer app is making calls.” Back then, he might have been correct, but that’s no longer the case.
The killer app today for mobile phones is messaging, and there are countless messaging apps. Of course there’s Apple Messages, which is built into every iPhone, but there are plenty of third-party options, too. These include Meta’s apps WhatsApp and Facebook Messenger, as well as Telegram, Signal, Snapchat, and many others. (See our article comparing several popular secure messaging apps.)
Instant messaging on cell phones began with SMS, which stands for short message service (or short messaging service). Originally, an SMS text message could only contain basic characters, and had a tight limitation on message length. SMS has progressed a lot since its origin, and it’s still an important protocol today. Although it isn’t end-to-end encrypted, it’s not going away any time soon.
Let’s explore what SMS is, how it works, and why it’s still needed—even though it’s not secure.
In this article:
- What is SMS?
- How does SMS work?
- Why is SMS important?
- SMS and IoT
- Why is SMS insecure? Should you use it for 2FA?
- What is RCS? Will Apple ever adopt it?
- What is the future of SMS?
- How can I learn more?
What is SMS?
If you’ve been using a mobile phone for a while, or if any one of your contacts doesn’t have an iPhone, you’ve certainly sent and received many SMS texts. Some 25 billion SMSes are sent every year. While that sounds like a large number, it is well below the number of messages sent through other messaging apps. For example, more than 100 billion messages are sent via WhatsApp each year.
Even if everyone you know has an iPhone, or even if you primarily use third-party messaging apps, you probably still receive SMSes. I get SMS text messages from my mobile phone company, telling me that my latest bill is available; from my doctor, or dentist, reminding me of an appointment; and, regularly, from websites sending me a six-digit code as a second factor to log into their service.
And, of course, there is SMS spam. Depending on the country you live in and other factors, you may receive multiple spam SMS messages every day, many of which are scams. Scam messages are sometimes called smishing (or smshing, short for SMS phishing).
How does SMS work?
When you send an SMS, you don’t send it directly to the person you’re messaging. As with email, SMS messages go through a server, called a short message service center (SMSC). This server then attempts to deliver the message to the recipient. If it cannot do so—for example, if the recipient’s phone is turned off, or they have no cellular service—it will try again later.
SMS messages are short. Because of how the SMS protocol works, messages are limited to 160 characters. However, for some languages, such as Japanese, Arabic, or Ukrainian, which do not use the standard GSM 7-bit character set but rather UTF-16, the limit is 70 characters. (You might notice when texting someone who doesn’t have an iPhone that the soft character “limit” drops from 160 to 70 if you add emojis or certain special characters.)
The SMS protocol also includes support for MMS, or multimedia messaging service, which can include photos, low-resolution short videos, or audio clips.
Why is SMS important?
SMS can be seen as the lowest common denominator of messaging. It’s the fallback if the sender’s phone and the recipient’s phone do not both support the same, more modern messaging standards.
If you use Apple’s Messages app, you’ve likely noticed that some of your sent messages appear in blue bubbles, while others appear as green bubbles. Blue bubbles indicate that you’re texting with someone who owns an Apple device. Green bubbles indicate that you’re texting with someone over SMS or MMS; this usually means they have an Android smartphone or other non-iPhone device.
