101 Security-Minded Reasons You Should Update to iOS 9
Posted on
by
Derek Erwin

iOS 9 has arrived! Yesterday, Apple officially released iOS 9 and the update comes to you packed with security fixes: iOS 9 patches 101 vulnerabilities (CVEs), to be exact. This update is available for: iPhone 6, iPhone 4s and later, iPod touch (5th generation) and later, and iPad 2 and later (including iPad mini 3 and iPad Air 2).
Apple’s iOS 9 update notice mentions the following details about iOS 9:
With this update your iPhone, iPad and iPod touch become more intelligent and proactive with powerful search and improved Siri features. New multitasking features for iPad allow you to work with two apps simultaneously, side-by-side or with the new Picture-in-Picture feature. And, built-in apps become more powerful with detailed transit information in Maps, a redesigned Notes app, and an all-new News app. And improvements at the foundation of the operating system enhance performance, improve security and give you up to an hour of extra battery life.
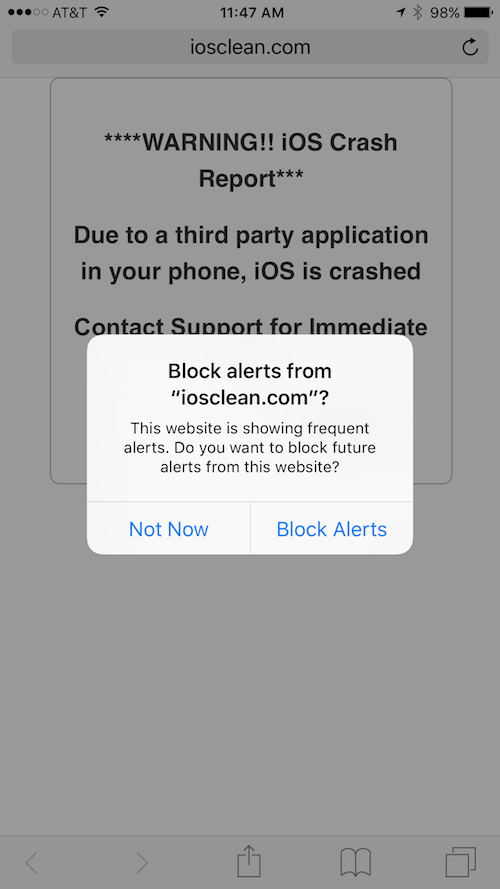
The list of security bugs addressed in the update is gigantic, and among the most prominent is a patch for the iOS crash report scam. On the iOS crash report scam, scammers had been displaying bogus error messages on potential victims’ iOS devices — fraudulently posing as Apple’s technical support team. A typical message reads as follows (phone numbers have been removed):
**** IOS Crash Report ****
IOS crashed previously due to unwanted websites visit. There is a problem with the configuration of your IOS. Please call Apple Technical Support at 0800-XXX-XXXX. Click on OK this will attempt to send a crash report to Apple. Call now Apple 0800-XXX-XXXX.
Fortunately, iOS 9 now detects if a website is showing frequent alerts, such as the one above, and allows you to block future alerts from the malicious website. As seen in the image below, when visiting a fraudulent website, after about two popup alerts, the option to block future alerts is revealed:
iOS 9 addresses 101 vulnerabilities altogether, giving you all-the-more reason to update to Apple’s latest mobile operating system. The complete list of security bugs patched with iOS 9 is below and describes the addressed vulnerabilities:
- CVE-2015-5916 : Some cards may allow a terminal to retrieve limited recent transaction information when making a payment. The transaction log functionality was enabled in certain configurations. This issue was addressed by removing the transaction log functionality.
- CVE-2015-5850 : A local attacker may be able to reset failed passcode attempts with an iOS backup. An issue existed in resetting failed passcode attempts with a backup of the iOS device. This was addressed through improved passcode failure logic.
- CVE-2015-5856 : Clicking a malicious ITMS link may lead to a denial of service in an enterprise-signed application. An issue existed with installation through ITMS links. This was addressed through additional installation verification.
- CVE-2015-5862 : Playing a malicious audio file may lead to an unexpected application termination. A memory corruption issue existed in the handling of audio files. This issue issue was addressed through improved memory handling.
