Security & Privacy + Security News
TrueCrypt Has Been Audited! Should You Use It?
Posted on
by
Joshua Long
Close to a year ago, I wrote an article entitled “TrueCrypt is Dead; What Does This Mean for Mac Users?” after the developers of the source-available* disk encryption software abruptly terminated the project.
It might surprise readers, then, to see recent headlines about the second phase of TrueCrypt’s security audit having been completed. What’s the point of auditing software that’s no longer being developed? Is TrueCrypt really dead?
Let’s address the second question first. The short answer is that, yes, TrueCrypt itself is dead in the sense that it’s not being developed anymore by its original creators.
It is extremely unlikely that there will ever be another official version of the software under the trademarked TrueCrypt name (and if one should ever surface, it would be viewed with such intense skepticism after last year’s brouhaha that very few people would likely use it).
But some people view TrueCrypt’s demise more positively: “TrueCrypt is dead; long live TrueCrypt.”
Long live TrueCrypt?
 One subset of those people includes the die-hard believers in TrueCrypt who continue to view it as the best software of its kind, in spite of public concerns about its security. Some still prefer it over Microsoft and Apple’s built-in full-disk encryption alternatives (e.g. Windows’ BitLocker and OS X’s FileVault 2, respectively; more about the latter later) due to paranoia about whether these major U.S.-based corporations may be beholden to—or compromised by—the government or intelligence agencies such as the NSA.
One subset of those people includes the die-hard believers in TrueCrypt who continue to view it as the best software of its kind, in spite of public concerns about its security. Some still prefer it over Microsoft and Apple’s built-in full-disk encryption alternatives (e.g. Windows’ BitLocker and OS X’s FileVault 2, respectively; more about the latter later) due to paranoia about whether these major U.S.-based corporations may be beholden to—or compromised by—the government or intelligence agencies such as the NSA.
Still others continue using TrueCrypt for its unique features, including cross-platform encrypted disks (a feature that’s still being utilized by Amazon Web Services today), and the plausible deniability hidden operating system feature for Windows users, which allows a user who’s under duress to use an alternative boot password to log into a different operating system that doesn’t contain incriminating information.
Another subset of those still interested in TrueCrypt, and thus its ongoing security audit, are programmers who are continuing to develop TrueCrypt independent of the original creators—an undertaking which is known in the software development field as forking a project.
There has been some debate about how acceptable it is to create a public fork of the TrueCrypt codebase under its unique source code license, which threatens legal prosecution if the copyright holder feels that some part of the license was not followed precisely, and expressly forbids relicensing the software under any other license. One fork, VeraCrypt, brazenly defies this prohibition and claims that VeraCrypt is offered under both the TrueCrypt License and the Microsoft Public License. Another fork, CipherShed, is currently offered under the TrueCrypt License but intends to eventually undergo a complete code rewrite so that it can legally cut ties with that license and officially be relicensed as truly free (as in freedom) open-source software.*
Naturally, both for those who use continue using TrueCrypt 7.1a (the final full-featured version) and for those who want to develop or use a fork of TrueCrypt, it’s important to know with confidence that the software is secure and safe to use.
Is TrueCrypt secure and safe to use?
In late 2013, prior to TrueCrypt’s demise, a Canadian student was able to successfully compile the Windows version of TrueCrypt 7.1a’s source code and output the identical resulting binary that was available to download from TrueCrypt’s site, and he shared the results of how he did so. This means that if the source code is thoroughly audited and found to be safe, then one can reasonably infer that the pre-compiled software that was originally available from TrueCrypt’s site is probably safe as well (or at least the Windows version of it).
Around the same time in 2013, cryptographer and Johns Hopkins University research professor Matthew Green, and professional security researcher Kenneth White, kicked off a campaign to formally and publicly audit the TrueCrypt software, and thus the Open Crypto Audit Project (OCAP) was formed. The scope of this project was narrowed to include two phases: the first, to assess the bootloader and Windows kernel driver, and the second, “to perform a scoped engagement on portions of TrueCrypt’s cryptographic implementations and use.”
TrueCrypt audit phase 1
The first phase of the project was completed in February 2014 (with the blessing of TrueCrypt’s development team, and while TrueCrypt 7.1a was still available from the official TrueCrypt site) and was published (PDF) soon thereafter. The auditors “found no evidence of backdoors or otherwise intentionally malicious code” in the bootloader or the Windows kernel driver, and no “high-severity issues” were found, although various medium and low-severity and other potential issues were detailed in the report.
TrueCrypt audit phase 2
The second phase of the TrueCrypt audit was finally completed in March 2015 and was just published (PDF) on Thursday. Green’s “TL;DR” summary states that the “audit found no evidence of deliberate backdoors, or any severe design flaws that will make the software insecure in most instances.”
