iOS Malware ‘Xsser mRAT’ Targets Jailbroken iOS Devices
Posted on
by
Derek Erwin
It’s the big security news of the day. Security researchers have uncovered new iOS malware, called Xsser mRAT, which specifically targets iOS devices, and was originally targeted at Android devices.
The cross-platform attack involves both iOS and Android, targeting Hong Kong protesters, according to reports.
Lacoon Mobile Security discovered the malware while investigating similar malware for Google’s Android operating system that also targets Hong Kong protesters, and they have dubbed Xsser mRAT the “first and most advanced, fully operational Chinese iOS trojan found to date.”
But should iOS users be running to the hills in panic over Xsser mRAT?
For the majority of iOS users, your iPhone or iPad is simply not at risk of infection, because the Xsser mRAT can only be installed on jailbroken iOS devices.
What we know about Xsser mRAT
The exact way Xsser malware ended up on iOS devices has yet to be uncovered, although it is likely to have been spread as a fake app pretending to help Hong Kong protesters meet.
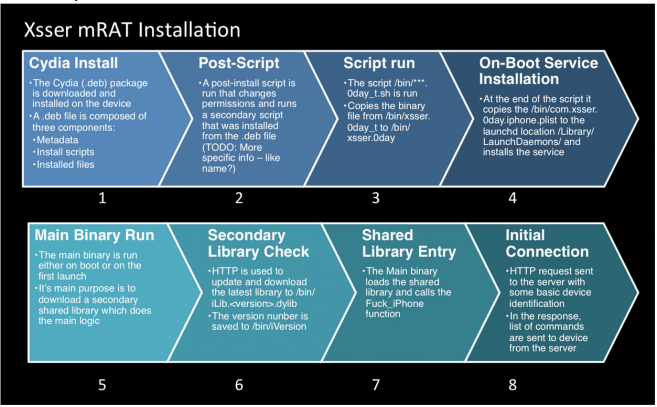
Xsser mRAT is a trojan, which means it requires installation of an infected package containing the malware to be installed on jailbroken iOS devices.
If installed, the trojan can operate in the background of a victims’ phone, and contents of the targeted device are sent to remote servers that appear to be controlled by a foreign government or organization. Xsser mRAT can steal SMS messages, call logs, location data, photos, address books, data from the Chinese messaging application Tencent and passwords from the iOS keychain, wrote Lacoon.
Even if the victim turns off their iPhone or iPad, the malware is not disabled, and researchers say that it reboots on start-up, as well as updating and sending back information automatically.
The full extent of how Xsser mRAT is being used is currently unknown. It is also unclear how the Xsser trojan would get onto a jailbroken iPhone, because at the moment the only known way for a victim to get the malware is to manually add the trojan’s source repository in Cydia, the jailbreak alternative to the App Store. If it is already in other packages as a trojan, it has yet to be identified.
How to protect yourself
One of the key benefits of running iOS instead of Android is the secure design of iOS. Purchasing an iPhone and jailbreaking it eliminates this major benefit, and it isn’t much different than running a Windows computer with no security software installed. Therefore, the most surefire method of protection is to not jailbreak your iPhone or iPad.
We have stressed this in the past, and now is a better time than ever to remind you: if you want to stop government spyware, don’t jailbreak your iPhone! And if you’re considering doing so, you should proceed with extreme caution. An iPhone that isn’t jailbroken is the safest way to prevent iOS malware infection.
If you have already jailbroken your iPhone, you have effectively taken out much of the security that Apple built into iOS in the first place, to protect users from nastiness and misbehaving apps. (Which leads us to ponder, if you’re going to jailbreak your iPhone, why did you bother getting one?)
Do you install apps that were not received from the App Store? If you think it is worth the risk, you should be super-careful about where you download and install applications. Just because an app claims to be one thing doesn’t mean it’s not another.