¡Ay, MaMi! New DNS-hijacking Mac malware discovered
Posted on
by
Joshua Long
UPDATE: On January 17, we added additional information about the malware’s method of persistence and another file dropped by the malware, as well as the forum user’s reported source of infection.
Very early in the morning on Friday, January 12, Mac security researcher Patrick Wardle published a report about a brand new Mac malware, dubbed OSX/MaMi.
“2018 is barely two weeks old, and already it looks like we’ve got [a] new piece of macOS malware!” Wardle said, upon introducing his analysis of OSX/MaMi.
OMG do we have the 1ˢᵗ macOS malware of 2018? and can I name it!? OSX/MaMi is undetected by AV (src: VT) infecting Macs around the world – persistently installs new root cert & hijacks DNS settings: https://t.co/kkriVSPNC7 ???☠️ …mahalo to a good friend for the ping ?
— Objective-See (@objective_see) January 12, 2018
On Thursday, a user of a computer security forum had posted asking for help with removing some malware from his Mac that another malware-removal utility wasn’t detecting.
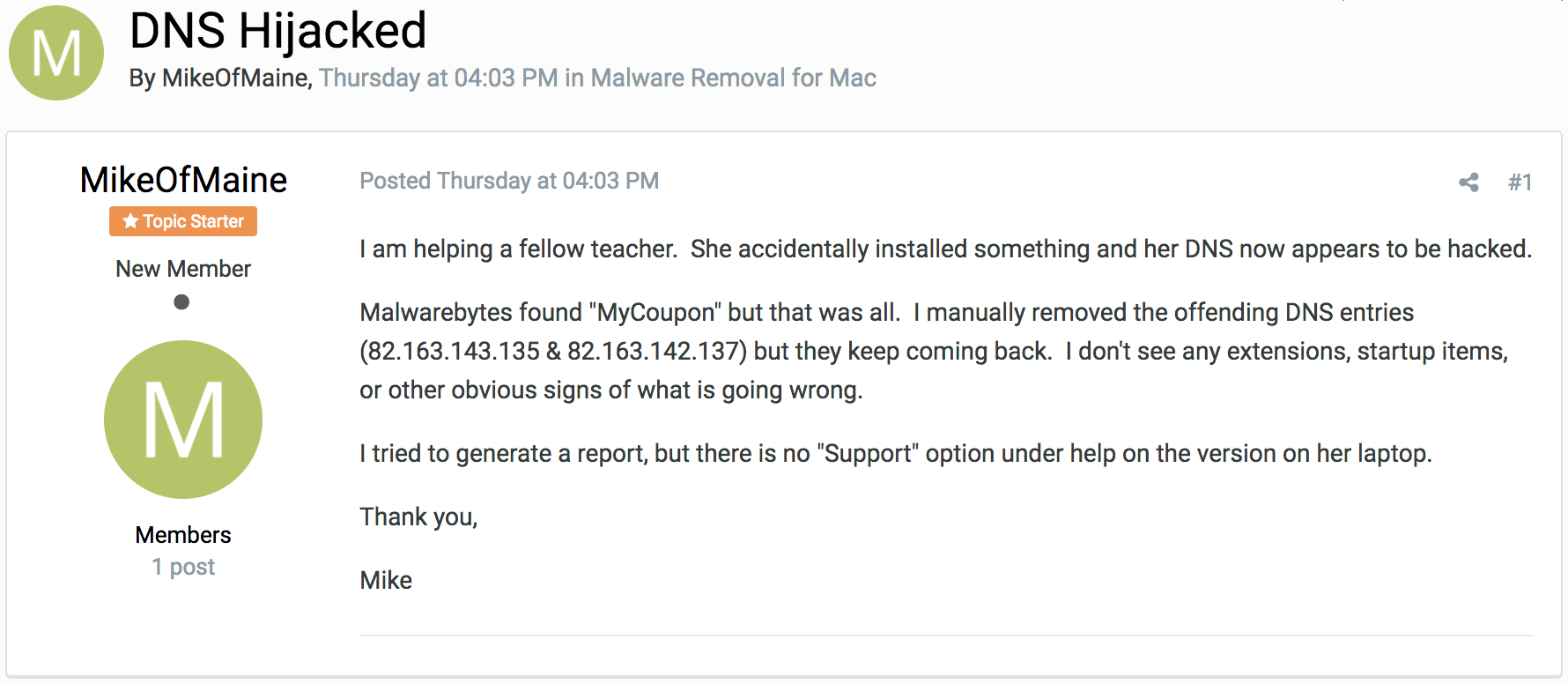
The original forum post that started the MaMi investigation.
