Month in Review: Apple Security in September 2017
Posted on
by
Joshua Long
So much has happened in the past month; where to begin? We’ve got news about Apple’s latest operating systems, a Keychain password-stealing vulnerability affecting macOS—including the brand new High Sierra—and could a “dolphin attack” hijack Siri? Keep reading to find out!
Updates for Every Apple Operating System
 If you’ve got a relatively recent Mac, iPhone, iPad, iPod touch, Apple TV, or any Apple Watch, then Apple’s got an update for you!
If you’ve got a relatively recent Mac, iPhone, iPad, iPod touch, Apple TV, or any Apple Watch, then Apple’s got an update for you!
In September, Apple released major updates for all of its current operating systems, each of which contains security fixes:
- macOS High Sierra 10.13 is available for compatible Macs
- iOS 11 (now up to 11.0.1) is available for compatible iOS devices
- tvOS 11 is available for compatible Apple TVs
- watchOS 4 is available for all versions of the Apple Watch
For further details, see Apple Releases macOS High Sierra, iOS 11 and more with Security Fixes.
You can also check out Google’s Project Zero blog for some (really geeky and highly technical) details about several Wi-Fi vulnerabilities that were addressed in iOS 11.
Apple also released several other software updates that fix security vulnerabilities:
- Safari 11 (included with macOS High Sierra; also available for Sierra and El Capitan)
- iTunes 12.7 (for OS X Yosemite and later, and Windows 7 and later)
- macOS Server 5.4 (for macOS High Sierra)
- Xcode 9 (for macOS High Sierra and Sierra)
- iCloud for Windows 7.0 (for Windows 7 and later)
For technical details about the security bugs that were mitigated, see Apple’s security updates page.
Secure Kernel Extension Loading is Not So Secure
The new macOS High Sierra includes a feature which Apple is calling User-Approved Kernel Extension Loading (also known as Secure Kernel Extension Loading, or SKEL). The feature, described by Apple in a Technical Note, is supposed to make it more difficult for an attacker to load powerful kernel extensions into the operating system.
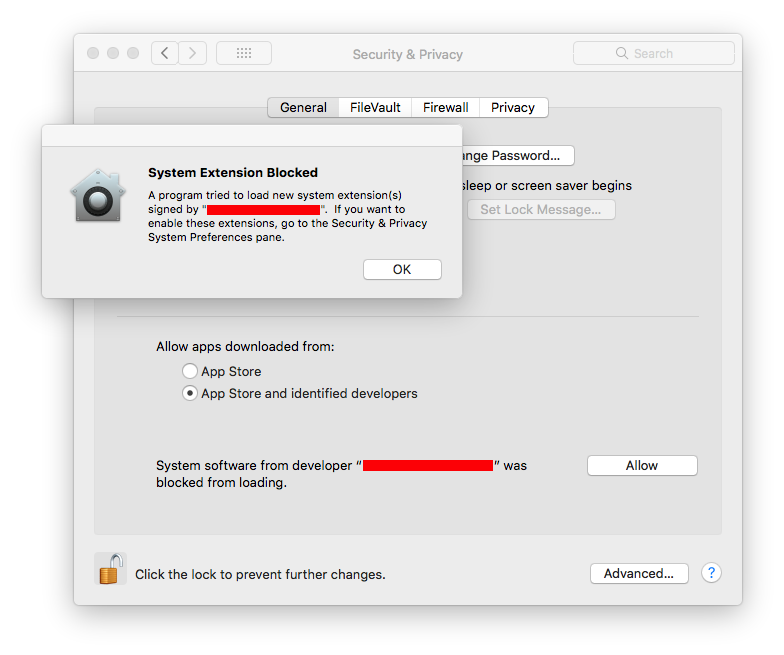
In High Sierra, Apple made it harder to install kernel extensions. Image: Apple
Mac security researcher Patrick Wardle has discovered that High Sierra’s SKEL is, unfortunately, not so secure after all, at least in its initial implementation.
