What is credential stuffing? Why you need unique passwords
Posted on
by
Kirk McElhearn
 One of the most serious Internet security risks involves usernames and passwords—and the reuse of passwords across multiple sites. The best practice is to use a different password on every website or with every service where you have an account. While it’s okay to reuse the same user name (which is sometimes your email address), passwords should always be unique because of data breaches and credential stuffing.
One of the most serious Internet security risks involves usernames and passwords—and the reuse of passwords across multiple sites. The best practice is to use a different password on every website or with every service where you have an account. While it’s okay to reuse the same user name (which is sometimes your email address), passwords should always be unique because of data breaches and credential stuffing.
Why must every site password be unique?
There are often data breaches where companies have not stored data such as usernames and passwords securely. This data becomes public knowledge, and it could contain your username and password for certain sites. One website that tracks the publicly available data from this type of breach, Have I Been Pwned, currently has records for 7.8 billion accounts. (On this site, you can enter your email address or any usernames you have used to see if your credentials have been compromised.)
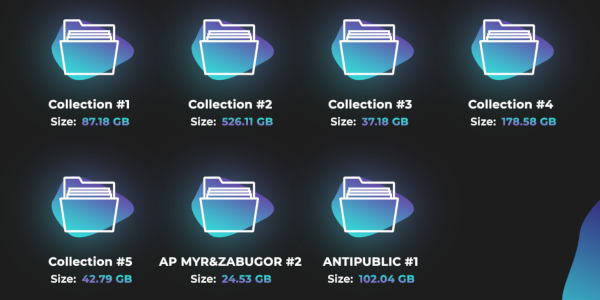
Massive collections of stolen passwords are freely available online.
When this type of data becomes available, hackers and cybercriminals perform credential stuffing attacks, using stolen usernames and passwords to attempt to log into various other accounts: these may be bank accounts, email accounts, and services such as Facebook, Twitter, or Instagram. They do so by simply trying the many combinations that they have discovered: they automate the entry of a username and password until they find that combo being used on other sites.
I have nothing to hide. Why should I care if hackers break into my accounts?
 Since credential stuffing is an automated process, it doesn’t take much effort for a cybercriminal to build a portfolio of hacked accounts. They can then use those hacked accounts to do things like send spam, or try to trick your friends, relatives, and coworkers into (for example) thinking you’re stranded overseas and need you to wire them money.
Since credential stuffing is an automated process, it doesn’t take much effort for a cybercriminal to build a portfolio of hacked accounts. They can then use those hacked accounts to do things like send spam, or try to trick your friends, relatives, and coworkers into (for example) thinking you’re stranded overseas and need you to wire them money.
Remember that if a hacker knows your password, in many cases they can change your password and lock you out (and lock out other hackers), so you may never be able to regain access to your account. That can be a major inconvenience, especially if they break into your e-mail account (because then they could take advantage of “forgot my password” links to break into the rest of your accounts) or a banking or other sensitive account.
How can I protect my accounts from credential stuffing attacks?
 The number-one way to protect against credential stuffing is to ensure that you use a unique strong password for every different site and service. This should be the default way you set up your accounts. And wherever possible, enable two-factor authentication for an additional layer of security.
The number-one way to protect against credential stuffing is to ensure that you use a unique strong password for every different site and service. This should be the default way you set up your accounts. And wherever possible, enable two-factor authentication for an additional layer of security.
If you do currently use the same password on multiple websites, we strongly recommend that you change your password on every website where it is used.
And since that likely means you’ll have a lot of unique passwords, the best way to keep track of them is to use a trusted password manager (secured by a long, strong password that only you know and will remember).
How can I learn more?
Check out our related articles with additional information on these topics:
- How to avoid getting hacked after data breaches
- Two-factor authentication: How it works and why you should use it
- How to choose the right password manager for you
- How to choose and answer security questions
 Every week, Intego’s experts discuss Apple security on the Intego Mac Podcast—we discuss credential stuffing in episode 81—so be sure to subscribe to make sure you don’t miss the latest episode. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
Every week, Intego’s experts discuss Apple security on the Intego Mac Podcast—we discuss credential stuffing in episode 81—so be sure to subscribe to make sure you don’t miss the latest episode. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
You can also follow Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).
Image of girl holding “change your password” sign based on Wikipe-tan holding sign cropped by Kasuga~enwiki (CC BY-SA 3.0).