Since neither the forum hosts nor other forum users had responded publicly, Wardle decided to do some investigating.
Intego also began analyzing the malware early Friday morning and updated its VirusBarrier antivirus definitions to detect this new malware as OSX/MaMi.A.
Following is a compilation of some interesting findings from Intego researchers, Wardle, Noar (another researcher), and Thomas Reed.
What Does the OSX/MaMi Malware Do?
The main objective of the malware is to hijack a user’s DNS.
DNS stands for domain name system, a technology used by nearly every Internet-connected device to resolve domain names to their actual Internet protocol (IP) address. For example, if you type “intego.com” into your browser, DNS is how your computer knows where to find Intego’s site.
OSX/MaMi malware attempts to hijack a victim’s DNS requests by injecting its own DNS servers into an infected system. It also installs a malicious root certificate authority (root CA) so that secure HTTPS requests can also be hijacked by the malware without scary warnings appearing in the victim’s browsers.
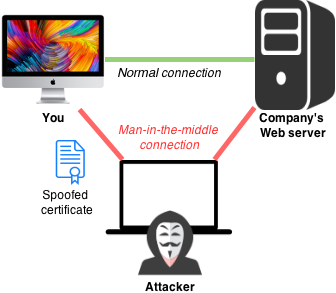 The combination of hijacking DNS and injecting a root CA make it possible for the malware creator to engage in “man-in-the-middle” (MitM) attacks against a victim. An attacker could potentially do things such as spy on everything a victim does online, see every bit of data typed into “secure” Web forms, and inject malware or advertisements into any Web page (even if the page uses HTTPS).
The combination of hijacking DNS and injecting a root CA make it possible for the malware creator to engage in “man-in-the-middle” (MitM) attacks against a victim. An attacker could potentially do things such as spy on everything a victim does online, see every bit of data typed into “secure” Web forms, and inject malware or advertisements into any Web page (even if the page uses HTTPS).
Although analysis of the malware so far has not shown any utilization of the following functions, the malware also appears to have the capability (or at least incomplete attempts at adding the capability) to execute AppleScript code, simulate mouse clicks, and take screenshots. It also appears to contain code for installing a method of persistence called a LaunchAgent (see our recent interview with Amit Server about OSX/Pirrit for more about LaunchAgents), but so far we have not observed a LaunchAgent being installed by OSX/MaMi.
UPDATE: On the forum user’s computer, the malware was installed as a LaunchDaemon—similar to a LaunchAgent—with the file path /Library/LaunchDaemons/Cyclonica.plist (note that the file name might differ on other infected systems, but one unique thing about the file name is that it doesn’t follow the standard reverse domain notation convention as discussed in the aforementioned interview with Serper about Pirrit). This LaunchDaemon plist file references a malicious file that’s downloaded to the user’s home directory, in this case ~/Library/Application Support/Cyclonica/Cyclonica (again, the folder and file names might differ on other infected systems, but will probably match the name of the LaunchDaemon plist file). Thanks to Thomas Reed for working with the forum user to obtain this information.
Why “MaMi”?
Wardle, the first researcher to write up a report on the malware, called it OSX/MaMi, so Intego has adopted the name. Although several antivirus vendors are calling it “OSX/DNSChanger,” we agree with Wardle that it’s helpful to distinguish between MaMi (which is new malware) and other DNS-modifying malware that has already been called DNSChanger in the past.
Good: detection for OSX/MaMi went from 0/59 to 26/59 on VirusTotal: https://t.co/JXSs0iRngo Bad: several AVs calling it ‘OSX/DNSChanger’ …which IMHO, is dumb as there’s an unrelated Mac malware from 2012, *already* called this (even has a wikipedia: https://t.co/VHetpnH811) ? pic.twitter.com/Aiq4EbiAy3
— patrick wardle (@patrickwardle) January 15, 2018
The name “MaMi” appears in text strings within the malware (mami_activity, loadMaMiAtPath, unloadMaMiAtPath, removeMaMiAtPath, initMaMiSettings, SBMaMiSettings, SBMaMiManager, etc.).
Mami is an Israeli term of endearment, meaning something akin to sweetie or honey; for example, a mother might call her child by that name. We’ll explain the Israel connection below.
