Before the Weekend: Update Flash Player, Office for Mac
Posted on
by
Derek Erwin
Online threats capitalize on software vulnerabilities, so it’s best to patch known holes as quickly as possible. This means installing Apple’s and other third-party software security updates promptly.
Before heading into the weekend, there are two very important security updates you should be aware of and install immediately. First is for Adobe Flash Player, and the other for Microsoft’s Office for Mac.
Adobe Update: Flash Player 22.0.0.192
Adobe Systems has released Flash Player 22.0.0.192 with security updates to patch multiple vulnerabilities, most of which could lead to arbitrary code execution, as well as a fix for the zero-day exploit reported on Tuesday.
Adobe software affected by this updates includes the following:
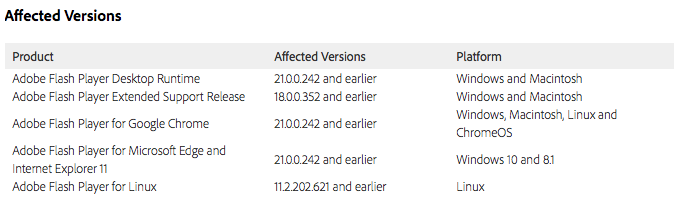
For those interested in the full list of vulnerabilities patched with these updates, see Adobe’s security bulletin (APSB16-18).
Macintosh and Windows users running Adobe Flash Player Desktop Runtime should update your software to Flash Player 22.0.0.192 (17.7 MB) as soon as possible, and Linux users should update to Flash Player 11.2.202.626. Adobe Flash Player installed with Google Chrome will be automatically updated to the latest version, which will include Adobe Flash Player 22.0.0.192 for Windows, Mac, Linux and Chrome OS.
Microsoft Update: Office for Mac 2011 14.6.5
Microsoft has released security patches with the updated Office for Mac 2011 14.6.5, resolving vulnerabilities in Microsoft Office that could allow remote code execution if a user opens a specially crafted Office file.
Microsoft also released updates for Office 2016 for Mac, which includes fixes for issues in the Office 2016 for Mac Suite that affect versions of Word, Excel, and PowerPoint.
According to Microsoft’s security team, these updates correct a critical vulnerability and users should install the security patches as soon as possible. Microsoft said:
“The most severe of the vulnerabilities could allow remote code execution if a user opens a specially crafted Microsoft Office file. An attacker who successfully exploited the vulnerabilities could run arbitrary code in the context of the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.”
Common Vulnerabilities and Exposures identifies the vulnerability as follows:
CVE-2016-0025: Microsoft Word 2007 SP3, Office 2010 SP2, Word 2010 SP2, Word 2013 SP1, Word 2013 RT SP1, Office 2016, Word 2016, Word for Mac 2011, Word 2016 for Mac, Office Compatibility Pack SP3, Word Automation Services on SharePoint Server 2010 SP2, Word Automation Services on SharePoint Server 2013 SP1, Office Web Apps 2010 SP2, Office Web Apps Server 2013 SP1, and Office Online Server allow remote attackers to execute arbitrary code via a crafted Office document, aka “Microsoft Office Memory Corruption Vulnerability.”
Microsoft addressed the vulnerability by correcting how Office handles objects in memory. Office for Mac users should install the update at your earliest convenience.
Office for Mac 2011 users can update your software by using Microsoft’s AutoUpdate application, or by visiting the Microsoft Download Center to download and install Office for Mac 2011 14.6.5 (113.4 MB).
Office 2016 for Mac users can get the updates by using Microsoft AutoUpdate. To do this, open a Microsoft Office program, and then click “Check for Updates” on the Help menu.