However, two “high-severity issues” were identified in the second audit (along with a low-severity issue and one of undetermined severity). The more significant of the high-severity issues, Green asserts, is that “in some extremely rare circumstances” the Windows version of TrueCrypt doesn’t properly handle cases where the Windows Cryptography API (application programming interface) fails to initialize correctly, and neglects to warn the user about this failure and proceeds anyway. Green feels that “the likelihood of such a failure is extremely low,” and that “even if the Windows Crypto API does fail on your system, [TrueCrypt] still collects entropy from sources such as system pointers and mouse movements” which he feels “are probably good enough to protect you.” Both Green and the auditors recommended that those developing forks of TrueCrypt rewrite the code to implement better checks for failures of this kind.
The second high-severity issue discovered in the second audit relates to TrueCrypt’s AES implementation being susceptible to cache-timing attacks, which Green feels “is probably not a concern unless you’re perform encryption and decryption on a shared machine [meaning a computer you share with someone else], or in an environment where the attacker can run code on your system (e.g., in a sandbox, or potentially in the browser).” The auditors offer strategies that could be used in TrueCrypt forks to partially mitigate this weakness.
Both Green’s TL;DR summary and the second audit’s Findings Summary seem positive overall with regards to the security of the audited portions of TrueCrypt. The auditors state that none of the four total issues they identified in the second audit “led to a complete bypass of confidentiality in common usage scenarios,” and also state that “the standard workflow of creating a volume and making use of it was reviewed, and no significant flaws were found that would impact it.”
What about Mac OS X and Linux versions?

With these two audits completed, the status at the top of the official audit site IsTrueCryptAuditedYet.com has been changed to a resounding “Yes!”—but much more work could be done to throughly audit TrueCrypt. The Mac and Linux versions have not been a focus to date, and there are many other potential areas of focus specified in the Project Goals and Scope sections of the audit reports. An extremely thorough audit of all components and uses of TrueCrypt would be nice, but it would also be extremely expensive. The homepage of the Open Crypto Audit Project states, “pending an executive summary, TrueCrypt is Audited,” which seems to imply that the two audits completed thus far are the only ones that the OCAP plans to spearhead for the time being.
So, should you use TrueCrypt or one of its offshoots? We’ll leave that as an exercise for you, the reader, to decide after examining the available evidence, but if you need to share encrypted disk images or external drives with someone who uses Windows or Linux, then it’s probably a decent solution for your use case.
Apple’s built-in full-disk encryption alternatives

However, if your goal is to encrypt your Mac’s boot drive, and assuming you trust Apple (and you probably do if you’re using a Mac), then you’ll probably want to use the Apple-supported whole-disk encryption solution that’s built right into your operating system: FileVault 2.
How to use FileVault 2
FileVault 2 (which is different from the original FileVault built into Mac OS X v10.6 Snow Leopard that merely encrypts a user’s home folder while leaving the rest the disk unencrypted, including memory swap files) is really easy to enable if you’re not already using it (and you might be, especially if you’ve upgraded to Yosemite). Just click on the Apple menu, select System Preferences…, click on Security & Privacy, and then click on FileVault.
If you haven’t already enabled the feature, then you’ll see a button labeled Turn On FileVault (note that you may need to first click on the lock icon and enter your administrator password, if prompted, before you can click on the Turn On FileVault button). After clicking on that button, OS X will walk you through the process of encrypting your Mac’s hard drive. For more information about using FileVault 2, you can review the Apple support article entitled “OS X: About FileVault 2.”
How to use Disk Utility
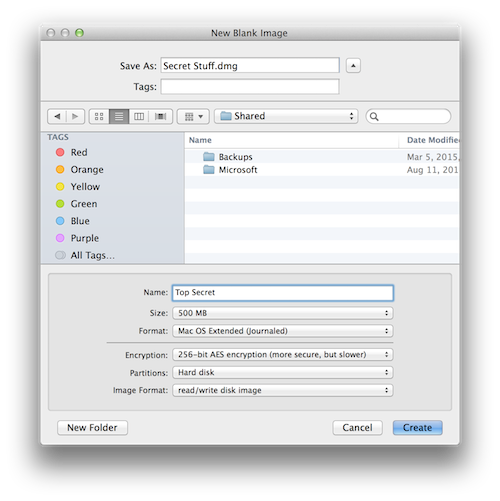
If you just want to create an encrypted, portable disk image that you only plan to use on Macs, you can do that with Apple’s Disk Utility application, which is also part of OS X. You can find it by opening Macintosh HD, then the Applications folder, then the Utilities folder (or simply click on the Spotlight magnifying glass in the upper-right corner of your screen and start typing Disk Utility). We’ve previously explained how to make an encrypted disk image from an existing folder, but you may not know that you can also create a new disk image of just about any size by clicking on the File menu, selecting New and then Blank Disk Image…, and then selecting the disk size, encryption format, and other options, as seen in this screenshot:
But hey, if you have a desire to use TrueCrypt instead of some alternative solution, at least now you know that TrueCrypt has been audited and is therefore safe to use.
…Probably.
*Technically, TrueCrypt is more accurately referred to as “source-available” rather than “open-source” software; the TrueCrypt license is somewhat restrictive and is not recognized by the Free Software Foundation or the Open Source Initiative.