Security & Privacy + Security News
Google Discloses Security Vulnerabilities in OS X—While Leaving a Billion Android Users Exposed
Posted on
by
Graham Cluley

If you’ve been following the security beat closely in the last month or so, you’ll be aware that Google has managed to get itself into some hot water on the vulnerability side of things.
What’s happened is this. A team of Google security engineers, calling themselves Project Zero, have taken it upon themselves to find flaws in other vendor’s software. And, if they feel the other vendor isn’t quick enough in fixing the software vulnerabilities, the Googlenauts release details of not just how to exploit the software vulnerability, but actual proof-of-concept code to do the deed too.
The release of actual exploit code, that any internet ne’er-do-well can pick up and alter for their own malicious ends, is bad enough—but the Google Project Zero team has done itself no favours by dishing the dirt on exploitable vulnerabilities when they knew that a patch to protect all vulnerable users was only a day or two away.
Three times in the last month, Google has gone public about flaws in arch-rival Microsoft’s code, and effectively handed online criminals the blueprints to exploit the vulnerabilities themselves.
Now, I accept that the issue of how to best disclose vulnerabilities is a contentious one—with many holding strong and opposing opinions. But I really cannot understand how Google engineers think they are doing the internet community a favour, if they know a patch for a bug is only a matter of a day or so away and yet release their exploit code anyway.
Why am I talking about this on the Intego Mac Security blog? Because it’s not just Microsoft that is in Google’s firing line.
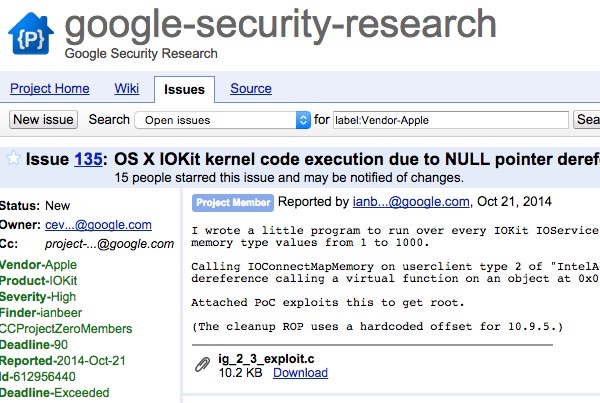
Last week, Google disclosed three vulnerabilities in OS X (here, here, and here), having first privately informed Apple in October last year.
As the 90-day grace period has expired, Google feels it’s right to make details of the vulnerabilities public, and tell people how to exploit them.
Thankfully, none of the OS X vulnerabilities discovered by Google appear to be highly critical and seem to require an attacker to have physical access to a vulnerable Mac—but that’s not really the point.
Is it really helping anyone by making details of these bugs public? If Google’s engineers felt that Apple needed a kick up the bum to fix the flaws more quickly, wouldn’t it have been sufficient to demonstrate the vulnerabilities to members of the computer security press rather than making the code public?
After all, the media would think it was a pretty hot story if Apple was being lackadaisical about security—and pressure could be brought to bear.
Fortunately, according to iMore, the security flaws are all fixed in OS X Yosemite 10.10.2, which is now undergoing beta test.
Meanwhile, perhaps someone should remind Google of the saying, “People in glass houses shouldn’t throw stones.”
As is being widely reported, more than a billion Android smartphones, running Android 4.3 or earlier, are being left exposed to attacks by Google, which has declared it will not fix vulnerabilities in its WebView code.
Just imagine if Apple researchers gave Google 90 days to fix a WebView vulnerability in Android 4.3, and then released proof-of-concept exploit code.
I wonder how Google would feel then?