Month in Review: Apple Security in March 2017
Posted on
by
Joshua Long

Last month, February, was a doozy with several reports of Mac malware in the wild. What notable security events have happened in March 2017 that impact users of Macs, iPhones, iPads, and other Apple devices? Read on to find out.
Mac Hackers Get Root at Pwn2Own
 Each year at the CanSecWest security conference, hackers compete for cash prizes and geek cred in the Pwn2Own hacking competition. Zero-day vulnerabilities exploited during the contest are disclosed to the vendors, so bugs get fixed and end users ultimately benefit from increased security.
Each year at the CanSecWest security conference, hackers compete for cash prizes and geek cred in the Pwn2Own hacking competition. Zero-day vulnerabilities exploited during the contest are disclosed to the vendors, so bugs get fixed and end users ultimately benefit from increased security.
On the first day of Pwn2Own, researchers Samuel Groß and Niklas Baumstark chained together multiple exploits to “get root” (obtain full administrator privileges) on a MacBook Pro. They earned style points by displaying “pwned by niklasb & saelo” across the Touch Bar.
Awesome pwnage with @_niklasb #pwn2own 🙂 pic.twitter.com/Zk0empswbW
— Samuel Groß (@5aelo) March 15, 2017
(As a fun aside, back in 2010 I interviewed four-time Pwn2Own winner Charlie Miller about Mac security and fuzzing after his third-year victory.)
Apple Denies Alleged iCloud Breach; Refuses Ransom
 Vice’s Motherboard blog reports that a group calling itself “Turkish Crime Family” has demanded that Apple pay a ransom of $75,000 in cryptocurrency or $100,000 in iTunes gift cards to prevent a mass attack on iCloud users.
Vice’s Motherboard blog reports that a group calling itself “Turkish Crime Family” has demanded that Apple pay a ransom of $75,000 in cryptocurrency or $100,000 in iTunes gift cards to prevent a mass attack on iCloud users.
The extortionists, who threaten to remotely wipe Apple devices and reset iCloud accounts if Apple has not paid them by April 7, claim to have access to as many as 559 million accounts including some with @icloud.com and @me.com domains.
Apple claims that there has not been a breach of iCloud or Apple ID systems, and that the extortionists’ list of e-mail addresses and passwords appears to have come from previous attacks on third-party services. Apple told Motherboard:
“We’re actively monitoring to prevent unauthorized access to user accounts and are working with law enforcement to identify the criminals involved.
“To protect against these type of attacks, we always recommend that users always use strong passwords, not use those same passwords across sites and turn on two-factor authentication.”
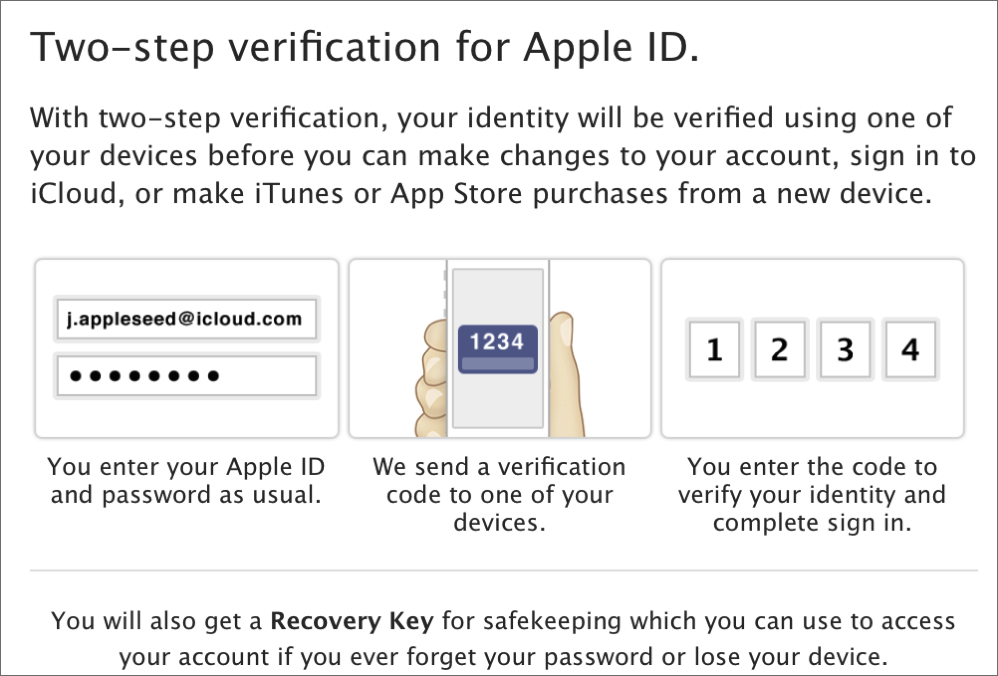
Enabling two-step verification for your Apple ID is a good safety precaution.
We offer the same advice about not reusing passwords across multiple sites. If you may have used your Apple ID or iCloud account password on another site in the past, change your password as a precaution, and be sure to use one that’s unique and hasn’t been used elsewhere. And yes, definitely enable two-step authentication; adding “something you have” to your sign-in process can make it significantly more difficult for an attacker to breach your account.
WikiLeaks’ Vault 7 and DarkMatter Disclosures
 WikiLeaks has recently made waves with a series of alleged leaks of U.S. Central Intelligence Agency documents, collectively dubbed “Vault 7.” The alleged leaks contain documents, which date from 2012 to 2016 according to security expert Bruce Schneier’s report, that include details of both previously known and new attacks on software and hardware platforms of companies such as Apple, Cisco, Google, Microsoft, and Samsung—some of which were supposedly used by the CIA a decade or longer ago.
WikiLeaks has recently made waves with a series of alleged leaks of U.S. Central Intelligence Agency documents, collectively dubbed “Vault 7.” The alleged leaks contain documents, which date from 2012 to 2016 according to security expert Bruce Schneier’s report, that include details of both previously known and new attacks on software and hardware platforms of companies such as Apple, Cisco, Google, Microsoft, and Samsung—some of which were supposedly used by the CIA a decade or longer ago.
Motherboard reports that WikiLeaks has been in touch with Apple, Google, and Microsoft with an offer to share the details of several vulnerabilities disclosed in Vault 7. According to Motherboard, WikiLeaks would only disclose the details to Apple and other companies if they would promise to patch the vulnerabilities within 90 days.
A Microsoft spokesperson confirmed that Microsoft had been contacted, but Apple and Google have neither commented on Motherboard’s inquiry nor a follow-up inquiry from Forbes. However, BuzzFeed reported earlier this month that Apple had stated that “many of the issues leaked [on the first day of Vault 7] were already patched in the latest iOS,” and that Apple would “continue to work to rapidly address any identified vulnerabilities.”
Here’s Apple’s statement on iOS-related stuff in the WikiLeaks CIA data dump. pic.twitter.com/QiAWx8ZXpT
— John Paczkowski (@JohnPaczkowski) March 8, 2017
Forbes reported this week on a Vault 7 update that WikiLeaks is calling “DarkMatter,” which alleges that the CIA has been targeting the iPhone since a year after Apple debuted its groundbreaking smartphone. The CIA was allegedly developing rootkit malware called NightSkies in 2008, which Forbes indicates would have given the CIA complete control over a compromised iPhone.
There was also allegedly a version of NightSkies in development that targeted Macs, as well as a way to combine multiple attacks to embed persistent rootkit malware into the EFI firmware and operating system.

