New OSX/Crisis or Business Cards Gone Wild
Posted on
by
Arnaud Abbati
In these days of computer conspiracies, the Mac is not left out. A new variant of Remote Control System, Hacking Team’s spyware, landed on VirusTotal with a detection rate of 0 out of 47 scanners.
RCS, also known as OSX/Crisis, is an expensive rootkit used by governments during targeted attacks. It collects audio, pictures, screenshots, keystrokes and report everything to a remote server. It’s known to be delivered through grey market exploits.
The dropper filename, Biglietto Visita, is Italian for business card. Like OSX/Crisis.A, the code is in a dedicated section and uses low-level system calls to deploy the spyware: a backdoor and its encrypted configuration, an image, a scripting addition and the kernel extensions.
To avoid antivirus detection, the backdoor is now obfuscated using MPress packer. We can use gdb or Volatility to dump the unpacked binary. Complete analysis is in progress, as it is another story to put the symbols in place, but here you have an excerpt of the decrypted configuration file:
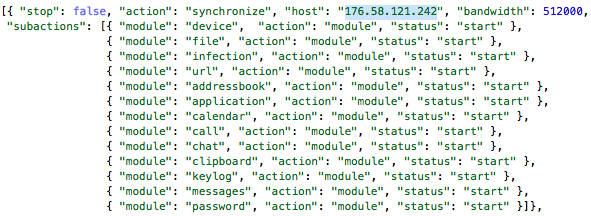
As you can see, our infected machines have good reasons to communicate with 176.58.121.242 (we also have packet captures to decrypt). At the time of this writing, this Linode UK host is online and moderates unwanted targets quickly (remote uninstall).
As is, the backdoor do not trigger the social-engineering privilege escalation, or load the kernel extensions.
Should you feel concerned by government targeted attacks, or recently received a 200k€ business card, then look for those files in your Home folder and your Startup Disk:
- Library/LaunchAgents/com.apple.UIServerLogin.plist
- Library/Preferences/2Md1ctl2/0T4Nn2U0.tze
- Library/Preferences/2Md1ctl2/5KusPre5.vAl
- Library/Preferences/2Md1ctl2/Contents/Info.plist
- Library/Preferences/2Md1ctl2/Contents/Resources/9uW_anE9.cIL.kext/Contents/Info.plist
- Library/Preferences/2Md1ctl2/Contents/Resources/9uW_anE9.cIL.kext/Contents/MacOS/9uW_anE9.cIL
- Library/Preferences/2Md1ctl2/hFSGY5ih.rfU
- Library/Preferences/2Md1ctl2/q45tyh
- Library/Preferences/2Md1ctl2/WaAvsmZW.EMb
- Library/Scripting Additions/UIServerEvents/Contents/Info.plist
- Library/Scripting Additions/UIServerEvents/Contents/MacOS/0T4Nn2U0.tze
- Library/Scripting Additions/UIServerEvents/Contents/Resources/UIServerEvents.r
Intego VirusBarrier with up-to-date malware definitions protects Mac users against this malware, detected as OSX/Crisis.B.