New OSX/Crisis Variant Invokes Pope Francis
Posted on
by
Arnaud Abbati
A new sample of OSX/Crisis, the too popular Da Vinci rootkit from Hacking Team, reached our Malware Lab during the weekend. We currently do not have information about the origin of the file on VirusTotal, named “Frantisek,” but it is an Eastern European first name meaning Francis. Could it be related to Pope Francis?
Like the previous variants, OSX/Crisis.C is delivered through a dropper that installs silently, without requiring a password, and works on Mac OS X 10.5, 10.6, and 10.7. However, Hacking Team has updated some of the dropper code and the backdoor configuration file format.
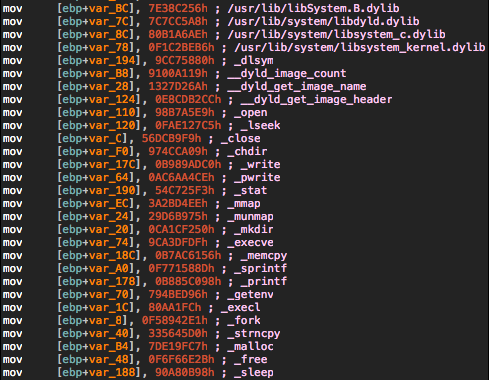
The dropper executes an unusual segment: __INITSTUB. The original entry point EIP points to this code segment before reaching the almost empty _main function of the program. For this reason, an incautious researcher using a debugger could get infected without even noticing it. While it uses a different way to resolve system symbols, it crashes on OS X Mountain Lion or OS X Mavericks (segmentation fault). This might be a 64-bit bug in the malware.
Following is a screenshot of the resolved symbols hash of the dropper in IDA:
When the dropper runs successfully, it hides the following files in the user’s home directory (in the Library/Preferences folder), inside a fake application bundle called OvzD7xFr.app:
- 1 backdoor: 8oTHYMCj.XIl (32-bit)
- 1 configuration file: ok20utla.3-B
- 2 kernel extentions: Lft2iRjk.7qa (32-bit) and 3ZPYmgGV.TOA (64-bit)
- 1 scripting addition: EDr5dvW8.p_w (FAT)
- 1 XPC service: GARteYof._Fk (FAT)
- 1 TIFF image, a System Preferences icon, ripped of Linkinus preferences panel: q45tyh
Then it executes the backdoor and finishes the installation by creating a LaunchAgent file, com.apple.mdworker.plist.
Similar to OSX/Crisis.B, this binary is obfuscated using MPress packer. It doesn’t run on OS X 10.9 as it is linked against the Apple System Profiler private framework, SPSupport, which is now 64-bit only; an “Image not found” exception is raised, and then it crashes. Furthermore, on a supported target, the backdoor simply uninstalls its files and quits. This could be related to a corrupted configuration file (the sample one starts with NULL bytes).
Other than a few new tricks, features implemented by the backdoor component are similar to previous variants: it patches the Activity Monitor application to hide itself, takes screenshots, captures audio and video, gathers user locations, connects to WiFi hotspots, syncs collected data with a Command and Control (C&C) server, and tricks the user using social engineering to gain System Administrator privileges and drop its rootkit.
At the time of this writing, the overhaul detection rate on VirusTotal is very low.
Intego VirusBarrier with up-to-date malware definitions protects Mac users against this malware, detected as OSX/Crisis.C.