Wardle notes that although Apple has done several things to make it more difficult for kernel extensions to be installed surreptitiously in High Sierra, all it takes is for an attacker to find a single flaw to bypass those protections, and Wardle found just such a flaw.
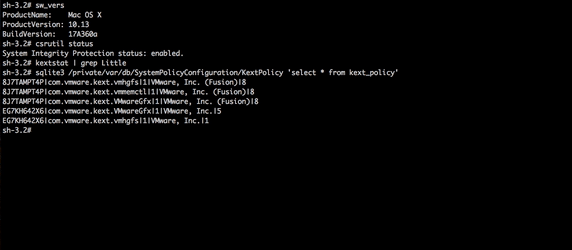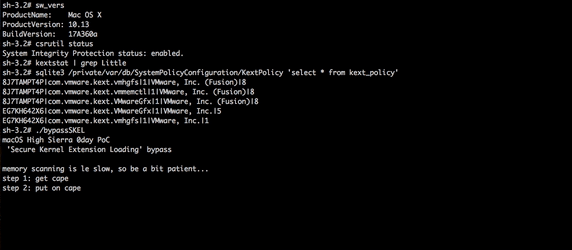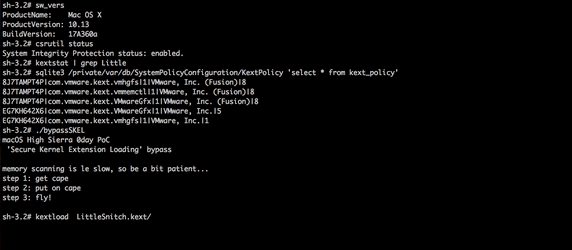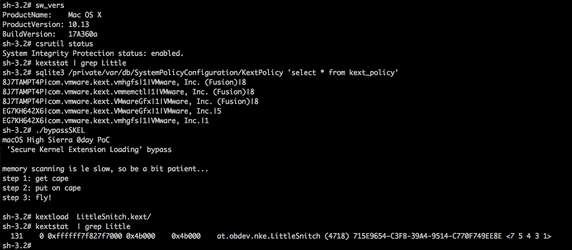 Wardle demonstrates his skills by bypassing SKEL. Image credit: Wardle
Wardle demonstrates his skills by bypassing SKEL. Image credit: Wardle
Since the vulnerability has not yet been patched, Wardle is holding off on releasing the full technical details of his exploit, but you can read more about his SKEL research on his blog.
Is this a reason to avoid upgrading to High Sierra? No, not at all. The advantages of having the latest Apple operating system, including improved security in other areas, make it important to migrate to High Sierra as soon as practical, if you haven’t already done so.
Mac Malware Can Steal All Your Keychain Passwords
Patrick Wardle had a busy month.
In addition to the SKEL bypass described above, Wardle also reported on a password-stealing vulnerability that he discovered in High Sierra and previous versions of macOS.
