SabPab Backdoor Exploits Java Vulnerability
Posted on
by
Peter James
Yet another malware has been found to exploit the CVE-2012-0507 Java vulnerability with a drive by download. SabPab is a backdoor that seeks to connect to remote command and control servers, presumably to harvest information on infected Macs. This malware installs in the user’s /Library/LaunchAgents folder, so no administrator password is needed. It places its code in the user’s /Library/Preferences folder (the com.apple.PubSabAgent.pfile):
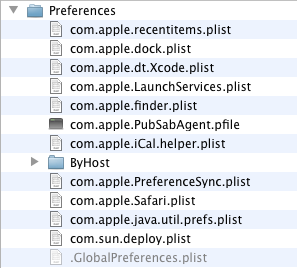
It is worth noting that the Java vulnerability this malware uses was patched by Apple ten days ago. So Mac users should make sure that they have their Java up to date.
Intego’s Mac antivirus, VirusBarrier X6 with malware definitions dated April 12, 2012 or later, will detect and remove the SabPab backdoor.