New SPOILER attack puts Intel processors at risk
Posted on
by
Jay Vrijenhoek

 A new attack has surfaced called SPOILER, which builds on past research behind Meltdown, Spectre, and Rowhammer attacks.
A new attack has surfaced called SPOILER, which builds on past research behind Meltdown, Spectre, and Rowhammer attacks.
Back in January 2018, you probably heard about Meltdown and Spectre, the nicknames for a series of severe vulnerabilities in the way computer processors function that could allow leakage of information stored in memory. Intel, Apple, and other affected companies have since mitigated these vulnerabilities through microcode updates for affected processors, as well as updates for software such as operating systems and Web browsers.
Rowhammer is an attack against system memory (RAM) that can be greatly accelerated by using a SPOILER attack. The following comic provides a humorous explanation of Meltdown and Spectre and partially explains Rowhammer:
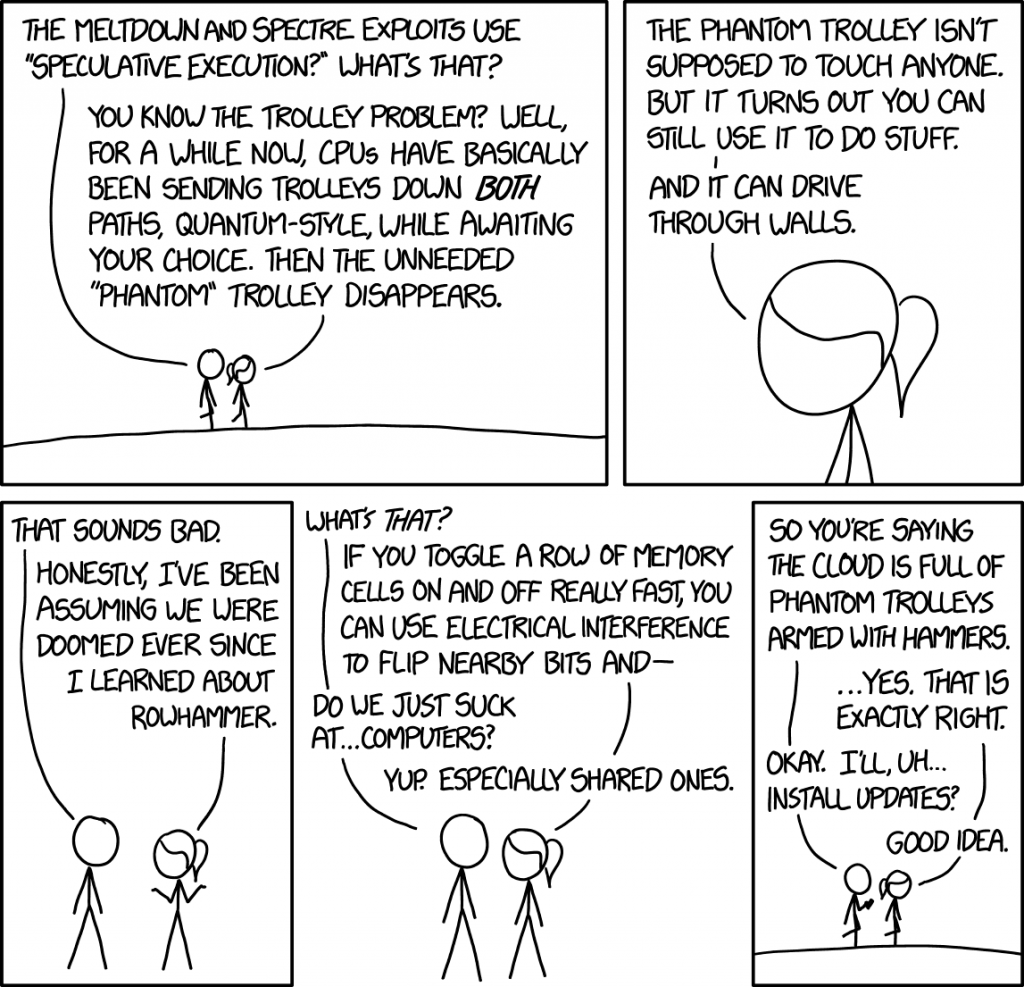
Image credit: xkcd #1938 by Randall Munroe
What is the new SPOILER attack?