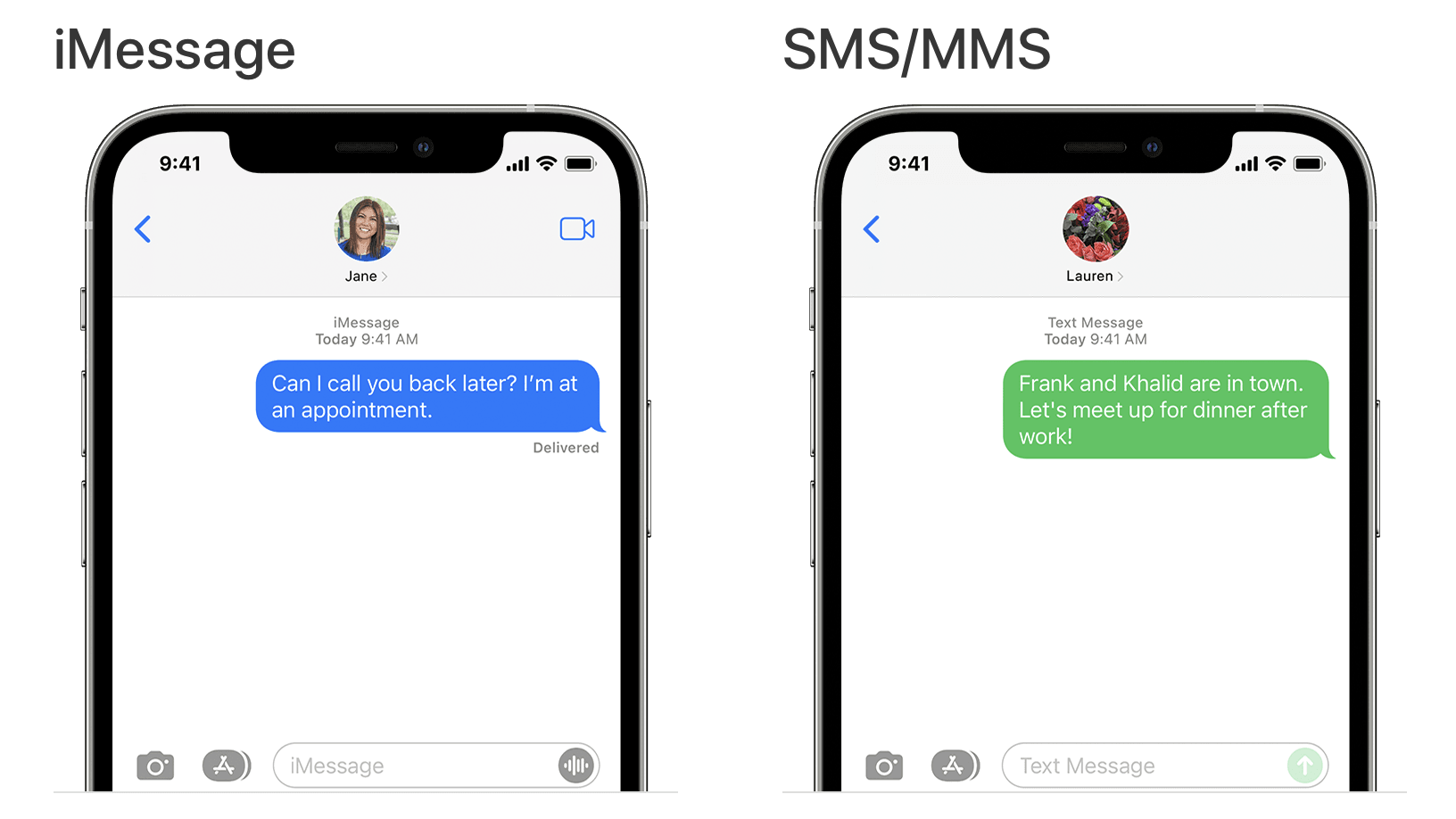
You can turn off the SMS fallback on an iPhone, in Settings > Messages. But in this case, you won’t be able to send text messages to non-Apple device users. And if you’re ever stuck in the wilderness and you can’t get a cell signal strong enough send an iMessage, you’ll likely need to manually re-enable SMS fallback if you want to send someone a text message.
Because SMS is so simple, it can be used for a wide range of purposes on countless devices. You don’t need a data plan to send SMSes; any phone plan allows you to communicate this way. This means that SMS can be used for simple devices that don’t use any other form of communication.
SMS is also the background of the Advanced Mobile Location (or AML) service, which is used to make emergency calls from a phone, and to record the locations of people who make such calls. The EU has mandated that AML be available on all mobile phones, and other countries are following.
SMS and IoT
Estimates suggest that, by 2025, there will be more than 27 billion IoT (Internet of things) edge devices around the world, many of which use SMS to communicate. Most of these devices are simple sensors that send small amounts of data to cloud servers, often on a regular schedule.
