New Mac Trojan Discovered Related to Syria
Posted on
by
Lysa Myers
A new Mac Trojan has been discovered that creates a backdoor on an affected user’s machine. It was found on VirusTotal, sent by a user in Belarus. At the time of writing, the Command and Control (C&C) server is down and no longer sending commands to affected users. This appears to be a targeted attack, though the method of delivery is not yet known. So, while this has been affecting users in the wild, the overall threat level appears to be low.
The Trojan is an application that is disguised as a picture – the .app file-extension is not visible by default.
At this time, we are unaware how it is sent to affected users. The malware could likely be sent by email or placed on a website as part of a watering hole attack, for instance. Depending on how the file is received, the behavior of the file in OS X may be slightly different.
In some cases, there will only be an alert from Gatekeeper if the user clicks on the application if it came from a download with a quarantine bit set. There are several ways of downloading a file that would set the quarantine bit; for example, apps downloaded from the browser or an email client. Apps from other sources, such as file servers, external drives, or optical discs will not set the quarantine bit, unless the apps were originally downloaded from the Internet and had the quarantine bit set at that time.
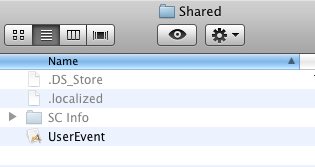
When run, the Trojan copies itself to /Users/Shared/UserEvent.app
MD5 6a36379b1da8919c1462f62deee666be
SHA-1 40b34e91cde683a567974750d1c5c9bcb09a87bb
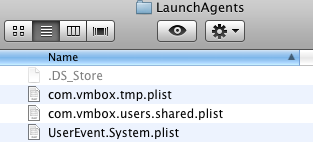
It also creates a LaunchAgent in ~/Library/LaunchAgents/UserEvent.System.plist to launch the application /Users/Shared/UserEvent.app
The Mac Trojan hides itself from the Dock and Cmd-Tab Application switching. It then opens the JPEG image inside the Application bundle with the standard OS X application Preview, which fools the user into thinking that it was just an image file.
Once it’s installed, the Trojan connects to the C&C server on port 7777.
The Trojan application installs a permanent backdoor that allows the attacker to send a variety of commands. In testing, we observed the C&C receiving a variety of system information about the affected machine, sending Pings to monitor the connection, and trying to download the following image file to the machine, among other commands.
Intego VirusBarrier with current virus definitions protects Mac users against this malware, detected as OSX/Leverage.A. While this is known to be affecting users, this is considered to be a low-risk threat at this time, as it appears to be a targeted attack. This rating may be changed as more information comes to light. If possible, it’s advised that users keep all their software, particularly operating system, browsers and browser plugins (such as Flash and Java if applicable) up to date as exploits are common ways for such attacks to spread.