Now there is a new attack named SPOILER. Much like the Spectre and Meltdown attacks, SPOILER abuses a speed-enhancing feature called speculative execution in Intel processors.
Speculative execution is one of several techniques used to make processors faster. A processor will guess (speculate) which instructions may be next and that way can be ready for those instructions if they actually come along, resulting in faster execution. Incorrect guesses will be discarded by memory disambiguation, but the problem is that Intel processors don’t do the discarding part very well.
SPOILER goes after the Memory Order Buffer of the processor, which is a different area than those attacked by Spectre and Meltdown. The Memory Order Buffer facilitates the communication between the processor and the memory (RAM), from which the processor draws its guesses.
Because the SPOILER attack goes after a different part of the processor, previous Spectre and Meltdown mitigations do not protect from it. As described in the research paper “SPOILER: Speculative Load Hazards Boost Rowhammer and Cache Attacks,” published by researchers from Worcester Polytechnic Institute in Massachusetts and the University of Lübeck in Germany:
“In contrast to previous attacks on speculative and transient behaviors, we discover a new leakage on the undocumented memory disambiguation and dependency resolution logic. SPOILER is not a Spectre attack. The root cause for SPOILER is a weakness in the address speculation of Intel’s proprietary implementation of the memory subsystem which directly leaks timing behavior due to physical address conflicts. Existing [Spectre] mitigations would therefore not interfere with SPOILER.”
SPOILER can be used to rapidly accelerate the Rowhammer attack, to the degree that the researchers said that “instead of taking weeks, Rowhammer could take just seconds,” according to The Register.
Which Apple devices are affected?
Since 2006, Apple has incorporated Intel CPUs (processors) in its Mac desktop and notebook computers.
Meanwhile, Apple’s iOS devices (iPhone, iPad, and iPod touch) use Apple’s A-series processors, which are based on the ARM processor architecture. The researchers who documented SPOILER also tested some ARM and AMD architectures (ARMv8-A and AMD Bulldozer) but did not find them to be vulnerable to the SPOILER attack.
Therefore, Macs are presumably vulnerable to SPOILER attacks, but other Apple products are not known to be vulnerable.
Will updates to protect against SPOILER be available?
Similar to Spectre and Meltdown, complete protection of SPOILER attacks will likely require both hardware and software updates. The researchers note that hardware mitigation may impact performance and could take years to be deployed, especially to legacy systems.
As microcode updates are part of Apple’s firmware updates (which, in turn, are distributed with macOS updates), it would be up to Apple to decide which hardware might receive patches for SPOILER. This would almost certainly leave out hardware not supported by the latest macOS. Software mitigation would likely be incomplete and would have to come in the form of macOS and Safari (and third-party browser) updates.
The researchers informed Intel of their findings on December 1st, 2018. Intel told The Register the following:
“Intel received notice of this research, and we expect that software can be protected against such issues by employing side channel safe development practices. This includes avoiding control flows that are dependent on the data of interest. We likewise expect that DRAM modules mitigated against Rowhammer style attacks remain protected. Protecting our customers and their data continues to be a critical priority for us and we appreciate the efforts of the security community for their ongoing research.”
This does not sound like Intel is planning to do any mitigating on their end, which puts the pressures of addressing the issue on software developers, but time will tell.
How can I keep my Mac safe from SPOILER attacks?