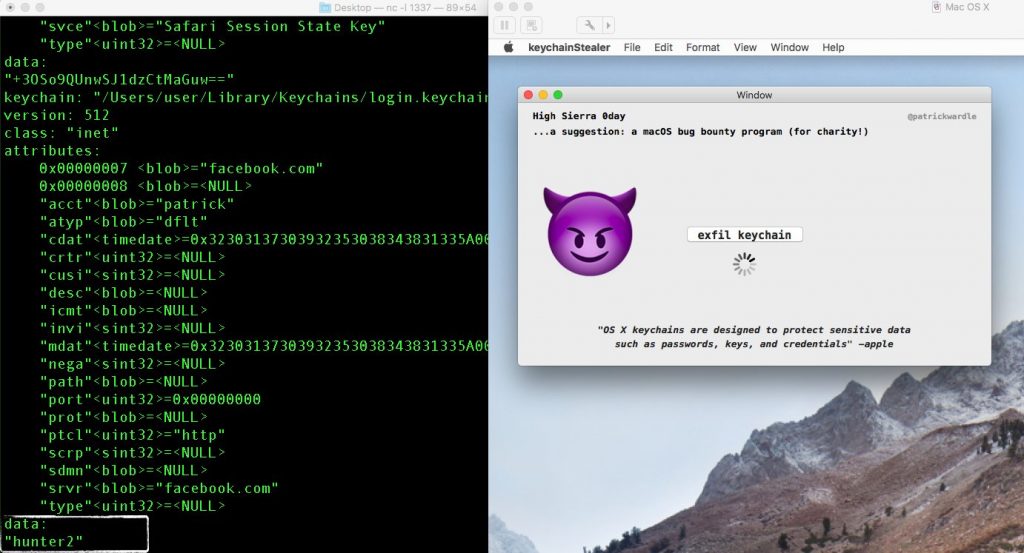 Malware can potentially steal all your Keychain passwords. Image: Wardle
Malware can potentially steal all your Keychain passwords. Image: Wardle
Each version of macOS includes a Keychain that stores passwords saved by Safari, Mail, and other applications. The Keychain is supposed to protect your passwords, and is only supposed to reveal them to the correct application as needed (or to user via the Keychain Access app).
However, the vulnerability found by Wardle could allow malware to export all of your Keychain passwords in plain text, as shown in a video demonstration.
Wardle responsibly disclosed the vulnerability to Apple along with a proof-of-concept app before High Sierra was publicly released, and he has not made any exploit code available to the public. Apple has not yet released a security update to address the issue.
There has been a lot of erroneous reporting and confusion about this story elsewhere, so be sure to read Wardle’s FAQ for further details, including some ways to mitigate the vulnerability until Apple patches it.
The take-away? Exploit code is not in the wild, so there’s no need to panic—and we can all consider ourselves fortunate that Wardle is one of the good guys.
BlueBorne
 In mid-September, a company that focuses on Internet of Things (IoT) security published information about serious Bluetooth vulnerabilities, collectively dubbed BlueBorne, that affect a wide range of Apple and other devices.
In mid-September, a company that focuses on Internet of Things (IoT) security published information about serious Bluetooth vulnerabilities, collectively dubbed BlueBorne, that affect a wide range of Apple and other devices.
Apple devices that can run the latest versions of iOS or tvOS, or any version of macOS or watchOS, are not known to be vulnerable to BlueBorne attacks.
However, several old models of iPhone, iPad, iPod touch, and Apple TV that cannot be upgraded to the latest version of iOS or tvOS remain vulnerable to exploitation. Apple has not announced any plans to release updates for affected devices.
For further details, see my article What is BlueBorne? An Apple Device FAQ.
DolphinAttack
One of the most intriguing attacks that came to light in September is called DolphinAttack.
Six researchers at Zhejiang University in China found that it was possible with all the biggest-name speech recognition systems on the market (including Apple’s Siri, Google Now, Microsoft’s Cortana, Amazon’s Alexa, as well as Samsung and Huawei voice-control systems—and even Audi’s Q3 car navigation system!) to play back spoken commands in an inaudibly high pitch to execute the commands on a nearby affected device—without anyone being able to hear the command being played back.

DolphinAttack being executed on iPhone. Image: Guoming Zhang via YouTube
Depending on a victim’s device and its voice command capabilities, a successful DolphinAttack could allow an attacker to do things such as the following:
- cause a device to visit a malicious Web site (thus potentially executing malicious code or infecting the device)
- spy on the victim (e.g. by causing the victim’s device to call another device in the possession of the attacker)
- impersonate the victim by sending unauthorized text messages or e-mails
- cause a denial of service (DoS) by enabling airplane mode
For users of iOS devices, the best mitigation against such attacks is to disable the “Hey Siri” voice-activation feature, as described here; then you can still activate Siri by holding down the Home button (or the side button on iPhone X).
