Mac OS X 10.8.3 Released with Apple’s Security Update 2013-001
Posted on
by
Derek Erwin
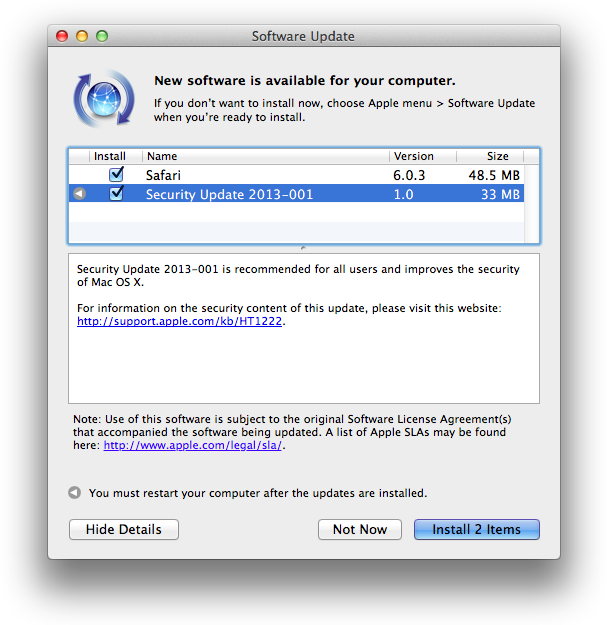
Last week, Apple released a new version of its OS X Mountain Lion operating system to Mac OS X 10.8.3. This update includes multiple bug fixes and improves the security of Mac OS X. Included with Mac OS X 10.8.3 are Safari 6.0.3 and Security Update 2013-001, both of which address multiple security problems. For Mac users running OS X Lion, the 33 MB Security Update 2013-001 shipped alongside the Safari 6.0.3 software update.
Apple silently bundled Safari 5.1.8 with the Snow Leopard version of Security Update 2013-001. Oddly, Apple has not released any details about this update on its Apple security updates page.
Altogether, the contents of these security updates include bug fixes for Mac OS X 10.6.8, Mac OS X Server 10.6.8, OS X Lion v10.7 to v10.7.5, and OS X Lion Server v10.7 to v10.7.5, in addition to OS X Mountain Lion v10.8 to v10.8.2. Overall, a total of 21 security issues are fixed, covering 17 separate CVEs, 9 of which are related to arbitrary code execution (CVE-2013-0156 and CVE-2013-0333 include flaws impacting multiple components of Apple software).
Also included in this software update is a malware removal tool that will remove some of the most common variants of Mac malware. (Naturally, here at Intego we recommend our comprehensive Mac anti-virus software since we offer award-winning protection with timelier malware definition updates.)
Following are details provided by Apple on the security issues documented as offering remote attackers the potential for arbitrary code execution:
- CVE-2012-2088 : A buffer overflow existed in libtiff’s handling of TIFF images. This issue was addressed through additional validation of TIFF images.
- CVE-2013-0976 : A memory corruption issue existed in the handling of graphics data. This issue was addressed through improved bounds checking.
- CVE-2013-0971 : A use after free issue existed in the handling of ink annotations in PDF files. This issue was addressed through improved memory management.
- Available for Mac OS X Server 10.6.8, OS X Lion Server v10.7 to v10.7.5: CVE-2013-0156 : A type casting issue existed in Ruby on Rails’ handling of XML parameters. This issue was addressed by disabling XML parameters in the Rails implementation used by Podcast Producer Server.
- Available for OS X Lion Server v10.7 to v10.7.5: CVE-2013-0333 : A type casting issue existed in Ruby on Rails’ handling of JSON data. This issue was addressed by switching to using the JSONGem backend for JSON parsing in the Rails implementation used by Podcast Producer Server.
- Available for Mac OS X Lion Server v10.7 to v10.7.5: CVE-2013-0156 : A type casting issue existed in Ruby on Rails’ handling of XML parameters. This issue was addressed by disabling XML parameters in the Rails implementation used by Profile Manager.
- CVE-2012-3756 : A buffer overflow existed in the handling of ‘rnet’ boxes in MP4 files. This issue was addressed through improved bounds checking.
- Available for Mac OS X Server 10.6.8: CVE-2013-0156 : A type casting issue existed in Ruby on Rails’ handling of XML parameters. This issue was addressed by disabling YAML and symbols in XML parameters in Rails.
