Recommended + Security & Privacy + Security News
FREAK OpenSSL Bug: What Apple Users Need to Know
Posted on
by
Derek Erwin
Security researchers have discovered a crippling OpenSSL bug in Apple and Google devices, as well as many high profile websites, which could allow “man in the middle” attacks. These attacks can occur when Apple users are on public Wi-Fi networks, where they can be fooled into connecting to rogue servers claiming to belong to someone else.
The “FREAK” vulnerability (CVE-2015-0204), short for Factoring attack on RSA-EXPORT Keys, makes it possible for attackers to decrypt and monitor HTTPS-protected traffic.
A FREAK attack is possible when someone with a vulnerable device—Mac OS X computers, iOS and Android devices—connects to an HTTPS-protected website configured to use an easily breakable key once thought to be dead. It requires that the attacker be in a position where they can intercept packets between the endpoint device and the HTTPS-protected website.
How did we get here?
The flaw resulted from a former policy of the Clinton administration, which required weak 512-bit keys to be used in any software or hardware that was exported out of the United States. The U.S. government forbade the export of strong encryption in products shipped to customers in other countries.
These restrictions were lifted in the late 1990s, but somehow the weaker encryption have managed to remain in widely used software and hardware around the world, including the United States, and went unnoticed by the public until recently.
How to tell if a website is vulnerable
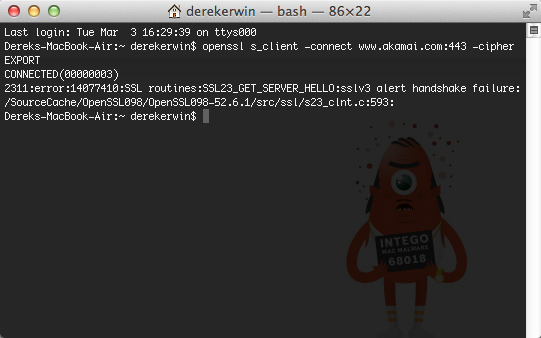
If you have a Mac OS X system, open Terminal and run this line of code:
openssl s_client -connect www.akamai.com:443 -cipher EXPORT
If it returns “alert handshake failure” in its answer, then the host site is safe.
To check if another site is safe, substitute “www.akamai.com” with another hostname.
How to tell if your browser is vulnerable
Type this web address directly into your browser address bar:
https://freakattack.com
On this page, you can see if your browser is vulnerable, and it has a list of every vulnerable website. At the time of writing this post, only Firefox is safe to use on Mac OS X (both Safari and Google Chrome are vulnerable).
Have hackers figured out how to exploit the FREAK flaw?
There is no published attack using this vulnerability, but that doesn’t mean it’s not happening. Given the age of this vulnerability, someone has probably figured out how to exploit it, at least by the NSA. However, successful exploitation is not exactly easy to accomplish without physical access to the hotspot hardware.
This means that attacks can be launched by anyone who has access to Internet traffic, which includes governments, Internet Service Providers (ISPs), coffee shops or airports, and any other locations offering Wi-Fi hotspots. A malicious hotspot owner could exploit the vulnerability, or someone spoofing the Starbucks hotspot from a nearby location. And a well-versed hacker could pull it off, but it’s really not that simple.
Dan Goodin at Ars Technica described what can happen, and said:
[A]ttackers on a coffee-shop hotspot or other unsecured network can masquerade as the official website, a coup that allows them to read or even modify data as it passes between the site and the end user.
How can the FREAK vulnerability be resolved?
Apple can patch this on the client side, and they no doubt will soon. Web server hosts can also patch this on the server side, which they no doubt are doing as well.
UPDATE: Apple Releases FREAK Fix for OS X, iOS and Apple TVs
Intego is continuing to research this threat and will continue to provide updates as new information becomes available.
What can you do to stay protected?
To stay safe on Macs, use Firefox.
On iOS devices, avoid using any public Internet access options (i.e. sitting in Starbucks or using free airport Wi-Fi) and doing things like banking and email. If you must use a public Wi-Fi hotspot, use a VPN (see Cloak as a paid option, or Onavo Protect as a free option), don’t send personal or private information if you can avoid it, and never accept any software updates.
Protect your Mac using a multi-layered approach to security: Download Intego’s award-winning Mac Premium Bundle X8.