Malware + Recommended + Security News
New Malware Underscores the Danger of Assumed Mac Security
Posted on
by
Jay Vrijenhoek
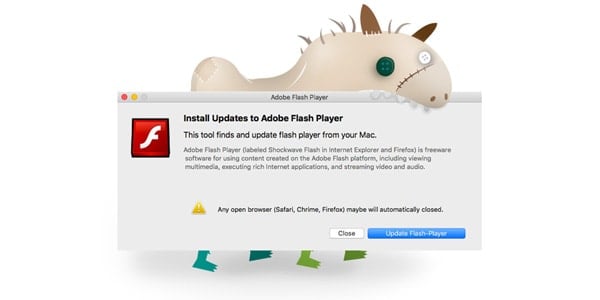
This week researchers found a piece of malware in the wild, built to steal passwords from the macOS keychain. Named “MacDownloader” and posing as, what else, a fake Flash Player update, the new malware was found on the Mac of a human rights advocate and believed to originate from Iran. The malware’s code is very sloppy and appears to have been made by an amateur who took pieces of other’s code and repurposed them.
The threat report mentions the following:
MacDownloader seems to be poorly developed and created towards the end of 2016, potentially a first attempt from an amateur developer. In multiple cases, the code used has been copied from elsewhere. The simple activity of downloading the remote file appears to have been sourced from a cheat sheet. The main purpose of MacDownloader seems to be to perform an initial profiling of the infected system and collection of credentials from macOS’s Keychain password manager – which mirrors the focus of Windows malware developed by the same actors.
At this time, it appears the malware is not a threat and the Command & Control server has been taken down. Intego VirusBarrier offers protection from this malware, detected as OSX/MacDownloader.
Malware payload
Security researchers found that this malware was originally designed as a fake Bitdefender antivirus, but was later repackaged as a fake Flash Player update. Once installed, the malware attempts to achieve persistence by use of a poorly implemented shell script, which at the time of writing did not function due to the C&C server being offline.
How MacDownloader tricks Mac users

MacDownloader displays a fake Flash Player update that offers an “Update Flash-Player” button and a “Close” button. Unlike other malware of its kind, clicking the Close button actually exists the installer and nothing malicious is placed on the system. If the Update button is clicked though, a malware dialog will pop-up, which is, of course, fake as well.
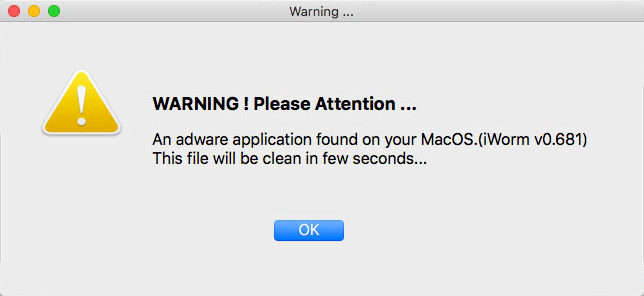
These dialogues are also rife with basic typos and grammatical errors, indicating that the developer paid little attention to quality control.
After a user clicks on OK, the software mimics the System Preferences to request the admin password in order to grab more info on the system. If the user enters their password and clicks OK, the software grabs the info, and then it tries to open a remote connection to:
connect to 46.17.97.37 on TCP port 80 (http) IP Address 46.17.97.37 Reverse DNS Name No Reverse Name Established by /Users/intego/Desktop/addone flashplayer.app/Contents/MacOS/Bitdefender Adware Removal Tool Process ID 1228 User intego (UID: 501)
MacDownloader collects user keychain information and uploads it to said C&C server, including documents the running processes, installed applications and the username and password, which are acquired through a fake System Preferences dialog.
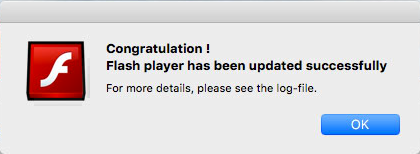
The name and password, which in almost all cases are Administrator credentials, give the malware everything it needs to access the keychain information. With access to the keychain the sky is the limit, because email account passwords, social network account details, and much more, are all stored in the keychain. (More than enough information for identity theft!) With all the information collected and sent to their server, a dialog is displayed showing the Flash Player update was completed. Of course, no Flash Player was ever installed or updated.
The researchers also made an interesting observation:
While Windows remains the dominant operating system in the world, many communities have shifted over to macOS in the interest of security and stability. However, much of the added security afforded to macOS users stems from an expectation of Windows by attackers and less readily-available remote access tools for the OS, rather than better in-built defenses. Thus, macOS users are at risk of assuming greater protection against malware than actually exists, and could be more vulnerable as a result. One of these communities is the human rights community, especially those focused on Iran, which based on anecdotal experience is strongly dependent on Apple devices.
Translation: the notion that people who are drawn to Macs “in the interest of security,” coupled with an inherent belief that Macs offer “greater protection against malware than actually exists,” leads to an interesting target group for state sponsors of hacking.
Still alive: myths about malware in general, but Macs especially
Could it be true? Is the old myth that Macs are safer than Windows machines, straight out of the box, still alive?
I was first introduced to Mac in 1996 and got my first Mac at home in 1998. Back then, the mantras “there are no viruses for Mac” and “Mac is more secure than Windows,” among others, were accepted as simple truth. By all means, download anything, insert any CD or ZIP drive, because nothing bad can happen, you’re on a Mac! Today, over two decades later, a lot of Mac users still think these “truths” apply. As the researchers pointed out, there are communities that moved to Mac, because they feel it offers them greater protection. This goes for businesses and consumers as well.
If you’ve been reading The Mac Security Blog for a while, you are well aware there are plenty of malware for the Mac, and these are not the only threats that can affect Mac users. For example, using unsecured Wi-Fi can get your information intercepted, whether you use a Mac or a PC. Not using a firewall can get you hacked, whether you use a Mac or a PC. And just this week another Mac threat was found in the form of a Microsoft Office Word macro, more info on that here.
Even on a Mac it’s important to be security minded. This means using layered security such as a firewall and antivirus solution. This also means hardening your macOS installation itself and using best practices when using open Wi-Fi or when using your Mac in a shared environment.
While there are not nearly as many threats out there for Mac as there are for Windows, there is enough to put you at risk. Every year as Mac market share goes up, it becomes more interesting and potentially profitable for malware authors to focus on Mac. Targeted attacks through phishing or social engineering to a Mac user or small group of users (a business for example) will typically go undetected for much longer, increasing the chances of payout. Whether payout means the successful theft of user data or ransomware, the longer the malware can stay active and undetected, the better.
And, for Pete’s sake, please don’t assume your Mac offers greater protection from malware than actually exists, or you could be more vulnerable as a result.