Flashback Mac Malware Uses Twitter as Command and Control Center
Posted on
by
Peter James
The Flashback malware, which Intego pointed out was infecting an increasing number of Macs, turns out to be using a novel technique to operate. Many types of malware use command and control servers that they connect to, in order to get instructions from the creators of the malware. The problem with using these servers is that their IP addresses are specified in the malware code, and the servers can generally be taken down.
Flashback, however, uses an interesting method of getting commands: it uses Twitter. And rather than use a specific Twitter account, which can be removed, it queries Twitter for tweets containing specific hashtags. These hashtags aren’t as simple as, say, #Flashback or #MacMalwareMaster, but are seemingly random strings of characters that change each day. Intego’s malware research team cracked the 128-bit RC4 encryption used for Flashback’s code and discovered the keys to this system.
The hashtags are made up of twelve characters. There are four characters for the day, four characters for the month, and four characters for the year. The characters used are in the following table:
| 0 | gbqj | 18 | kudd |
| 1 | dljt | 19 | nwal |
| 2 | yfad | 20 | hmca |
| 3 | kpsh | 21 | dqyo |
| 4 | igaw | 22 | kkag |
| 5 | pepb | 23 | viqt |
| 6 | ezcn | 24 | wpld |
| 7 | hwpd | 25 | nsiy |
| 8 | drir | 26 | myvo |
| 9 | rnwp | 27 | rgel |
| 10 | updw | 28 | zlxl |
| 11 | jsng | 29 | djno |
| 12 | xeoa | 30 | beti |
| 13 | rgdg | 31 | ewof |
| 14 | aofl | 32 | mqan |
| 15 | oeur | 33 | xsco |
| 16 | dspu | 34 | jfiq |
| 17 | jyuv |
The following is a screenshot of output from a network packet analyzer when the Flashback malware was searching mobile.twitter.com for the hashtag #pepbyfadxeoa, for today, March 5, 2012:
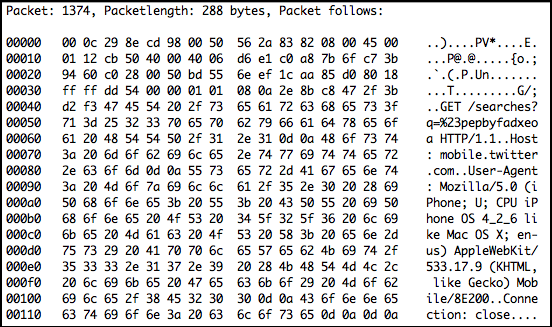
- Mozilla/4.0 (compatible; MSIE 7.0; Windows Phone OS 7.0; Trident/3.1; IEMobile/7.0; HTC; 7 Mozart T8698)
- Mozilla/4.0 (compatible; MSIE 7.0; Windows Phone OS 7.0; Trident/3.1; IEMobile/7.0; HTC; mwp6985)
- Mozilla/4.0 (compatible; MSIE 7.0; Windows Phone OS 7.0; Trident/3.1; IEMobile/7.0; SAMSUNG; SGH-i917)
- Mozilla/5.0 (iPhone; CPU iPhone OS 5_0 like Mac OS X) AppleWebKit/534.46 (KHTML, like Gecko) Version/5.1 Mobile/9A334 Safari/7534.48.3
- Mozilla/5.0 (iPhone; CPU iPhone OS 5_0 like Mac OS X) AppleWebKit/534.46 (KHTML, like Gecko) Version/5.1 Mobile/9A5302b Safari/7534.48.3
- Mozilla/5.0 (PWNED iPod; U; CPU iPhone OS 4_2_1 like Mac OS X; en-us) AppleWebKit/533.17.9 (KHTML, like Gecko) Version/5.0.2 Mobile/8C148 Safari/6533.18.5
There is no guarantee that there will be tweets every day, but Intego is monitoring Twitter, looking for these specific hashtags, and Intego VirusBarrier X6’s web threat protection has been updated to block searches using these combinations of characters.
It’s worth noting that the people behind the Flashback malware most likely to not send commands every day, and certainly delete their tweets, as Intego has found no past tweets in its searches. However, the malware clearly sends these HTTP requests, looking for such tweets.