Recommended + Security & Privacy + Security News
iOS trustjacking: How attackers can hijack your iPhone
Posted on
by
Joshua Long

Have you ever plugged in your iPhone to a USB port and tapped “Trust” on your screen? You might have unknowingly given an attacker permanent access to your device—even wirelessly, and potentially even remotely.
On Wednesday morning at RSA Conference 2018, two security researchers gave a presentation that has massive security and privacy implications for users of all devices that run Apple’s iOS operating system: iPhone, iPad, and iPod touch.
In this article:
- What exactly is the “trustjacking” attack?
- Does the attacker have to be near the victim?
- Remote attack where the user is not near the trusted computer
- Remote attack where the attacker is not near the trusted computer
- What if I never tap Trust when using someone else’s computer? Am I safe?
- Why does iOS have a “Trust This Computer” dialog box?
- Do I need to tap “Trust” to charge my device?
- Are public charging stations safe?
- How can I revoke trust from computers I’ve previously trusted?
- How can I learn more?
What exactly is the “trustjacking” attack?
 The security researchers, Adi Sharabani and Roy Iarchy, presented a live demonstration of the attack. Sometime before the presentation, Sharabani had previously connected his iPhone X to Iarchy’s MacBook and tapped “Trust” in a dialog box on the iPhone—something many people do when they connect their iPhone to a computer.
The security researchers, Adi Sharabani and Roy Iarchy, presented a live demonstration of the attack. Sometime before the presentation, Sharabani had previously connected his iPhone X to Iarchy’s MacBook and tapped “Trust” in a dialog box on the iPhone—something many people do when they connect their iPhone to a computer.
During the presentation, Sharabani used his iPhone X to take a selfie with Iarchy, after which he sent a text message to their company’s CEO.
On the MacBook, Iarchy issued a command to Sharabani’s iPhone to back up its data over Wi-Fi, which is made possible by an iOS feature called iTunes Wi-Fi Sync, which works on both macOS and Windows hosts. After the synchronization was complete, Iarchy showed that both the selfie and the text message were easily accessible on his MacBook.
Great to speak with @royiarchy at #RSAConference. More important, great to see that you finally created a twitter account! pic.twitter.com/mK5gW5BZbw
— Adi Sharabani (@adisharabani) April 18, 2018
The researchers also demonstrated how an attacker could live-stream continuous screenshots from the device, effectively simulating a live video feed of what was on the iPhone’s screen. Given that iOS briefly shows the most recently typed character in password fields, it’s possible for an attacker to watch a victim type their banking or other passwords. This is effectively a clever, modern way to conduct a “shoulder surfing” attack without having to be in the same room as the victim.

Remotely observing iOS is a modern version of shoulder surfing.
One of the most concerning attacks enabled by trustjacking that Sharabani and Iarchy demonstrated was the ability to replace an iOS app with a malicious version that had an identical icon, which appeared in the same location as the original. In their demonstration, it took less than a second for the iPhone’s legitimate Facebook app to get replaced with a repackaged version.
By repackaging an app, an attacker can insert functionality of their choosing, including functions only available via private APIs that Apple doesn’t allow to be used in App Store apps.
![]()
Is this the real Facebook app or a maliciously modified version?
Imagine, if you will, a couple of scenarios in which replacing an app with a compromised version could be a serious security and privacy concern.
![]() Many people use secure messaging apps, like Signal, for instance, to transmit messages that only the recipient can decrypt. If an attacker were to replace your iPhone’s secure messaging app with a malicious repackaged version, all of your “secure” messages could be siphoned off and made available for the attacker—before they were ever encrypted in the first place.
Many people use secure messaging apps, like Signal, for instance, to transmit messages that only the recipient can decrypt. If an attacker were to replace your iPhone’s secure messaging app with a malicious repackaged version, all of your “secure” messages could be siphoned off and made available for the attacker—before they were ever encrypted in the first place.
It’s also possible for repackaged apps to do things like secretly take pictures of you using your front-facing camera, record audio using your microphone, and more; iOS developer Felix Krause shared examples of similar behavior in October 2017.
 Krause shows how a hijacked camera can reveal a user’s emotion.
Krause shows how a hijacked camera can reveal a user’s emotion.
Unlike MacBooks and iMacs, iOS devices do not include camera-in-use indicator lights, so a victim would have no way of knowing that they were being spied upon in this manner.
Does the attacker have to be near the victim?
After an iOS user has trusted a computer, at any time in the future that computer can be used to carry out attacks when the device is either connected via USB, or when the iOS device and the computer are connected to the same Wi-Fi wireless network.