For older devices such as the iPhone 6 where “Hey Siri” voice activation is only available while the device is charging, an alternative option (if you really want to leave Hey Siri enabled) is to turn your phone so the screen side faces down whenever you’re charging it, as described here.
 Although macOS High Sierra and older versions of macOS do not have a “Hey Siri” voice activation feature built in, it’s possible to create such a feature using built-in tools by following guides available online. The DolphinAttack researchers indicated that Macs are also susceptible to hearing and interpreting imperceptibly high-pitched commands.
Although macOS High Sierra and older versions of macOS do not have a “Hey Siri” voice activation feature built in, it’s possible to create such a feature using built-in tools by following guides available online. The DolphinAttack researchers indicated that Macs are also susceptible to hearing and interpreting imperceptibly high-pitched commands.
For more information on DolphinAttack, you can read the technical journal synopsis and the full academic journal paper (PDF).
Your Mac’s Firmware May Be Outdated
On Friday, Duo Security published a blog post and an accompanying white paper (PDF) reporting that a surprisingly high number of Macs may be running outdated firmware.
If a Mac’s Unified Extensible Firmware Interface (UEFI, or simply EFI) firmware is outdated, it may be susceptible to serious vulnerabilities of a similar nature to Thunderstrike and Sonic Screwdriver (mentioned in our March month-in-review article).
Of the 73,324 in-production Macs that Duo’s researchers tested, overall 4.2% (about 3,080) of those Macs were not running the expected firmware version (based on the hardware model, OS version, and EFI version released with that OS version).
Worse, certain models of Macs were far less likely than average to be running updated firmware.

These Macs are more likely to have outdated firmware. Images: Apple via EveryMac
The report specifically calls out several top offenders, including the 21.5-inch iMac (4K, Late 2015), which “has the highest occurrence of incorrect EFI firmware with 43% of systems running incorrect versions,” followed by three versions of the MacBook Pro (Late 2016) “with rates of deviance between 35% and 25%.”
Duo Security is preparing to release a client application called EFIgy on GitHub that can help users assess the state of their Macs’ UEFI firmware.
Incidentally, Apple also seems to recognize the importance of Macs receiving the latest firmware updates.
The newly released macOS High Sierra checks for firmware updates weekly according to an Apple spokesperson, as reported by Ars Technica.
Differential Privacy: Less Private Than You Think?
Apple indicates on its Privacy page that its operating systems use “Differential Privacy” to “scramble your data and combine it with the data of millions of others,” so Apple can “see general patterns, rather than specifics that could be traced back to you.”
Apple says it can use this anonymized data to learn things such as the energy consumption of Safari, for example.
That may not sound too terrible; however, according to new research, Apple’s Differential Privacy may not be quite as anonymous as Apple would like you to think.
Wired quotes Frank McSherry, who is “one of the inventors of differential privacy and a former Microsoft researcher,” as giving the analogy that “Apple has put some kind of handcuffs on in how they interact with your data,” but it “turns out those handcuffs are made out of tissue paper.”
The research, which primarily focused on macOS Sierra, found that the amount of data loss that Apple permits “is significantly higher than what is commonly considered reasonable in academic literature.”