(Incidentally, “mami” has several meanings in different cultures. Similar to the Israeli word, it is also a Spanish word that can be a term of endearment in some contexts; it can also mean mommy, beautiful woman, or young girl with whom the speaker is familiar. Mami is also a female given name in Japanese meaning “real beauty,” and it’s also the name of a noodle soup in the Philippines.)
How the Malware Spreads
At this time, it’s not known precisely how the original forum user got infected. However, several Web sites are currently hosting copies of the malware binary, so one possibility is that OSX/MaMi may be a secondary infection installed by other malware that’s already installed on a victim’s system.
UPDATE: The forum user later reported that his coworker’s computer became infected after clicking in a browser popup window: “…this was a lame method of transmission. A popup came up that she clicked and followed through with.” Thanks to Thomas Reed for working with the forum user to obtain this information.
How to Tell if Your Mac Is Infected
WARNING: Do not attempt to connect to the domain names or IP addresses below; doing so may lead to infection!
The most obvious indicators of compromise (IoCs) are that an infected computer will have the following IP addresses as DNS servers: 82.163.143․135 and 82.163.142․137.
There are a number of methods for checking which DNS servers your Mac is using.
If you’re using a wired Ethernet connection, click on the Apple menu and select System Preferences…, then click on Network, and then (if it’s not already selected) click on Ethernet (or Thunderbolt Ethernet) in the left pane. In the right pane, you’ll see a “DNS Server:” line which may contain one or more DNS IP addresses. If you see one or both of the IP addresses above that start with “82.163.” then your Mac has been infected.
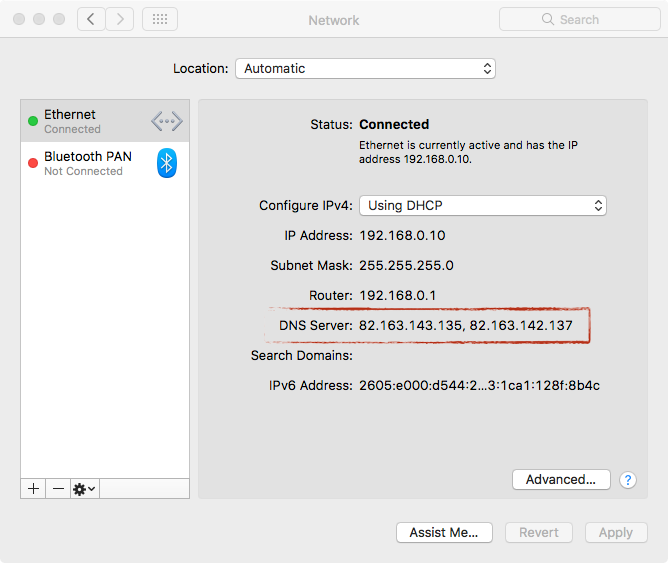
MaMi DNS servers on Ethernet. Image credit: Wardle
If you’re using a wireless network, you can copy and paste the following into the Terminal app on your Mac:
networksetup -getdnsservers Wi-Fi
If you see one of the IP addresses above that start with “82.163.” then your Mac has been infected. (Most often you’ll see the message, “There aren’t any DNS Servers set on Wi-Fi,” or if you’ve manually added DNS servers in the past you’ll see them listed.)
Another indicator of compromise is the presence of a root CA for the domain cloudguard(.)me; you can search for the word cloudguard in the Keychain Access app on your Mac, and if it appears in the results, then your Mac has been infected.
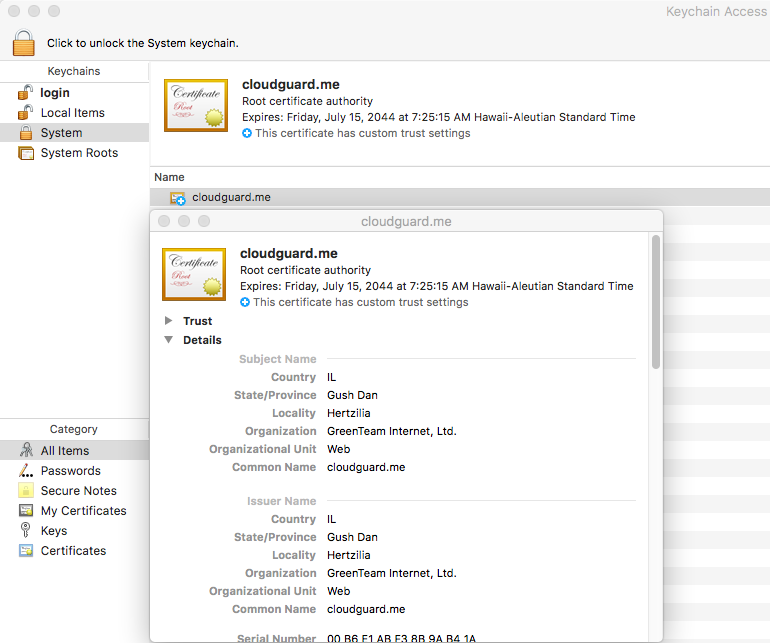
Root CA installed by OSX/MaMi. Image credit: Wardle
The Keychain Access and Terminal apps are both located in /Applications/Utilities in your Macintosh HD.