Using SMS is the most efficient way to do this, because it doesn’t rely on a data connection. Even in remote areas, they can send simple data via phone networks in text form, such as temperature readings, motion detection alerts, or utility meter readings.
Similarly, SMS is also used to wake up remote devices, such as wildlife cameras. And SMS is even used on devices like pet trackers or car trackers, to send location information from the GPS element of the tracker.
Why is SMS insecure? Should you use it for 2FA?
As I mentioned earlier, SMS is a bit like email. A message is sent from a device, it transits through a server, and it gets forwarded to a recipient’s device. Like e-mail, SMS is not end-to-end encrypted; the message may remain stored on a server for some time, allowing bad actors to read it at a later date.
There are a number of attack scenarios that can allow a malicious party to obtain SMSes that are intended for someone else. Methods include—but are not limited to—SIM swap scams, SIM cloning attacks, IMSI catcher (“fake cell tower”) attacks, and other man-in-the-middle (MITM) attacks. In some scenarios, a nefarious person can intercept SMS messages and receive (or listen in on) phone calls intended for the victim, without the victim’s knowledge.
For all of these reasons, it’s inherently insecure to use SMS for two-factor authentication (2FA; i.e. those six-digit codes you enter to confirm your identity when logging into websites). If your only 2FA option for a service is receiving codes over SMS, it’s usually* better than not having any 2FA at all. But if you have other options such as using passkeys, physical security keys, a trusted authenticator app, or even receiving a one-time passcode via WhatsApp, your accounts will be much more secure if you choose those options instead of SMS.
*The one caveat is that some services, if a user forgets their password—or an attacker who claims to be the user doesn’t know the password—may fall back to SMS as the only factor. This is a poor practice, because in such cases simply intercepting a text message could be all it takes to hack into an account. Before enabling SMS-based 2FA, make sure you know exactly how a service will use SMS with regards to account recovery.
What is RCS? Will Apple ever adopt it?
Android devices support a technology called Rich Communication Services—RCS for short. If you use the Google Messages app on an Android phone, it now defaults to offering end-to-end encryption for texts between Android users (as long as both phones are on carrier networks that support RCS).
It’s not available in every country. Some repressive or totalitarian regimes may reject adopting RCS, preferring to surveil their citizens more easily by monitoring unencrypted SMS messages.
RCS is similar to Apple’s iMessage in a few ways; both work over Wi-Fi or a mobile data plan, and both are end-to-end encrypted. Also, both are essentially siloed to their respective platforms; Android users can text each other over RCS, and iPhone users can text each other over iMessage.
Apple won’t license its iMessage technology to Google to implement in Android. This is actually pretty understandable for a variety of reasons; for one thing, iMessage uses a lot of proprietary technologies that are heavily integrated with iOS and iPhones, so some features would simply be unavailable to Android users anyway.
But for whatever reason, Apple has also refused to add RCS compatibility to its Messages app. Last year, Google launched a public campaign begging Apple to adopt RCS, but Apple has completely ignored Google’s pleas. (We discussed this on episode 252 of the Intego Mac Podcast.)
So, for now, iPhone-to-Android and Android-to-iPhone texting—including group messages initiated on an iPhone if at least one group member has an Android phone—will continue to rely on the outdated and insecure SMS and MMS standards. That is, if everyone relies on using the built-in messaging apps that come with their phones; there’s always the alternative to get everyone in a group to install WhatsApp, for example, and use it instead.
What is the future of SMS?
Because of its ubiquity, its widespread use on IoT edge devices, and the fact that it doesn’t require a data plan (and to a lesser degree, because of Apple’s refusal to adopt RCS or open up iMessage), SMS is not going away anytime soon.
The main weakness of SMS is its lack of encryption. This means that sending any sensitive information via SMS is risky, because it could be intercepted. Therefore, it’s preferable to send sensitive or private information over an end-to-end encrypted messaging service. But for basic text messaging needs, SMS can still be a useful tool.
How can I learn more?
It’s a good idea to use an end-to-end encrypted secure messaging solution when possible, rather than SMS. Check out our article covering the most popular secure messaging apps.
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()