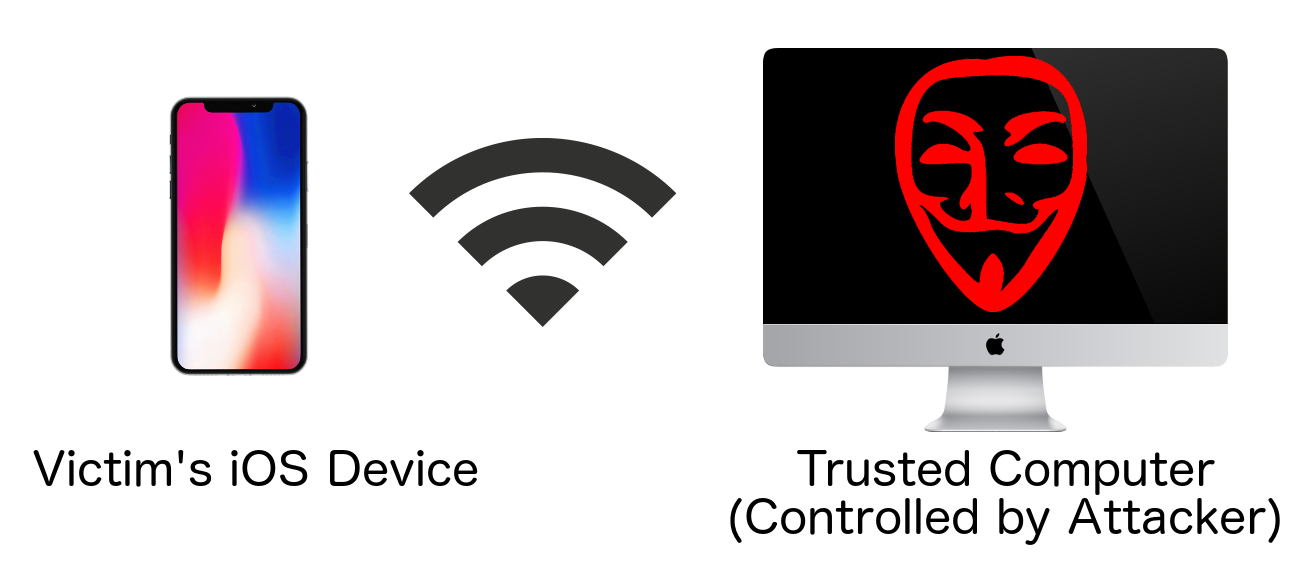
However, remote attacks are also possible.
Remote attack where the user is not near the trusted computer
![]() Sharabani and Iarchy have confirmed that it’s possible to carry out attacks when the iOS device is elsewhere in the world, so long as the iOS device is connected to a VPN of the attacker’s choosing.
Sharabani and Iarchy have confirmed that it’s possible to carry out attacks when the iOS device is elsewhere in the world, so long as the iOS device is connected to a VPN of the attacker’s choosing.
This attack scenario requires a combination of trustjacking—the user having once trusted a computer now controlled by the attacker—and what the researchers called a malicious profile attack (which implies that the victim has fallen for a social engineering attack and installed a mobileconfig profile created by the attacker).
Remote attack where the attacker is not near the trusted computer
If an attacker has compromised (hacked into) a trusted computer, then the attacker could potentially execute an attack from a remote location, as explained below.
What if I never tap Trust when using someone else’s computer? Am I safe?
 Sharabani and Iarchy also described an attack scenario in which a legitimately trusted computer—perhaps the victim’s home computer—had become compromised by an attacker. If an attacker can surreptitiously control a compromised computer from a remote location, then the attacker could carry out these attacks from anywhere in the world.
Sharabani and Iarchy also described an attack scenario in which a legitimately trusted computer—perhaps the victim’s home computer—had become compromised by an attacker. If an attacker can surreptitiously control a compromised computer from a remote location, then the attacker could carry out these attacks from anywhere in the world.
Thus, it’s important to maintain the security of your own Mac or Windows PC that you’ve allowed your iOS device to trust.
Why does iOS have a “Trust This Computer” dialog box?
The first time a computer attempts to access data from your iPhone or other iOS device, you will see a dialog box on your device’s screen, which says, “Trust This Computer? Your settings and data will be accessible from this computer when connected.” The dialog box presents two options: “Trust” and “Don’t Trust.”
![Trust This Computer? Your settings and data will be accessible from this computer when connected. [Trust] [Don't Trust] Trust This Computer? Your settings and data will be accessible from this computer when connected. [Trust] [Don't Trust]](https://www.intego.com/mac-security-blog/wp-content/uploads/2017/09/ios10-iphone7-trust-computer-alert.jpg) The iOS “Trust This Computer?” dialog box
The iOS “Trust This Computer?” dialog box
By displaying this prompt, Apple gives iOS users the choice whether the connected computer should be allowed to access the device’s settings and data.
However, the dialog box implies that it’s necessary for there to be a physical connection between the iOS device and the computer via a Lightning to USB cable. Most iOS device users are unaware that “connected” can also mean “on the same Wi-Fi network.”
As of iOS 11, tapping Trust now requires you to enter your device’s unlock passcode. According to Sharabani and Iarchy, Apple implemented this mitigation after the researchers began working with Apple to disclose the vulnerability in July 2017. Even so, many users do not understand the nature or degree of the trusted relationship, and may be trusting computers too freely.