- CVE-2013-0973 : Software Update allowed a man in the middle attacker to insert plugin content into the marketing text displayed for updates. This may allow the exploitation of a vulnerable plugin, or facilitate social engineering attacks involving plugins. This issue does not affect OS X Mountain Lion systems. This issue was addressed by preventing plugins from being loaded in Software Update’s marketing text WebView.
- Available for OS X Lion Server v10.7 to v10.7.5: CVE-2013-0156 : A type casting issue existed in Ruby on Rails’ handling of XML parameters. This issue was addressed by disabling XML parameters in the Rails implementation used by Wiki Server.
- Available for OS X Lion Server v10.7 to v10.7.5: CVE-2013-0333 : A type casting issue existed in Ruby on Rails’ handling of JSON data. This issue was addressed by switching to using the JSONGem backend for JSON parsing in the Rails implementation used by Wiki Server.
Following are the remaining flaws fixed with Apple’s Mountain Lion update and Security Update 2013-001:
- CVE-2013-0966 : A canonicalization issue existed in the handling of URIs with ignorable Unicode character sequences. This issue was addressed by updating mod_hfs_apple to forbid access to URIs with ignorable Unicode character sequences.
- CVE-2013-0967 : Java Web Start applications would run even if the Java plug-in was disabled. This issue was addressed by removing JNLP files from the CoreTypes safe file type list, so the Web Start application will not be run unless the user opens it in the Downloads directory.
- CVE-2011-3058 : A canonicalization issue existed in the handling of the EUC-JP encoding, which could lead to a cross-site scripting attack on EUC-JP encoded websites. This issue was addressed by updating the EUC-JP mapping table.
- CVE-2013-0963 : An error handling issue existed in Identity Services. If the user’s AppleID certificate failed to validate, the user’s AppleID was assumed to be the empty string. If multiple systems belonging to different users enter this state, applications relying on this identity determination may erroneously extend trust. This issue was addressed by ensuring that NULL is returned instead of an empty string.
- CVE-2012-3749 : An information disclosure issue existed in the handling of APIs related to kernel extensions. Responses containing an OSBundleMachOHeaders key may have included kernel addresses, which may aid in bypassing address space layout randomization protection. This issue was addressed by unsliding the addresses before returning them.
- CVE-2013-0969 : A logic error existed in VoiceOver’s handling of the Login Window, whereby an attacker with access to the keyboard could launch System Preferences and modify the system configuration. This issue was addressed by preventing VoiceOver from launching applications at the Login Window.
- CVE-2013-0970 : Clicking on a specifically-formatted FaceTime:// URL in Messages could bypass the standard confirmation prompt. This issue was addressed by additional validation of FaceTime:// URLs.
- CVE-2012-3488 : The libxslt support in contrib/xml2 in PostgreSQL 8.3 before 8.3.20, 8.4 before 8.4.13, 9.0 before 9.0.9, and 9.1 before 9.1.5 does not properly restrict access to files and URLs, which allows remote authenticated users to modify data, obtain sensitive information, or trigger outbound traffic to arbitrary external hosts by leveraging (1) stylesheet commands that are permitted by the libxslt security options or (2) an xslt_process feature, related to an XML External Entity (aka XXE) issue.
- CVE-2012-3489 : The xml_parse function in the libxml2 support in the core server component in PostgreSQL 8.3 before 8.3.20, 8.4 before 8.4.13, 9.0 before 9.0.9, and 9.1 before 9.1.5 allows remote authenticated users to determine the existence of arbitrary files or URLs, and possibly obtain file or URL content that triggers a parsing error, via an XML value that refers to (1) a DTD or (2) an entity, related to an XML External Entity (aka XXE) issue.
Head over to Apple’s support page for more information about the OS X Mountain Lion v10.8.3 update, which includes additional information about Safari 6.0.3, too. We strongly encourage all Mac users to download and install all security updates as soon as possible – it is an essential layer of security that keeps your digital life secure.
You can update through Apple’s Software Update tool by choosing Apple menu > Software Update when ready to install. For OS X Mountain Lion v10.8.2 users, you can download the 540.46 MB update to v10.8.3 from the Apple support page. For those running OS X 10.8, you can upgrade by downloading the 793.69 MB Combo updater.