Are “corrupt my file” sites safe? Here’s why to avoid corrupt-a-file services
Posted on
by
Joshua Long
Sometimes, through various means such as software bugs or incomplete downloads, files may inadvertently become corrupted. A corrupted file is not readable if you double-click on it; you’ll often see an error message instead. Malware such as ransomware and file or disk wipers can even cause intentional, malicious file corruption. (See our support article, “What is a Corrupted File?“)
Interestingly, there is also a gray market for “corrupt my file” services, for the purpose of intentional self-sabotage. While that may seem entirely counterproductive, corrupt-a-file sites make claims such as:
“Didn’t finish that assignment? Need more time to finish the report? Life happens… Upload your file and we’ll corrupt it for you. Then you can download and send it to whomever and they’ll only be able to open a corrupted file. This will give you some precious and sweet extra time.”
“Struggle with a report you can’t complete? Bored by this Excel sheet? Tired with this code which won’t work? Send us your file and we corrupt it. Your boss, customer or teacher will think you delivered on time, yet he can’t open it due to technology hassle. Mission completed!”
“Fool your friend/professor/boss sending trashed files and blame your Internet connection”
Aside from the obvious ethical problems of using a “file corruption as a service” site to cheat or deceive others, there are potential security or privacy concerns as well. Let’s explore several reasons why you should avoid such sites and services from that perspective.
Your files may contain sensitive, hidden data
Before uploading a file to any site, consider what data your file may contain. Are there any real people’s names or contact information? Are there any financial account details, or any other personally identifiable or potentially sensitive info within the file? If so, you probably shouldn’t send a copy of it to any unauthorized parties.
In some cases, you might not care whether others can view your file, for example if it’s a school assignment or a mundane report for work. However, it’s important to know that documents may also contain hidden metadata that you may want to keep private.
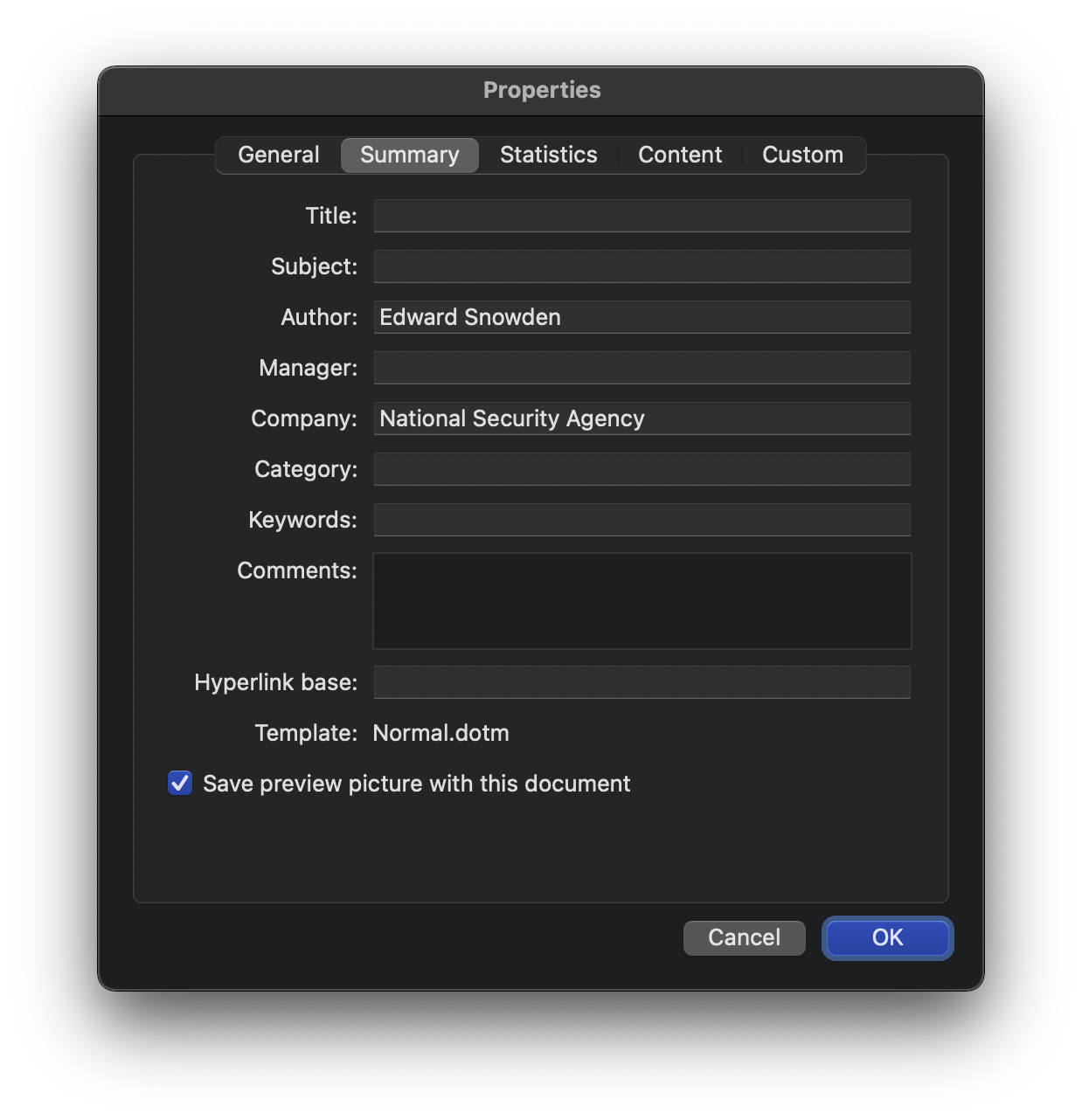
Microsoft Office documents contain hidden authorship metadata. Screenshot: Intego.