The malware may also drop files in /Library/LaunchDaemons and ~/Library/Application Support, as previously noted.
Partial instructions for manually removing the DNS servers and root CA from a Mac can be found in Wardle’s article; however, attempting to manually clean a system may be insufficient, as the forum user who originally reported the malware said that after manually removing the DNS servers they became installed again.
We strongly recommend scanning your system with Intego VirusBarrier to check for persistent infections.
Network administrators can find potentially infected systems on their network by looking for attempts to contact the following domains on port 80:
- squartera(.)info
- gorensin(.)info
- honouncil(.)info
- sincentre(.)info
- regardens(.)info
- angeing(.)info
- definitial(.)info
- humption(.)info
- lilovakia(.)info
- accessful(.)info — not known to be used by the malware variants we’ve seen, but evidently registered by one of the same people on the same date
How Long Has the Malware Been Around?
The earliest known sample of OSX/MaMi we’ve found so far was first uploaded to VirusTotal on November 15, 2017. Another sample was originally uploaded to VirusTotal on December 18, 2017. The sample analyzed by Wardle, which is still being distributed via many domains, was originally uploaded to VirusTotal on January 8, 2018, and it appears to be a more recent version.
Although this Mac malware doesn’t seem to have been in the wild for very long, Windows versions of the malware have been observed in the wild as far back as 2015, as detailed below.
Related Windows Malware
Another Mac malware researcher, Noar (@noarfromspace), made a connection between OSX/MaMi and DNSUnlocker—very similar malware that was found on Windows systems in August 2015.
@noarfromspace dug up: https://t.co/AK33MDzv16 Discusses the Windows malware ‘DNSUnlocker’ which hijacks DNS settings & installs same cert as OSX/MaMi. Guessing OSX/MaMi is a (fully re-written?) ?-version, with extra macOS-specific evilness… Also note: CloudGuard?? pic.twitter.com/rGjQn5L0ir
— Objective-See (@objective_see) January 12, 2018
Both OSX/MaMi and DNSUnlocker send DNS requests to IP addresses owned by GreenTeam Internet, a company based in Tel Aviv, Israel that claims to offer Internet safety services, “from safe Internet for kids and families, to malware and phishing protection for businesses.”
That’s interesting enough, but even more telling is that OSX/MaMi and DNSUnlocker install the exact same root CA (which is issued to GreenTeam Internet). The certificate was generated in July 2014, and it has an expiration date in July 2044.
Who’s Behind the Malware?
Several domains referenced within the malware are registered to an Anton Vodonaev, who’s supposedly located in Ukraine and whose e-mail addresses contain the name “prolone” (possibly a reference to the steroid drug of that name).
Several domains that are hosting the malware binary are registered to a Vladislav Kakoshin at a different mailing address and postal code in Ukraine.
Of course, it is entirely possible that these names may be pseudonyms and that the individual or individuals might not really be in Ukraine.
All of the domains registered to these names were registered on May 30, 2017 through the same domain name registrar.
It’s unclear what, if any, direct connection the alleged Ukrainian individuals may have with GreenTeam Internet in Israel.
Intego VirusBarrier X9 Users Are Protected
Intego VirusBarrier with up-to-date virus definitions will detect this malware as OSX/MaMi.A.
We recommend Mac Premium Bundle X9, which includes VirusBarrier, for the most comprehensive commercial anti-malware protection and utility suite available for Mac.
Subscribe for More Mac Security News
We’ll talk about OSX/MaMi on this week’s edition of the Intego Mac Podcast; subscribe in iTunes/Podcasts to make sure you get the latest episode on Wednesday.
Be sure to subscribe to The Mac Security Blog, the Intego Mac Podcast, and Intego’s YouTube channel to make sure you don’t miss any important news!
Man in the middle diagram image credit: Nasanbuyn and Apple; modified by Joshua Long.