New Cross-Platform Backdoor Trojans Used in Targeted Attack
Posted on
by
Lysa Myers
Security researchers have discovered three trojan horse applications, now posted to VirusTotal, which appear to be part of a targeted attack for both Mac OS X and Windows machines. Likely found in pirated software distributed via BitTorrent trackers and other sites containing links to pirated software, these trojans act as backdoors on an affected user’s system, and are found bundled with copies of legitimate commercial applications.
When the files as shown below are run, each tries to contact a Command and Control (C&C) server to await commands from the attacker.
AppDelete.app.zip
SHA1 : 8bbbc10bf35ac5c9ba768462cbf864713ff740fe
![]()
Img2icns.app.zip
SHA1 : 14bc618b68e17a1ed79bb786e7d33efe21c03b84
![]()
CleanMyMac.app.zip
SHA1 : 6819dd010b463d30cc94b33547bb4c2d95dd672f
![]()
Inside each of the application folders we can see the invisible backdoor, .launchd.app, which is copied to the user’s Home folder and launches when the user double-clicks on the trojan application. It also launches the original commercial applications corresponding to the icon used to entice the target, which are embedded in each of the trojan application’s resources, disguising its bad activity.
The .launchd.app application has a simple keylogger that communicates with the C&C server. Persistence is achieved by creating a LaunchAgent, which launches the backdoor .launchd.app at every login:
- ~/Library/LaunchAgents/apple.launchd.plist
The backdoor files are removed from the commercial application at the first launch of the backdoor, attempting to hide the trojan’s trail. Affected users cannot effectively see where the backdoor came from after the first launch.
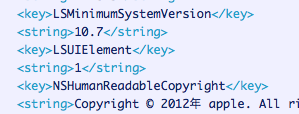
The Mac variant uses 64 bits code without any code signing, and it is only compatible with OS X versions 10.7 and 10.8.
Similar to OSX/Leverage, this trojan inhibits the Dock icon and Command-Tab application switching when the backdoor is launched, making it more difficult for a user to spot.
The trojan files’ use a copyright, but it’s poorly written (including a strange character and “Apple” being in lower-case), so it is clearly not by the original authors of the valid apps they try to imitate.
Intego VirusBarrier with up-to-date virus definitions protects Mac users against this malware, detected as OSX/Icefog.A. While this is known to be affecting users, this is considered to be a low-risk threat at this time, as it appears to be a targeted attack.
____
Update – September 30, 2013
Intego has received several reports from concerned customers who read this post and believe that the valid applications are trojans. It is important to note that the legitimate apps the trojans imitate do not try to surreptitiously install malware. Likely distributed via sites containing links to pirated software, the trojan files’ use a copyright that is poorly written and includes an odd character with “apple” (sic) being lower-case.