Malware + Recommended + Security & Privacy + Security News
Serious Zero-Day Security Flaw in iOS and OS X Could Lead to Password Theft
Posted on
by
Graham Cluley

Is almost nine months long enough to fix a serious security vulnerability that hackers could use to steal passwords and plant malware undetected on computers and smartphones?
You would certainly like to think so, wouldn’t you?
Especially if the security holes were in the heart of iOS and OS X, and the company responsible for fixing them was Apple with its considerable resources.
And yet, alarms have been rung today that Mac and iDevice users remain at risk, over half a year after university researchers privately disclosed details of the problem to Apple’s security team in Cupertino.
Researchers from Indiana University, Peking University, and Georgia Institute of Technology, joined forces to uncover the serious security issue, which they document in a technical paper entitled, “Unauthorized Cross-App Resource Access on Mac OS X and iOS.”
In the paper, the researchers describe how they discovered serious exploitable bugs in Mac OS X and iOS, enabling them to silently steal passwords from installed apps.
In a report in The Register, which broke the story, the scale of the researchers’ achievement is made clear:
The team was able to upload malware to the Apple app store, passing the vetting process without triggering alerts. That malware, when installed on a victim’s device, raided the keychain to steal passwords for services including iCloud and the Mail app, and all those stored within Google Chrome.
Of course, if the researchers were able to upload boobytrapped malicious apps to the official App Store without being spotted by Apple, it’s natural to worry that others with criminal intent might have managed to do the same.
In a YouTube video, the researchers demonstrate how a malicious app running on OS X Yosemite are able to steal iCloud tokens supposedly securely stored in Keychain:
According to the paper, the flaw is caused by a “lack of app-to-app and app-to-OS authentications,” leading to unauthorized cross-app resource access (XARA). To determine the size of the problem, the team developed a tool that automatically scanned OS X and iOS apps in order to determine if the necessary protection was missing from their code.
 A staggering 88.6% of 1,612 free OS X and iOS apps downloaded from the official app stores were found to be “completely exposed” to the attacks. A result the researchers described as “dire”:
A staggering 88.6% of 1,612 free OS X and iOS apps downloaded from the official app stores were found to be “completely exposed” to the attacks. A result the researchers described as “dire”:
“The consequences are dire: for example, on the latest Mac OS X 10.10.3, our sandboxed app successfully retrieved from the system’s keychain the passwords and secret tokens of iCloud, email and all kinds of social networks stored there by the system app Internet Accounts, and bank and Gmail passwords from Google Chrome; from various IPC channels, we intercepted user passwords maintained by the popular 1Password app (ranked 3rd by the MAC App Store) and the secret token of Evernote (ranked 3rd in the free “Productivity” apps); also, through exploiting the BID vulnerability, our app collected all the private notes under Evernote and all the photos under WeChat. We reported our findings to Apple and other software vendors, who all acknowledged their importance.”
Attacks on vulnerable apps are said to have potentially serious consequences:
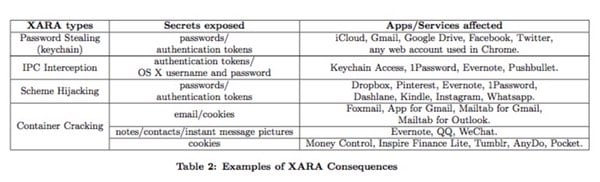
“Specifically, keychain credentials for high-profile services (e.g. iCloud, Gmail, Google Drive, Facebook, Twitter, LinkedIn, etc.) and any web accounts in Google Chrome are completely exposed. All their passwords and secret tokens can be collected by the adversary. Those vulnerable to the IPC interception include Keychain Access, Evernote, 1Password, Pushbullet, etc. Their sensitive data, such as authentication tokens and even current OS user’s username and passwords are up for grabs. The scheme vulnerability was found in 1Password, Dash- lane, Evernote, Kindle, Adobe Revel, Wunderlist, etc., on OS X, through which app users’ credentials can be gathered. On iOS, popular apps like Pinterest, Instagram, U.S. Bank (banking), Citi Mobile (banking), PayPal, Amazon, WhatsApp, Dropbox, etc., were found to be exploitable. Their authentication tokens and other information can be stolen.”
“Note that all the attack apps were successfully released by the Apple Stores. So, the security threats are indeed realistic.”
So, it’s a serious problem. And, as yet, not fixed.
The university researchers say that they first reported the vulnerability to Apple on October 15 2014, and contacted them again in November 2014 and early this year. They claimed that Apple told them that because of the complex nature of the security issue, six months’ grace would be required to develop a solution.
Unfortunately, that fix has still not emerged and the researchers have chosen to go public with their findings.
For now, until a proper solution is discovered, the most secure approach might be to exercise caution about what apps you download onto your Macs and iOS devices, even if they are listed in the official iOS and Mac App Store — stick with apps from known developers.