Apple Updates XProtect to Block New Leverage Malware Variant
Posted on
by
Derek Erwin
Following the discovery of a new version of OSX/Leverage, a backdoor first spotted in 2013, Apple has issued an update to its XProtect malware definitions to version 2093. This update provides basic detection for this new threat, which the Apple security team named OSX.Leverage.A. Intego VirusBarrier already provides protection against this threat, which it identifies as OSX/FlashyComposer.A.
The malware is a newer version of OSX/Leverage.A, which Intego analyzed back in 2013. While the core sources of the two Leverage samples are the same, there are some notable differences in the new threat.
The first Leverage variant was a Trojan application that masqueraded as a picture (the .app file extension was not visible by default), and once installed, our testing revealed that the Trojan would attempt to download a logo of the Syrian Electronic Army hacker group onto the infected machine.

The new iteration disguises itself as a fake Flash Player update, which Intego warned could happen in our 2013 blog post. Additionally, the new version of the Leverage malware is signed with an Apple code signing certificate issued to a developer, named “Aleks Papandopulo,” as noted by Security Week’s Eduard Kovacs.
A potential victim will land on a webpage designed to appear as though it is a legitimate Adobe website, which loads an iframe from a URL with malicious code. (RELATED: How to Tell if Adobe Flash Player Update is Valid)
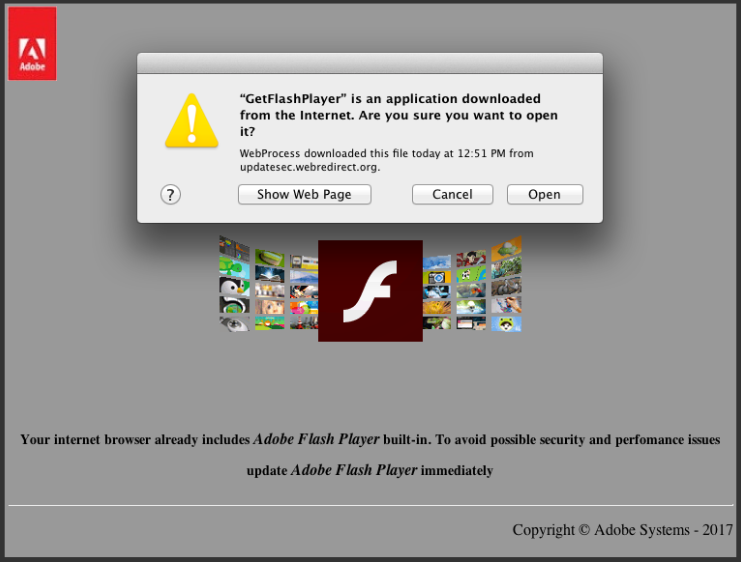
The malicious code attempts to download and install a fake Flash update. Image credit: Volexity.
If a victim allows the execution of the malicious file when prompted or manually executes it from the Downloads folder, the Leverage malware installs a backdoor that beacons back to its command and control (C&C) server once per second until a connection is established, and sends information about the infected Mac. Veloxity researchers eloquently clarified, “Unlike the earlier version of the malware, this new version does not limit itself to a predefined set of commands and instead allows an unrestricted command shell capability back into an infected system.”
Intego VirusBarrier with up-to-date virus definitions will detect and eradicate the Leverage malware, the original variant identified as OSX/Leverage.A, and due to the way the new Mac Trojan disguises itself as a fake Flash Player update, the new variant will be flagged by our anti-virus software as OSX/FlashyComposer.A.