Do I need to tap “Trust” to charge my device?
 No! If all you want to do is charge your device’s battery, you should always tap the “Don’t Trust” button, not the “Trust” button. Charging your battery does not require a trusted relationship.
No! If all you want to do is charge your device’s battery, you should always tap the “Don’t Trust” button, not the “Trust” button. Charging your battery does not require a trusted relationship.
If you decide later that you need to exchange data between your iOS device and a computer you had previously chosen not to trust, simply reconnect your device via USB and you’ll be presented with the “Trust This Computer?” dialog box again.
Are public charging stations safe?
If you ever connect your iPhone to something that doesn’t appear to be a computer, for example a public charging station, you shouldn’t get a “Trust This Computer?” prompt. If you see such a prompt at a public charging kiosk, you may in reality be connected to a hidden computer on the other end—one that’s designed to steal data from connected devices while they’re charging.
The safest solution is to avoid public charging terminals altogether. They can potentially attempt to hack your device, via methods similar to those described in this article. Even a seemingly innocuous-looking cable can potentially try to hijack your device, as discussed in episode 124 of the Intego Mac Podcast (from 20:47 to 22:02). There are other potential non-security concerns as well, such as the possibility of a malfunctioning cable, charger, or electrical outlet that can cause a short and physically damage your device.
How can I revoke trust from computers I’ve previously trusted?
 After learning about this attack, you may find yourself trying to remember how many computers you’ve previously trusted when you probably didn’t need to, or that should no longer have a trusted relationship with your iOS device.
After learning about this attack, you may find yourself trying to remember how many computers you’ve previously trusted when you probably didn’t need to, or that should no longer have a trusted relationship with your iOS device.
Unfortunately, Apple does not offer users a way to see a list of all computers to which they’ve previously connected their iOS device, which means you cannot selectively revoke trust from individual computers.
What you can do instead is to mass-revoke trust from all previously connected computers by going into the Settings app, tapping General, Reset, and then Reset Location & Privacy.
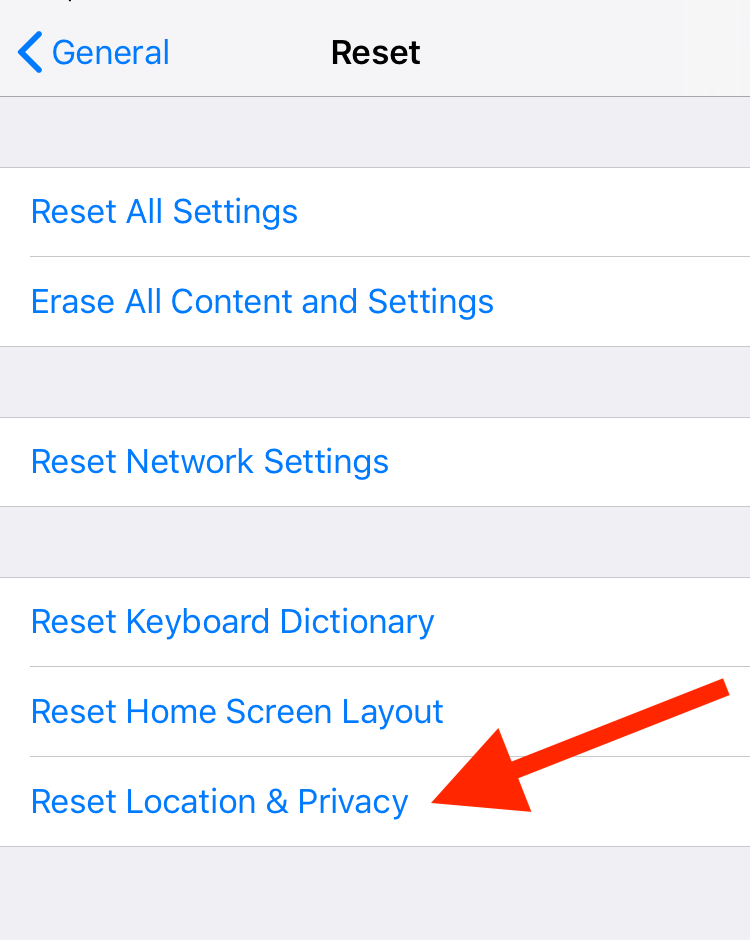
“Reset Location & Privacy” untrusts all previously trusted computers.
Note that this has some temporarily inconvenient side effects; for example, you’ll need to individually reauthorize each and every app to know your location or to use your camera. However, the minor inconvenience is well worth it to protect your security and privacy.
How can I learn more?
For more information about trustjacking, including some video demonstrations, you can read Iarchy’s blog post. We also discussed trustjacking on episode 28 of the Intego Mac Podcast.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()
iPhone X image by Rani Ramli. Charging iPhone battery image by rawpixel. Shoulder surfing image compiled by Josh Long, based on sitting geek image via Pixabay and standing person image by James Heilman, MD. iMac image by Rafael Fernandez. Wi-Fi icon image via BrandEPS.