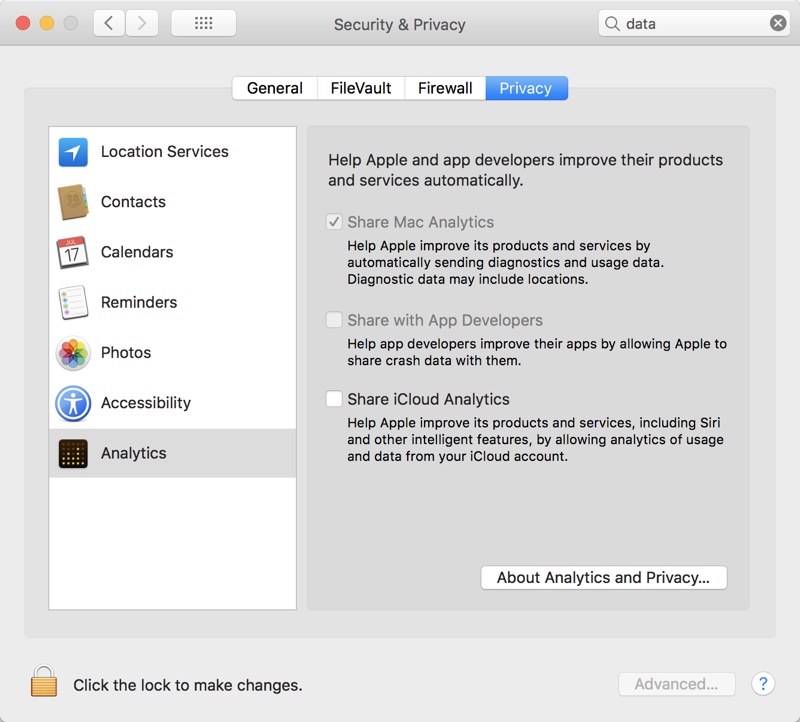
You can opt out of Analytics in macOS. Image credit: MacRumors
Thankfully, Apple does allow users to opt out of data collection for Macs as well as iOS mobile devices. For details, see Apple’s macOS article and scroll down to “Opt-out of sharing analytics,” and see also Apple’s iOS article on the subject.
For more technical information about the research, you can read Wired’s article, as well as the technical journal synopsis and the full academic journal paper (PDF).
Other Security News, in Brief
There were other important—though less specifically Apple-focused—goings-on in the security world in September. A couple highlights:
 Equifax breach: One of the “big three” credit bureaus in the United States suffered major breaches earlier this year which finally came to light in September. Numerous additional stories have surfaced after the initial breach coverage, and all signs point to a very poorly-managed security infrastructure. Even if you’re not a U.S. citizen and may not be one of the 145.5 million consumers whose sensitive information was disclosed, some of your personally identifiable information may have been compromised. Be sure to read up on the Equifax breach to see how you may be affected and what actions you can take to protect yourself. Here are just a few articles to whet your appetite:
Equifax breach: One of the “big three” credit bureaus in the United States suffered major breaches earlier this year which finally came to light in September. Numerous additional stories have surfaced after the initial breach coverage, and all signs point to a very poorly-managed security infrastructure. Even if you’re not a U.S. citizen and may not be one of the 145.5 million consumers whose sensitive information was disclosed, some of your personally identifiable information may have been compromised. Be sure to read up on the Equifax breach to see how you may be affected and what actions you can take to protect yourself. Here are just a few articles to whet your appetite:
- U.S. Federal Trade Commission: The Equifax Data Breach: What To Do
- Krebs on Security: The Equifax Breach: What You Should Know (Krebs has several other good articles on this subject that are worth reading)
- USA Today (dated October 2!): Equifax Data Breach Hit 2.5 Million More Americans Than First Believed
 D-Link router vulnerabilities: CSO Online reported that a fed-up researcher publicly disclosed a whopping ten zero-day vulnerabilities affecting the D-Link 850L 1200AC wireless router. If you use this router or a similar one, or if you think you might know someone who does, you’ll definitely want to read the report to find out how the vulnerabilities may affect you.
D-Link router vulnerabilities: CSO Online reported that a fed-up researcher publicly disclosed a whopping ten zero-day vulnerabilities affecting the D-Link 850L 1200AC wireless router. If you use this router or a similar one, or if you think you might know someone who does, you’ll definitely want to read the report to find out how the vulnerabilities may affect you.
Stay Tuned! Subscribe to The Mac Security Blog
Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month.
If you missed Intego’s previous Apple security news roundups for 2017, you can check them out here.
Have something to say about this story? Share your comments below!