- CVE-2015-5898 : A person with physical access to an iOS device may read cache data from Apple apps. Cache data was encrypted with a key protected only by the hardware UID. This issue was addressed by encrypting the cache data with a key protected by the hardware UID and the user’s passcode.
- CVE-2015-5885 : An attacker in a privileged network position can track a user’s activity. A cross-domain cookie issue existed in the handling of top level domains. The issue was address through improved restrictions of cookie creation.
- CVE-2015-3801 : An attacker may be able to create unintended cookies for a website. WebKit would accept multiple cookies to be set in the document.cookie API. This issue was addressed through improved parsing.
- CVE-2015-5912 : Malicious FTP servers may be able to cause the client to perform reconnaissance on other hosts. An issue existed in FTP packet handling if clients were using an FTP proxy.
- CVE-2015-5858 : A maliciously crafted URL may be able to bypass HTTP Strict Transport Security (HSTS) and leak sensitive data. A URL parsing vulnerability existed in HSTS handling. This issue was addressed through improved URL parsing.
- CVE-2015-5860 : A malicious website may be able to track users in Safari private browsing mode. An issue existed in the handling of HSTS state in Safari private browsing mode. This issue was addressed through improved state handling.
- CVE-2015-5841 : Connecting to a malicious web proxy may set malicious cookies for a website. An issue existed in the handling of proxy connect responses. This issue was addressed by removing the set-cookie header while parsing the connect response.
- CVE-2015-5824 : An attacker with a privileged network position may intercept SSL/TLS connections. A certificate validation issue existed in NSURL when a certificate changed. This issue was addressed through improved certificate validation.
- CVE-2015-5880 : A malicious application may be able to leak sensitive user information. Applications could access the screen framebuffer while they were in the background. This issue was addressed with improved access control on IOSurfaces.
- CVE-2015-5874 : Processing a maliciously crafted font file may lead to arbitrary code execution. A memory corruption issue existed in the processing of font files. This issue was addressed through improved input validation.
- CVE-2015-5829 : Processing a maliciously crafted text file may lead to arbitrary code execution. Memory corruption issues existed in the processing of text files. These issues were addressed through improved bounds checking.
- CVE-2015-5876 : A malicious application may be able to execute arbitrary code with system privileges. A memory corruption issue existed in dyld. This was addressed through improved memory handling.
- CVE-2015-5839 : An application may be able to bypass code signing. An issue existed with validation of the code signature of executables. This issue was addressed through improved bounds checking.
- CVE-2015-5847 : A local user may be able to execute arbitrary code with system privileges. A memory corruption issue existed in DiskImages. This issue was addressed through improved memory handling.
- CVE-2015-5855 : A malicious Game Center application may be able to access a player’s email address. An issue existed in Game Center in the handling of a player’s email. This issue was addressed through improved access restrictions.
- CVE-2014-8146, CVE-2015-1205 : Multiple vulnerabilities in ICU. Multiple vulnerabilities existed in ICU versions prior to 53.1.0. These issues were addressed by updating ICU to version 55.1.
- CVE-2015-5834 : A malicious application may be able to determine kernel memory layout. An issue existed that led to the disclosure of kernel memory content. This issue was addressed through improved bounds checking.
- CVE-2015-5848 : A local user may be able to execute arbitrary code with system privileges. A memory corruption issue existed in IOAcceleratorFamily. This issue was addressed through improved memory handling.
- CVE-2015-5867 : A malicious application may be able to execute arbitrary code with system privileges. A memory corruption issue existed in IOHIDFamily. This issue was addressed through improved memory handling.
- CVE-2015-5844, CVE-2015-5845, CVE-2015-5846 : A malicious application may be able to execute arbitrary code with system privileges. A memory corruption issue existed in the kernel. This issue was addressed through improved memory handling.
- CVE-2015-5843 : A local user may be able to execute arbitrary code with system privileges. A memory corruption issue existed in IOMobileFrameBuffer. This issue was addressed through improved memory handling.
- CVE-2015-5863 : A local attacker may be able to read kernel memory. A memory initialization issue existed in the kernel. This issue was addressed through improved memory handling.
