Major Authentication Security Flaw Reported in macOS High Sierra [Update]
Posted on
by
Jay Vrijenhoek
Today, software developer Lemi Orhan Ergin posted a tweet directed at Apple Support, outlining the discovery of a major security flaw in macOS High Sierra. It appears this flaw was not properly disclosed to Apple, so as of right now there is no fix and the latest beta versions appear to be affected as well, though reports on this are mixed. Typically we would wait to report on this until a fix is underway, but as this news is spreading fast, we thought it would be better to offer a temporary fox for this flaw instead.
What’s the flaw?
macOS 10.13 High Sierra users who leave their Mac unlocked can have anyone with physical access take complete control. Typically any important settings are locked and require an administrator name and password to access.
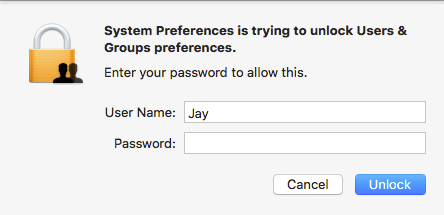
The problem is that this authentication process is broken. Anyone can use the username “root” with a blank password and hit return or click the Unlock button. The first time macOS will not allow it, but hitting return or clicking the button again will enable the root user and let anyone log in!
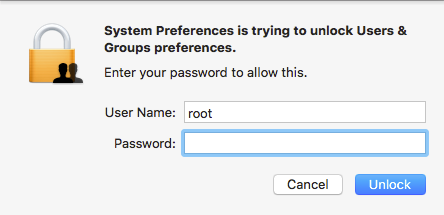
This trick appears to work on any System Preferences pane that is locked as well as other places in macOS that require authentication to access. To make matters worse, once the root user is enabled, someone can log you out or restart your machine, and then log in to the macOS as root user, having complete control over all your data.
What can I do to prevent this from happening?
First and foremost, access to your Mac has to be locked down the second you walk away from your Mac. This can be done with a screensaver password, by logging out, shutting down or locking your screen with the new High Sierra menu option (Apple menu > Lock Screen). Not giving anyone the chance to exploit this flaw is the best way to prevent it at the moment. It is currently not known if this flaw is exploited in the wild, but malware could very easily implement exploits.
The best way to protect yourself from this flaw, apart from the above mentioned suggestions, is to enable the root user on your Mac and set a strong, unique password. If the root user is already enabled, this flaw doesn’t work. The root user should never be enabled if you don’t need it, but this is a valid scenario in which said advice can be ignored.
To enable the root user on your Mac, do the following:
- Open the Directory Utility application. Use spotlight or find it in System > Library > CoreServices > Applications.
- Click the lock and authenticate with your credentials.
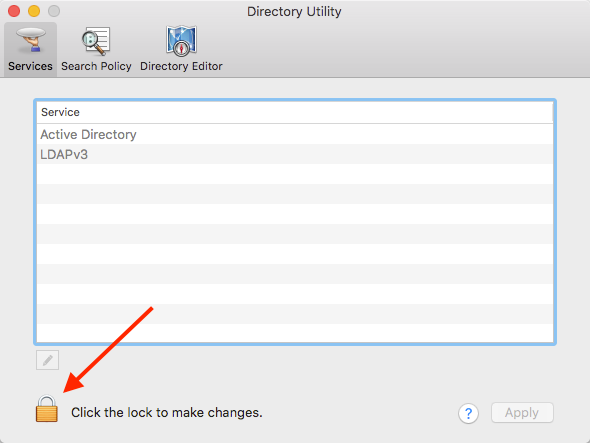
- Once authenticated, from the Edit menu, select “Enable Root User”
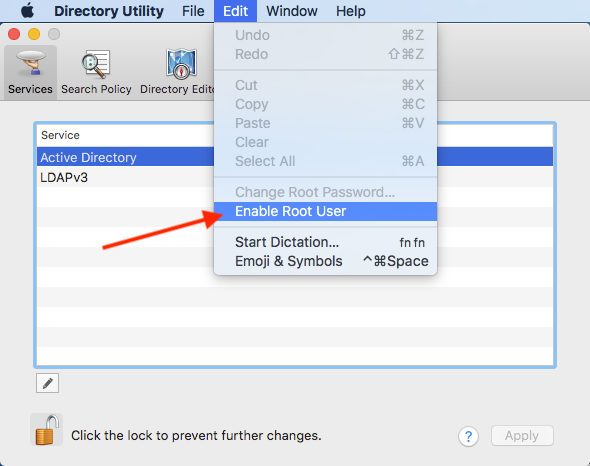
- Pick a strong and unique password!
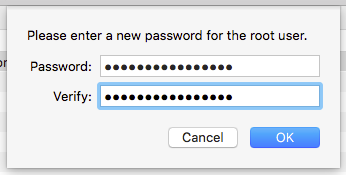
Click OK when the password has been set and lock the Directory Utility before quitting it.
Am I all set now?
Not quite. Enabling the root user, even with a strong and unique password should not be done unless it’s needed (which is virtually never for the vast majority of users). As soon as Apple releases a fix for this flaw, the root user should be disabled again through Directory Utility. Keep a close eye on software updates and read their descriptions to see if this flaw was one of the addressed issues. Of course, we at The Mac Security Blog will let you know as well when this flaw has been patched.
If you are not comfortable enabling the root user (superuser) account on your Mac, make sure it is locked down tight, so no one can even attempt to exploit this flaw. It’s also important to note that this flaw is present only on macOS High Sierra 10.13 and 10.13.1.
Editor’s Update: On November 29, Apple released Security Update 2017-001 for macOS High Sierra 10.13.1 to address the security flaw discussed in this post.
Apple’s security team said the following about this update:
An attacker may be able to bypass administrator authentication without supplying to administrator’s password. […] A logic error existed in the validation of credentials. This was addressed with improved credential validation.
macOS High Sierra users can download Security Update 2017-001 by visiting Apple’s support download page. When you install Security Update 2017-001 on your Mac, the build number of macOS will be 17B1002.
November 30 Update: Apple has released steps Mac users can take to verify that your computer has Security Update 2017-001. To confirm that your Mac has Security Update 2017-001, follow these steps:
- Open the Terminal app, which is in the Utilities folder of your Applications folder.
- Type the following command and press Return:
what /usr/libexec/opendirectoryd
- If Security Update 2017-001 was installed successfully, you will see one of these project version numbers:
opendirectoryd-483.1.5 on macOS High Sierra 10.13
opendirectoryd-483.20.7 on macOS High Sierra 10.13.1
As Apple mentioned, if you require the root user account on your Mac, you will need to re-enable the root user and change the root user’s password after this update.