Don’t Jailbreak Your iPhone if You Want to Stop Government Spyware
Posted on
by
Graham Cluley

Normally, you can’t run whatever software you like on your iPhone.
As a corporation, Apple has something of a “controlling personality” and has locked down your iPhone and iPad to prevent you from making a wide number of changes or tweaks.
The most obvious limitation is that on a regular iPhone you can only install programs approved by Apple, and distributed via Apple’s App Store – unlike, say, the situation on your Windows PC or Apple Mac computer.
On a jailbroken iPhone, however, you can shop for apps anywhere on the net, not just the official App Store.
So, should you jailbreak your iPhone? Well, from the security point of view, I’d recommend that if you’re thinking of jailbreaking you should proceed with caution, as two recent news stories demonstrate:
Firstly, surveillance companies love jailbroken iPhones.
Last week, news emerged that a company called Gamma International, which develops commercial network intrusion malware for the purposes of surveillance and sells it to governments around the world, had been hacked.
Gamma International has something of a notorious reputation over concerns that its software may have ended up in the hands of oppressive regimes, and that the company had no qualms about disguising its FinFisher spyware as bogus versions of the Firefox web browser.
According to Gamma International sales documents leaked by the hackers, FinFisher (also known as FinSpy) has no difficulties running on Androids and Blackberrys, but if it is up against a regular, non-jailbroken iPhone – it’s powerless.
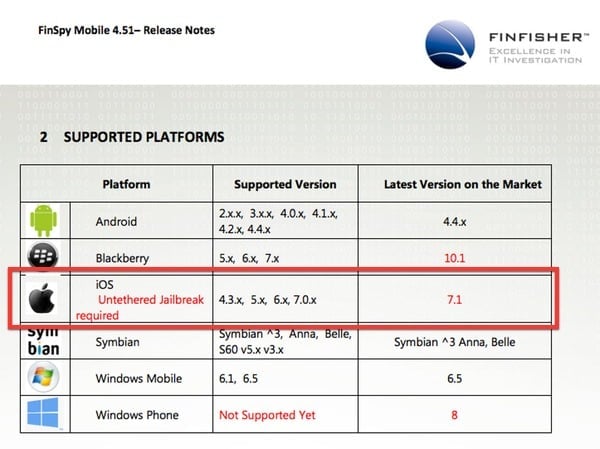
iOS: Untethered jailbreak required
So, if a government agent wants to listen in to the Skype calls you make, or track your location, or read files and steal phone numbers from your iPhone, they’ll have their fingers crossed that you have jailbroken it – otherwise they’re going to have to find a different way of spying on you and your activity than using FinFisher.

The reason is that jailbreaking rips out much of the security that Apple built into iOS in the first place, to protect users from nastiness and misbehaving apps. Whereas with other popular smartphone operating systems, FinFisher can be installed and activated relatively easily – it’s a lot harder with the iPhone.
Secondly, Chinese malware gangs make money out of jailbroken iPhones.
This week brings another warning for those considering jailbreaking their iDevices.
As Virus Bulletin reports, security researcher Axelle Apvrille has uncovered that some 75,000 jailbroken iPhones have been infected by malware known as iOS/AdThief.
The malicious code, written by a Chinese hacker calling themselves Rover12421, hijacks revenue from 15 different adkits, meaning that cash ends up in the pockets of criminals rather than the makers of the ad-funded apps themselves.
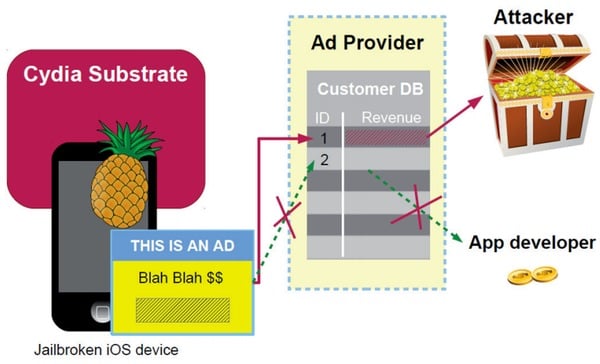
“With 75,000 infected devices, iOS/AdThief is not extremely prevalent,” wrote Apvrille. “However, there are an estimated 22 million hijacked ads, so the malware has probably had a fair amount of impact and generated significant revenue for the owner(s).”
Apvrille is right not to send owners of jailbroken iPhones running to the hills in panic. The threat should be put in proportion. Although there are clearly more risks associated with having a jailbroken iPhone compared to an un-meddled iDevice, there is still remarkably little malware written for the iOS operating system – particularly when compared to the huge problem that exists on Android.
Should you jailbreak your iPhone?
Personally, I think the typical smartphone user is safer with an iPhone than an Android, but an iPhone that isn’t jailbroken is safest of all from the malware point of view.
Yes, you might be able to do some cool things which Apple doesn’t want you to do with a jailbroken iPhone – but is it really worth the risk?