Two New Variants of Backdoor Trojan Found Targeting Activists
Posted on
by
Lysa Myers
Two new variants of a backdoor trojan named OSX/FileSteal have been found to be targeting activists via targeted email. The trojan is signed using a developer certificate to bypass certain levels of Gatekeeper protection. At the time of writing, the certificate has been revoked and the servers used by the threat have been sinkholed and as such the threat has been effectively neutralized. As new variants could continue to be created, it is best to continue to exercise caution, particularly if you’re in a targeted group.
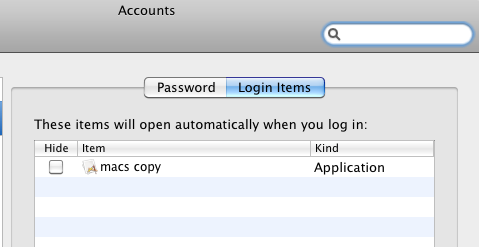
The backdoor itself is, like previous variants, very basic in functionality. It copies itself to the User’s home folder (whereas the original variant copied itself to the /Applications folder) and adds itself to the user’s login item to be launched on every startup. It does this using the same Applescript as used by the original OSX/FileSteal.A variant. The backdoor silently takes screenshots of the affected user’s machine, which are put it in the ~/MacApp folder. The threat then sends collected screenshots in PNG format to one remote website, and it sends other collected user info to another, separate site. The various sites used by the backdoor are not responding at this time.
In the case of at least one variant, the application is purported to be a picture within a ZIP archive:
- DSC001254_160413.zip
When unzipped, the application name is the same:
- DSC001254_160413.app
The remote sites used by the different variants of this threat are as follows:
- torqspot.org/App/MacADV/up.php
- securitytable.org/app-ang/upload.php
- securitytable.org/lang.php
- docsforum.info/lang.php
Intego VirusBarrier users with up-to-date virus definitions will detect this trojan as OSX/FileSteal.B.