The chain of trust in Apple’s devices
Posted on
by
Kirk McElhearn
 A lot of computer security is based on trust. Your devices verify that you are, indeed, an authorized user, through the use of user names and passwords. And your devices trust services and servers, through a series of certificates and “trusted third parties” who work through a cascading system of verification and authentication.
A lot of computer security is based on trust. Your devices verify that you are, indeed, an authorized user, through the use of user names and passwords. And your devices trust services and servers, through a series of certificates and “trusted third parties” who work through a cascading system of verification and authentication.
If you use Apple devices, the company has its own chain of trust that allows you to use multiple devices in concert. Each link of this chain is carefully designed to ensure its reliability, and each link also enhances other links in the chain. This can seem complex, but when you break it down into its component parts, it’s a lot easier to understand.
In most cases, you don’t need to know how all these elements work together, but it can be good to be aware of how Apple ensures the security of your devices, your accounts, and even your payment methods.
Your Apple ID
It all begins with your Apple ID. When you create a new Apple ID on Apple’s website, or on a device you own, you provide your name, birthday, and email address, set up a password, then answer three security questions. You verify your email address, and your Apple ID allows you to use Apple’s services.
This email address and password are now the keys that let you work with your iCloud account, which is automatically created with a new Apple ID, and any of Apple’s services, such as the iTunes Store, Apple Pay, and others.
But to go further, and use more advanced features, you need to turn on two-factor authentication. This allows you to activate the chain of trust across Apple devices that gives you much more power and lets you access enhanced features. When you set up two-factor authentication, you nominate one or more devices as “trusted devices” that provide codes when you want to log into Apple services. Adding a trusted device—a Mac, iPhone, iPad, iPod touch, or Apple Watch—allows Apple to send codes to these devices.
Since you’ve asserted your identity with your email and password, and confirmed it by entering a code received on a trusted device in your possession, the new device or service can be confident of your identity, and extend the chain of trust. Since email addresses and passwords are sometimes stolen, having that additional factor to confirm your identity is a powerful plus for security.
Once you’ve signed in with your Apple ID on a new device, you can use that new device to receive Apple ID verification codes. Since you have been authenticated on the new device, it has become a trusted device to receive these codes. On a Mac or on iOS, go to System Preferences or Settings, then Apple ID > Password & Security, and click Get Verification Code to obtain a code you can use to sign into your Apple ID on another device.
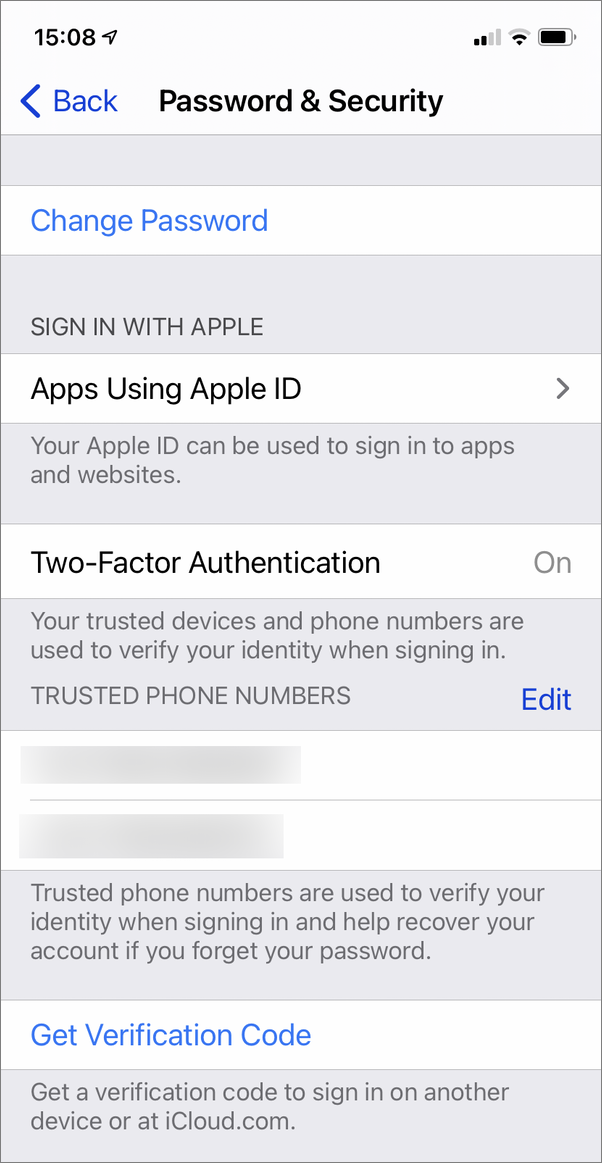
These one-time authentication codes can be delivered in other ways. You can add trusted phone numbers to your Apple ID account, to which codes can be sent via SMS text message. This can be helpful if you don’t always have a second device handy, or if you want to add numbers for your spouse or partner, children, or close friends, to ensure you can get codes when you need them. On the other hand, SMS is not the most secure way to validate one’s identity; targeted attack methods can be used to receive a victim’s SMS messages or phone calls.