- CVE-2015-5832 : AppleID credentials may persist in the keychain after sign out. An issue existed in keychain deletion. This issue was addressed through improved account cleanup.
- CVE-2015-5791, CVE-2015-5793, CVE-2015-5814, CVE-2015-5816, CVE-2015-5822, CVE-2015-5823 : Visiting a maliciously crafted website may lead to arbitrary code execution. Memory corruption issues existed in WebKit. These issues were addressed through improved memory handling.
- CVE-2015-5868, CVE-2015-5896, CVE-2015-5903 : A local user may be able to execute arbitrary code with kernel privileges. A memory corruption issue existed in the kernel. This issue was addressed through improved memory handling.
- CVE-2013-3951 : A local attacker may control the value of stack cookies. Multiple weaknesses existed in the generation of user space stack cookies. This was addressed through improved generation of stack cookies.
- CVE-2015-5882 : A local process can modify other processes without entitlement checks. An issue existed where root processes using the processor_set_tasks API were allowed to retrieve the task ports of other processes. This issue was addressed through added entitlement checks.
- CVE-2015-5879 : An attacker may be able to launch denial of service attacks on targeted TCP connections without knowing the correct sequence number. An issue existed in xnu’s validation of TCP packet headers. This issues was addressed through improved TCP packet header validation.
- CVE-2015-5869 : An attacker in a local LAN segment may disable IPv6 routing. An insufficient validation issue existed in handling of IPv6 router advertisements that allowed an attacker to set the hop limit to an arbitrary value. This issue was addressed by enforcing a minimum hop limit.
- CVE-2015-5842 : A local user may be able to determine kernel memory layout. An issue existed in XNU that led to the disclosure of kernel memory. This was addressed through improved initialization of kernel memory structures.
- CVE-2015-5748 : A local user may be able to cause a system denial of service. An issue existed in HFS drive mounting. This was addressed by additional validation checks.
- CVE-2014-8611 : A local user may be able to execute arbitrary code with kernel privileges. A memory corruption issue existed in the kernel. This issue was addressed through improved memory handling.
- CVE-2015-5899 : A local user may be able to execute arbitrary code with kernel privileges. A memory corruption issue existed in the kernel. This issue was addressed through improved memory handling.
- CVE-2015-5857 : An attacker can send an email that appears to come from a contact in the recipient’s address book. An issue existed in the handling of the sender’s address. This issue was addressed through improved validation.
- CVE-2015-5851 : A local attacker may be able to observe unprotected multipeer data. An issue existed in convenience initializer handling in which encryption could be actively downgraded to a non-encrypted session. This issue was addressed by changing the convenience initializer to require encryption.
- CVE-2015-5831 : A malicious application may be able to determine kernel memory layout. An uninitialized memory issue in the kernel led to the disclosure of kernel memory content. This issue was addressed through memory initialization.
- CVE-2015-0286, CVE-2015-0287 : Multiple vulnerabilities in OpenSSL. Multiple vulnerabilities existed in OpenSSL versions prior to 0.9.8zg. These were addressed by updating OpenSSL to version 0.9.8zg.
- CVE-2015-5837 : A malicious enterprise application can install extensions before the application has been trusted. An issue existed in the validation of extensions during installation. This was addressed through improved app verification.
- CVE-2015-5840 : Processing malicious data may lead to unexpected application termination. An overflow fault existed in the checkint division routines. This issue was addressed with improved division routines.
- CVE-2015-5903 : A local user may be able to read Safari bookmarks on a locked iOS device without a passcode. Safari bookmark data was encrypted with a key protected only by the hardware UID. This issue was addressed by encrypting the Safari bookmark data with a key protected by the hardware UID and the user’s passcode.
- CVE-2015-5904 : Visiting a malicious website may lead to user interface spoofing. An issue may have allowed a website to display content with a URL from a different website. This issue was addressed through improved URL handling.
- CVE-2015-5905 : Visiting a malicious website may lead to user interface spoofing. Navigating to a malicious website with a malformed window opener may have allowed the display of arbitrary URLs. This issue was addressed through improved handling of window openers.
- CVE-2015-1129 : Users may be tracked by malicious websites using client certificates. An issue existed in Safari’s client certificate matching for SSL authentication. This issue was addressed through improved matching of valid client certificates.