One alleged CIA trick from 2012 called “Sonic Screwdriver” is similar to Thunderstrike and Thunderstrike 2, which Apple partially mitigated years ago in 2014 with OS X 10.10.2 and in 2015 with 10.10.4.
As noted by 9to5Mac, security researcher Will Strafach believes that the vulnerabilities in the DarkMatter release have largely been fixed, and that end users need not worry.
I truly hope it goes without saying, but if not: I have verified that the new release contains nothing of concern. most things are ancient. https://t.co/0JSSc0UgF0
— Will Strafach (@chronic) March 23, 2017
Apple Hires Jonathan Zdziarski

Credit: Zdziarski’s blog
Earlier this month, leading iOS security expert Jonathan Zdziarski announced that he had accepted a position with Apple’s Security Engineering and Architecture team. On his acceptance of the position, Zdziarski commented:
“Privacy is sacred; our digital lives can reveal so much about us – our interests, our deepest thoughts, and even who we love. I am thrilled to be working with such an exceptional group of people who share a passion to protect that.”
Although it could certainly benefit Apple and its customers to have Zdziarski as part of Apple’s security team, AppleInsider notes that this also likely means that the researcher will reveal little about iOS security on his blog while employed by Apple.
It appears that Zdziarski has deleted his Twitter account.
Unpatched Vulnerability in Adium IM Client
 The Register reports that Adium, a multi-protocol instant messaging app for macOS, contains an outdated and vulnerable version of the libpurple library.
The Register reports that Adium, a multi-protocol instant messaging app for macOS, contains an outdated and vulnerable version of the libpurple library.
Users of Adium are advised to discontinue using the software until version 1.5.10.3 is released to address the vulnerability.
ICYMI: RSA Conference 2017 Highlights
 In February’s update, we mentioned that RSAC 2017 coverage was coming soon. In case you missed it, you can check it out here:
In February’s update, we mentioned that RSAC 2017 coverage was coming soon. In case you missed it, you can check it out here:
Stay Tuned! Subscribe to The Mac Security Blog
There’s more to come. Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month.
If you missed Intego’s other recent Apple security news roundups for 2017, you can check them out here: