Security & Privacy + Security News
OS X 10.10.2 Update Released – Fixing Thunderstrike and other Security Vulnerabilities
Posted on
by
Graham Cluley

Apple has released the latest update to OS X Yosemite, 10.10.2, fixing a number of issues—including some serious security vulnerabilities.
The first time that most Mac users will know about the update is when they find it nestled amongst their other updates in the App Store—and at first you may not realise the seriousness of the security issues it aims to fix, because they are hidden beneath a host of other fixes:
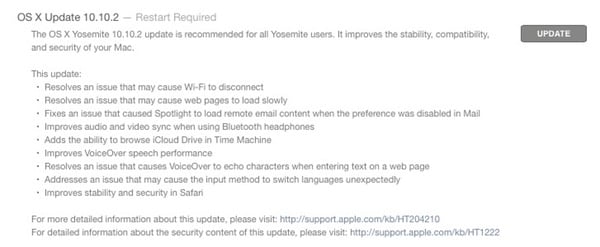
This update addresses the following:
- Resolves an issue that might cause Wi-Fi to disconnect
- Resolves an issue that might cause web pages to load slowly
- Fixes an issue that could cause Spotlight to load remote email content when this preference is disabled in Mail
- Improves audio and video sync when using Bluetooth headphones
- Adds the ability to browse iCloud Drive in Time Machine
- Improves VoiceOver speech performance
- Resolves an issue that could cause VoiceOver to echo characters when entering text on a web page
- Addresses an issue that could cause the input method to switch languages unexpectedly
- Improves stability and security in Safari
What’s most interesting to readers of this site, however, are the security fixes in this update to OS X, detailed—as usual—on Apple’s security updates webpage.
There you will find details of numerous security fixes—some serious and some not-so-serious—that are reportedly resolved by OS X 10.10.2.
Included amongst them are the three security flaws that Google controversially disclosed to the public, without waiting for Apple to roll out a patch.
Google privately informed Apple of these vulnerabilities in October and granted a 90-day grace period to resolve them. That grace period expired last week, with Google not only publishing details of flaws in OS X, but also proof-of-concept code that could potentially be used by attackers.
Thankfully now patches are available for those publicly-disclosed flaws.
Thunderstrike
And we should also give thanks that included in the OS X 10.10.2’s security fixes is what appears to be a patch for a potentially very serious vulnerability known as Thunderstrike.

Thunderstrike first became a hot topic at the end of last year when security researcher Trammel Hudson told the Chaos Communication Congress (31C3) conference in Hamburg about the new vulnerability he had discovered.
The vulnerability was named “Thunderstrike,” not only because hackers could exploit the Mac Thunderbolt port to install code using it, but also because (in Hudson’s words), “all exploits have cool names these days.”
What makes Thunderstrike particularly worrying is that it could install malware onto the ROM EFI boot chip on Macs and MacBooks, exploiting security loopholes to waltz past Apple’s built-in security measures that are supposed to prevent unauthorised firmware updates.
Once in place, a malicious rootkit could effectively “act invisible,” making itself impossible to detect through anti-virus software because it is running at such a low level—from the very instant a Mac is turned on—and capable of offering a clean, uninfected image of the boot chip to any service which interrogates it.
 One possible infection scenario is that you could visit a hotel, pop down to have breakfast and leave your laptop unattended. While you are away gorging yourself on hash browns and sausages, an “evil maid” has plugged a device into your Thunderbolt drive and reflashed your computer’s boot ROM.
One possible infection scenario is that you could visit a hotel, pop down to have breakfast and leave your laptop unattended. While you are away gorging yourself on hash browns and sausages, an “evil maid” has plugged a device into your Thunderbolt drive and reflashed your computer’s boot ROM.
And they didn’t need to know your password to do it.
Once in place, malware could steal information or spy on your activities.
To add insult to injury, a malicious Thunderstrike attack could avoid being removed by firmware-flashing software, forcing an expensive hardware fix.
In a word: nasty.
So, if I were you, I would strongly consider installing Apple’s OS X 10.10.2 update at your earliest opportunity. Obviously—as with any OS update—it does no harm at all to backup your systems first, just in case the new version throws up some unpleasant issues or incompatibilities.
But, for most people running Yosemite, OS X 10.10.2 couldn’t have come at a moment too soon and should be installed post haste.