Malware + Recommended + Security News
WannaCry and the State of Mac Ransomware
Posted on
by
Joshua Long
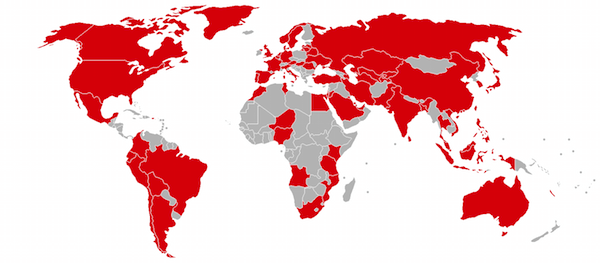
By now, you’ve probably heard about “WannaCry” in the news. As a Mac user, you might assume your computer is immune from ransomware attacks of this sort. That may not be such a wise assumption.
Today we’ll explain who WannaCry ransomware affects and how to protect yourself, as well as the current state of Mac ransomware. Read on to learn why you’ll want to be proactive about protecting your Mac.
Wanna Cry? You Might if You Use Windows
During the past couple weeks, serious vulnerabilities in unpatched copies of Microsoft Windows have led to the spread of destructive malware on a global scale.
The first malware to appear — known by names such as WannaCry, WanaCrypt0r, and WCry — is ransomware that encrypts files on a user’s computer and demands that a ransom be paid in Bitcoin currency. It spreads through wormable flaws in Windows’ implementation of SMB, a networking technology associated with file sharing.
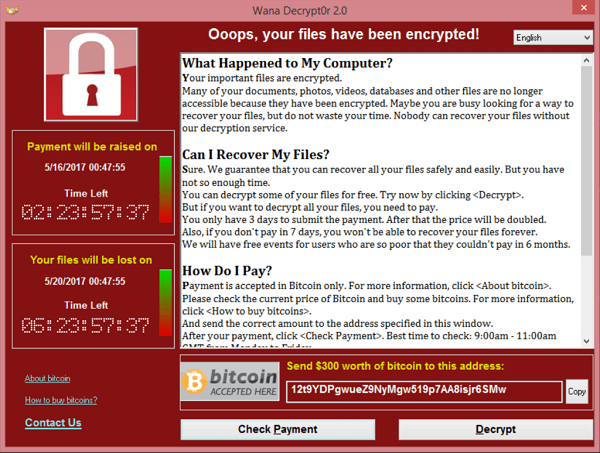
Microsoft patched the SMB flaws in Windows months ago, after the so-called “EternalBlue” vulnerability was publicly disclosed through an alleged leak of stockpiled NSA exploits. But some affected systems, such as Windows XP, are no longer officially supported by Microsoft and did not receive a patch until after WannaCry (and other malware using the same exploit) had already begun spreading across the globe.
Microsoft has published articles offering customer guidance and a very detailed overview of WannaCrypt’s behavior, including links to download emergency patches for various versions of Windows back to XP and Server 2003.
Other Windows malware in the wild such as Adylkuzz, Uiwix, and EternalRocks have already begun to exploit the EternalBlue vulnerability.
What if I Have Windows on My Mac?
Apple’s Mac operating system, macOS, is not known to be directly affected by the vulnerability.
However, those using Windows on their Macs will need to install the appropriate update to ensure that their Mac’s copy of Windows doesn’t become infected.
As a reminder, if your Mac is still running an old version of Windows, such as Windows Vista or Windows XP, Microsoft is no longer officially supporting those operating systems, so simply installing the WannaCry-related SMB patch will not protect Windows from other critical vulnerabilities that Microsoft has no intention to fix. In other words, it’s unsafe to use old and outdated versions of Windows, even if you have them installed on your Mac.
The State of Mac Ransomware
You may be asking yourself: what if I’m a Mac user and I don’t use Windows? Does that mean I’m safe?
The short answer is that as far as the first variants of WannaCry are concerned, if you aren’t running Windows on your Mac, then this particular malware won’t be able to infect your computer.
However, on the question of whether Mac users are immune from ransomware attacks, the answer is a resounding no.
A few months ago, the so-called “Patcher” (detected by Intego VirusBarrier as OSX/Filecoder) Mac ransomware began circulating on BitTorrent, masquerading as Adobe Premiere CC and Microsoft Office 2016 “cracks.” Rather than circumventing Adobe or Microsoft’s software activation requirements as implied, the Trojan horses instead encrypt the user’s files and demand a ransom.
Full Details: Patcher Ransomware Attacks macOS, Encrypts Files Permanently
Last year, ransomware known as KeRanger (detected by Intego VirusBarrier as OSX/KeRanger) was distributed via infected copies of Transmission, a popular BitTorrent app for Mac. The twist is that Transmission’s own site linked to the infected software, unbeknownst to the developer.
