How to Steal an iPhone’s Passcode (from up to 150 feet away!)
Posted on
by
Graham Cluley
Many of us know the danger of shoulder-surfers.
Those are the people who lurk beside you, or peek over your shoulder, as you enter a password on your computer or tap the PIN code into an ATM.
But did you know that the people stealing your iPhone or iPad passcode could be up to 150 feet away, and not even able to see your device’s screen?
It sounds like science fiction, but researchers at the University of Massachusetts Lowell claim they can easily steak smartphone passcodes as they are typed in, even if they are well out of arm’s reach.
Xinwen Fu, a scientist who worked on the project, described to Wired how the research revealed that passcodes could be determined on iOS and Android devices even when the screen itself wasn’t visible, by tracking and taking video of the users’ finger taps.

Spying on a passcode with Google Glass. Image source: Cyber Forensics Laboratory at University of Massachusetts Lowell
Unsurprisingly, different hardware in the hands of the would-be hackers produced different results.
Google Glass could detect a passcode with 83% accuracy, from a distance of three feet. A $72 Logitech webcam scored a more impressive 92% accuracy.
Best of all was the iPhone 5’s built-in camera, which accurately identified passcodes 100% of the time.
But before you smirk and admit you have to applaud Apple for the quality of their smartphone camera, here’s something else to consider.
A $700 high-definition Panasonic camcorder, almost 150 feet from its intended target, was able to extract the passcode from a victim’s iPad with its optical zoom.

Capturing passcodes at distance with a high-definition camcorder. Image source: Cyber Forensics Laboratory at University of Massachusetts Lowell
Of course, despite its poorer performance, Google Glass might be the one to be most concerned about – as it can take video footage so surreptitiously.
“Any camera works, but you can’t hold your iPhone over someone to do this,” says Fu. “Because Glass is on your head, it’s perfect for this kind of sneaky attack.”
How to Protect Yourself
My first recommendation is to stop using simple four digit passcodes for your iOS devices. Even though the researchers claim that longer passwords (that aren’t just limited to the numbers 0 to 9) don’t appear to be dramatically harder to crack, they clearly provide a higher level of security.
You can do this by going into Settings / Passcode (you may be asked for your existing passcode at this point), and toggling “Simple Passcode.”
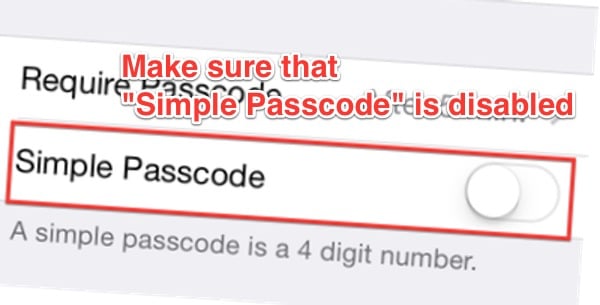
Secondly, if you’re worried that someone might be snooping, obscure your keypresses as you unlock your iPhone, iPad or indeed Android device – just like you would shield the numeric pad as you enter your PIN at a cash machine.
Finally, don’t let your iDevice out of your sight! Yes, it’s bad if your passcode ends up in the wrong hands – but the bad guys can’t actually do anything with it unless they manage to get physical access to your device.
Xinwen Fu and his fellow researchers will present a paper about their research at the Black Hat conference later this year, and release an Android app called PEK (Privacy Enhancing Keyboard) that randomizes the buttons on a lockscreen keyboard to make snooping via this method considerably more tricky.
To demonstrate a fix for that PIN privacy issue, the researchers have built an Android add-on that randomizes the layout of a phone or tablet’s lockscreen keyboard. They plan to release the software, dubbed Privacy Enhancing Keyboard or PEK, as an app in Google’s Play store and as an Android operating system update at the time of their Black Hat talk.
Will an app like PEK ever be released for iOS? It’s hard to imagine it happening any time soon. Apple has tight control over many aspects of its operating system, making it impossible for third-parties to mess with such fundamental aspects as the iPhone/iPad lock screen.
Unless, of course, you’ve decided to jailbreak your iOS device – in which case you could have any number of other security issues to consider… 😉