Consider, for example, that Microsoft Word, Excel, and PowerPoint documents typically contain the full, real name of the original author of a document, along with the name of their employer. That may not necessarily be information you want to share with an untrusted site—especially in combination with your IP address, which is visible to every site your visit (unless you’re using a VPN).
Even if you’re certain there’s nothing sensitive in your file, there’s more to consider before uploading it to a file corruption service.
Does the site have a privacy policy?
At least one popular file corruption site does not have a privacy policy. They don’t even make any claims whatsoever about what they do with files submitted to their service. A privacy policy should answer questions such as the following.
- Other than giving you a corrupted version, what does the site do with files you submit? Are submissions stored in a way that enables the site owner to see their contents? If so, what does the site operator do, if anything, with any potentially sensitive or personally identifiable information? (Sensitive data such as e-mail addresses, telephone numbers, social security numbers, or credit card information can easily be identified and extracted from files and used for illegal purposes, or sold on the black market.)
- What is their deletion policy for uploaded files? Do they keep them permanently? The site shouldn’t keep a copy of your original document after providing you with the corrupted version. (The longer the file is retained, the more likely that some unauthorized party will be able to obtain access to your document.)
- Are uploaded files deleted securely? “Deleting” a file typically leaves fragments of that file hidden on the drive. For optimal privacy, user-submitted files should ideally be overwritten (i.e. securely erased), not merely deleted.
Of course, even if a site does have a privacy policy, you should still exercise caution. Don’t assume that the site operator will actually comply with every claim in their privacy policy.
Where are the site and its owner based?
The geographical location of a server, or of the operator of a service, may also be worth considering. Some countries have laws or policies permitting the government to monitor all communications, or to compel a site owner to turn over all data that users submit to the site.
Perhaps—although it might seem conspiratorial—the site may even be operated by a foreign intelligence agency or someone acting on their behalf. What easier way is there to collect a broad swath of documents than to invite people to upload anything in exchange for some perceived benefit?
Alternatively, the site operator could be someone collecting data to sell on the black market, as mentioned previously. The location of the server and its operator are important here, too. Some countries turn a blind eye to cybercriminals who try to take advantage of foreigners. Even if you could prove that a site did something unethical with your data, that country’s law enforcement agencies may not be interested in punishing the site owner.
You can use a site like Website Location Finder to help identify or confirm where a site’s server is hosted.
Always think carefully before uploading a file to any site
Keep in mind that file-corruption services generally promote unethical use cases. It may, therefore, be unwise to expect the owner of that site to behave ethically with any documents you submit.
But even when you upload a file to a site with a good reputation, it’s wise to think carefully first. For example, consider that even VirusTotal, a legitimate site for scanning individual files for malware, encourages caution when deciding whether to upload a file to their service. When you upload files to VirusTotal, antivirus companies and members of the security community may be able to download copies of those files. Users of the site sometimes inadvertently submit files that contain confidential or sensitive data. Thankfully, VirusTotal has a process to request removal of sensitive data, but many online services are not so aware or accommodating.
Ultimately, it’s up to you whether to trust a site with your files. Before uploading, think about the potential sensitivity of any info or metadata in the file, consider whether the site is reputable, and peruse their privacy policy.
How can I learn more?
For more information about a similar scam—file converter sites—see our related article: “Are file converter sites safe? How to convert files safely on your Mac”
Are file converter sites safe? How to convert files safely on your Mac
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()
File shredder header image based on: “Paper Shredder” by Nick Bluth from the Noun Project (CC BY 3.0), Microsoft Word document icon ©Microsoft, “Red arrow” (CC0), Intego screenshot of Microsoft Word error message dialog box.