Full Details: Mac Users Hit by Rare Ransomware Attack, Spread via Transmission BitTorrent App
Even if you never do anything remotely related to BitTorrent, your Mac can still become infected.
Earlier this month, popular video transcoding software, Handbrake, was infected with the PROTON remote access Trojan (RAT), as reported by MacObserver. Similar to what happened with Transmission last year, the infected Handbrake software was distributed through the developer’s own official site until the developer became aware of the problem.
What Can Mac Users Do to Protect Themselves?
Being cautious about where you surf online is a good start, but as we’ve seen, even legitimate sites can get hacked or exploited and may distribute software that can infect your computer.
Following are some additional ways you can help safeguard your Mac against ransomware.
Anti-Virus Software
Installing a trusted security suite, including Mac anti-virus protection, is an essential component to keeping your Mac and your data safe. Anti-virus software can help protect your Mac against known malware that’s in the wild. Intego’s protection suite also includes file backup software and other useful utilities.
Backups
Keeping an unattached backup is another essential component to protecting your data. What is an “unattached” backup? Leaving an external hard drive permanently attached to your Mac and using Apple’s Time Machine functionality is insufficient because ransomware can encrypt your Time Machine backups as well, so you’ll want to keep a backup that’s detached from your computer so it can’t be touched by ransomware.
One possible solution is to use an online or “cloud” backup service that continuously uploads your files. These services often have “rollback” or “versioning” capability, so if your files get encrypted by ransomware, and then the encrypted versions get uploaded to your online backup service, you can still recover an older version of the file.
Although for some people a cloud backup solution may be a good option, there are some potential challenges with this approach:
- You’ll want to carefully vet whichever service you use, since they’ll have copies of very sensitive data from your Mac. Ask yourself: should I really trust them with everything on my Mac?
- Backing up to the cloud may cause you to exceed your Internet service provider’s data cap, so before you pay for a subscription to a cloud backup service, you’ll want to contact your ISP to find out if they have a maximum number of gigabytes or terabytes per month before they impose penalties (such as additional charges, slower data speeds, or discontinuation of service).
- Depending on your Internet service’s upload speed and the speed of your cloud backup service, it can take a very, very long time to do the initial synchronization of all your data over the Internet, particularly if you have hundreds of gigabytes or even terabytes of data. If you happen to get hit with ransomware during the days, weeks, or even months while your data is backing up for the first time, you may lose some data that had not been backed up yet.
Another option is to use a local backup that gets unmounted (“ejected”) between backups. Be sure to see our step-by-step guide, and other tips about protecting your Mac from ransomware, here: A Layman’s Guide to Ransomware Protection.
You can, and should, consider using multiple backup methods. Keep in mind the “3-2-1” backup principles, as described here: Data Backup Plan: How to Implement the 3-2-1 Backup Strategy.
For Über-Geeks Only
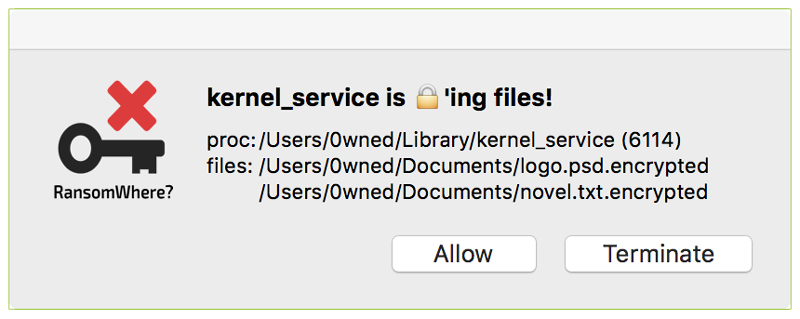
If practicing safe surfing habits, using a trusted protection suite including Mac anti-virus software, and implementing local backups and cloud backups still doesn’t seem like doing enough to protect yourself — and if you’re a very advanced Mac user — you could try using software that tries to generically detect ransomware, such as Patrick Wardle’s RansomWhere? app.
Be advised that RansomWhere? is not well suited for the average or novice user; it often displays warnings related to legitimate software that’s trying to update in the background (such as Google software and Dropbox), and its dialog boxes can be confusing if you don’t know much about how Macs work under the hood.
Stay Safe Out There
Another way to help yourself stay safe online is to subscribe to The Mac Security Blog, where we cover important topics about Internet safety and keep you informed about security news that affects users of Apple products. You can also follow Intego on Twitter and Facebook.