As to how one gets hit by SPOILER, this can be done by malware installed on your system, a malicious JavaScript on a website, or someone with unauthorized access to your computer. Of course, one of the most sensitive types of data that could be extracted by using the SPOILER attack will be passwords. But really any data that lives inside the computer’s memory (RAM) can be extracted this way, potentially including credit card numbers and other financial or personally identifiable information.
Keeping malware off your system shouldn’t be too hard, assuming you’ve got VirusBarrier, the world’s best Mac anti-malware protection.
But what about JavaScript attacks? You’ll want to make sure you use an up-to-date Web browser. Firefox, Opera, and Google Chrome are a few examples of browsers that are actively developed and updated, but Safari is only updated on the current macOS and receives only minimal updates for the two previous macOS versions. If you run an older version of macOS, consider upgrading to macOS Mojave if your Mac can support it (and if Apple doesn’t officially support macOS Mojave on your Mac, you may still be able to use a clever workaround to keep your Mac updated and more secure).
I am a huge fan of NoScript, a Firefox extension. As the name implies, it stops websites from loading scripts, JavaScript included. Unless you authorize a website to use scripts, they will not load. If you use NoScript and only enable scripts on websites you trust, avoiding malicious JavaScripts should become a lot easier.
There is now a version of NoScript for Google Chrome. For the Opera browser, there is a similar extension from another developer, called NoScript Lite. Meanwhile, Brave is a privacy-focused browser that can easily be configured to block JavaScript by default.
Unfortunately, NoScript is not available for Safari. I have found that getting any kind of browser extension such as ad blocker or script blocker to work in Safari under macOS Mojave, has become difficult to the point where I abandoned Safari completely and now use Firefox exclusively. For older versions of macOS, there is JSBlocker which will work up to macOS High Sierra 10.13.6.
Be forewarned, however, that while NoScript and other JavaScript blockers provide a lot of protection (including against browser-based SPOILER attacks), disabling JavaScript also breaks most Web pages. It can take some trial and error to get sites such as your banking, billing, and travel sites to work correctly—which means that users who aren’t very tech-savvy may find it far more frustrating than practical.
Will Intel bugs continue to plague Mac users?
You may have heard the rumors that Apple is planning a move away from the Intel architecture, perhaps as soon as 2020. Intego’s podcasters Josh and Kirk spoke about this in a recent episode of the Intego Mac Podcast, and it has been reported elsewhere as well.
A move away from Intel would certainly solve the SPOILER issue for new devices from that point forward, but only time will tell which (if any) Intel-based Macs will receive updates to protect against SPOILER.
Not everyone is looking forward to another architecture switch (Apple moved from IBM PowerPC to Intel processors in 2006, and in the mid-1990s Apple moved from Motorola 680×0 to PowerPC). But one benefit of switching is that it would leave all the currently known and future Intel vulnerabilities behind us.
And make no mistake, more Intel vulnerabilities will almost certainly be discovered; the research behind Spectre and Meltdown has virtually guaranteed that. Until you are able to buy a Mac with an ARM-based processor in it, or until Intel and Apple push out some mitigations, using a good antivirus solution and a JavaScript blocker are the best ways to keep your Mac safe from SPOILER. Keeping your Mac locked down when you’re away from a trusted network is of course also a good idea, too; for tips on that, have a look here.
How can I learn more?
 SPOILER was a topic on episode 72 of the Intego Mac Podcast. Every week, Intego’s experts discuss Apple security and privacy topics on the podcast, so be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
SPOILER was a topic on episode 72 of the Intego Mac Podcast. Every week, Intego’s experts discuss Apple security and privacy topics on the podcast, so be sure to subscribe to make sure you don’t miss any episodes. You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
You can also follow Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).
Spoiler Alert sign photo by Jason Eppink is licensed under CC BY 2.0; cropped and resized. Meltdown and Spectre logos by Natascha Eibl via meltdownattack.com (CC0; public domain). xkcd #1938 by Randall Munroe is licensed under CC BY-NC 2.5 with the clarification, “This means you’re free to copy and share these comics (but not to sell them).”