- CVE-2015-5764, CVE-2015-5765, CVE-2015-5767 : Visiting a malicious website may lead to user interface spoofing. Multiple user interface inconsistencies may have allowed a malicious website to display an arbitrary URL. These issues were addressed through improved URL display logic.
- CVE-2015-5835 : A malicious app may be able to intercept communication between apps. An issue existed that allowed a malicious app to intercept URL scheme communication between apps. This was mitigated by displaying a dialog when a URL scheme is used for the first time.
- CVE-2015-5892 : A person with physical access to an iOS device may be able to use Siri to read notifications of content that is set not to be displayed at the lock screen. When a request was made to Siri, client side restrictions were not being checked by the server. This issue was addressed through improved restriction checking.
- CVE-2015-5861 : A person with physical access to an iOS device can reply to an audio message from the lock screen when message previews from the lock screen are disabled. A lock screen issue allowed users to reply to audio messages when message previews were disabled. This issue was addressed through improved state management.
- CVE-2015-5838 : A malicious application may be able to spoof another application’s dialog windows. An access issue existed with privileged API calls. This issue was addressed through additional restrictions.
- CVE-2015-5895 : Multiple vulnerabilities in SQLite v3.8.5. Multiple vulnerabilities existed in SQLite v3.8.5. These issues were addressed by updating SQLite to version 3.8.10.2.
- CVE-2015-5522, CVE-2015-5523 : Visiting a maliciously crafted website may lead to arbitrary code execution. A memory corruption issue existed in Tidy. This issue was addressed through improved memory handling.
- CVE-2015-5827 : Object references may be leaked between isolated origins on custom events, message events and pop state events. An object leak issue broke the isolation boundary between origins. This issue was addressed through improved isolation between origins.
- CVE-2015-5789, CVE-2015-5790, CVE-2015-5792, CVE-2015-5794, CVE-2015-5795, CVE-2015-5796, CVE-2015-5797, CVE-2015-5799, CVE-2015-5800, CVE-2015-5801, CVE-2015-5802, CVE-2015-5803, CVE-2015-5804, CVE-2015-5805, CVE-2015-5806, CVE-2015-5807, CVE-2015-5809, CVE-2015-5810, CVE-2015-5811, CVE-2015-5812, CVE-2015-5813, CVE-2015-5817, CVE-2015-5818, CVE-2015-5819, CVE-2015-5821 : Visiting a maliciously crafted website may lead to arbitrary code execution. Memory corruption issues existed in WebKit. These issues were addressed through improved memory handling.
- CVE-2015-5820 : Visiting a malicious website may lead to unintended dialing. An issue existed in handling of tel://, facetime://, and facetime-audio:// URLs. This issue was addressed through improved URL handling.
- CVE-2015-5906 : QuickType may learn the last character of a password in a filled-in web form. An issue existed in WebKit’s handling of password input context. This issue was addressed through improved input context handling.
- CVE-2015-5907 : An attacker in a privileged network position may be able to redirect to a malicious domain. An issue existed in the handling of resource caches on sites with invalid certificates. The issue was addressed by rejecting the application cache of domains with invalid certificates.
- CVE-2015-5826 : A malicious website may exfiltrate data cross-origin. Safari allowed cross-origin stylesheets to be loaded with non-CSS MIME types which could be used for cross-origin data exfiltration. This issue was addressed by limiting MIME types for cross-origin stylesheets.
- CVE-2015-5825 : The Performance API may allow a malicious website to leak browsing history, network activity, and mouse movements. WebKit’s Performance API could have allowed a malicious website to leak browsing history, network activity, and mouse movements by measuring time. This issue was addressed by limiting time resolution.
- CVE-2015-5921 : An attacker in a privileged network position may be able to leak sensitive user information. An issue existed with Content-Disposition headers containing type attachment. This issue was addressed by disallowing some functionality for type attachment pages.
- CVE-2015-5788 : Visiting a malicious website may disclose image data from another website. A cross-origin issue existed with “canvas” element images in WebKit. This was addressed through improved tracking of security origins.
Apple iOS users can download and install the iOS 9 update through iTunes or through your device settings (select General > Software Update).