Apple’s identify verification technologies are not just for working with Apple services, either. For example, many banks and merchants deem Touch ID and Face ID robust enough to trust them for authenticating you so you can use their apps. Furthermore, you can pay with your iPhone or Apple Watch on NFC terminals that accept Apple Pay.
The Web of Apple Devices
If you have multiple Apple devices, and you are logged into your Apple ID on all of them, the web of trust they create allows you to leverage different devices to perform secure actions. For example, you can use your Apple Watch to unlock your Mac when it’s asleep and to authenticate for certain password requests. What’s interesting here is the connection between the Apple Watch, your iPhone, and your Mac.
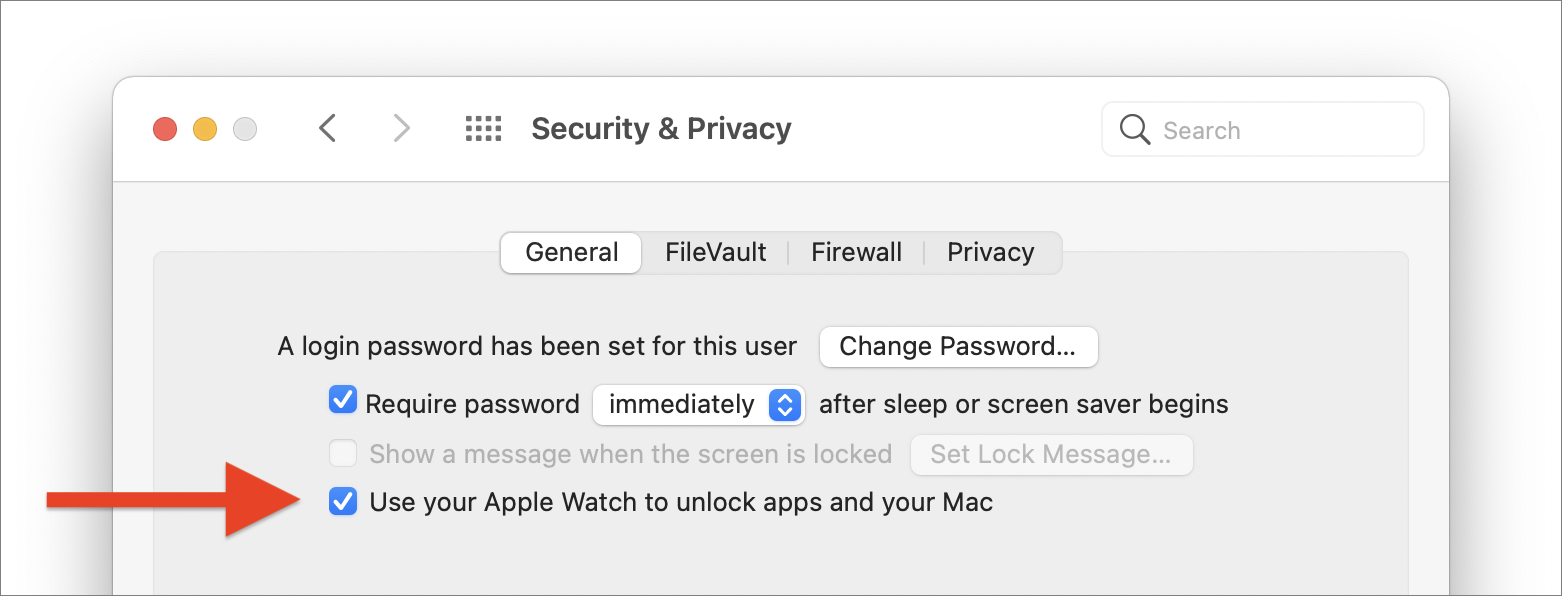
When you tell your Mac to allow your Apple Watch to unlock it, this three-step connection, with all the devices signed into the same Apple ID, is activated. You authenticate on your iPhone when you start it up by entering a passcode; you authenticate on your Apple Watch with a passcode as well. (After each device has been started up, you can unlock the phone with Face ID, Touch ID, or a passcode, and you can unlock the Apple Watch by unlocking your phone, or by tapping its passcode.) And this allows the watch to communicate directly with the Mac to perform these secure operations.
This feature is part of Apple’s Continuity technology, which also allows you to instantly share information across devices. For example, the Universal Clipboard allows you to copy data on one device, and have it available on another device. This data is encrypted, so the transmission is fully secure.
Even More on Macs
Some recent Apple laptops use Apple’s T2 security chips, and offer extended security features, ranging from the ability to use Touch ID instead of passwords to enhanced full-disk encryption. And this links with your Apple ID, if you have two-factor authentication enabled, allowing you to make purchases from the iTunes Store, the Mac App Store, and other Apple services.
The chain of trust also extends to Macs without Touch ID. If you have an iPhone or Apple Watch, you can use Apple Pay on a Mac (whether or not it has Touch ID), because each device in the chain has been trusted. The Bluetooth connection between the Mac and the other device is enough to ensure the integrity of the chain.
Beyond Apple
Unlike most implementations of two-factor authentication, Apple’s approach relies heavily on its multiple-device ecosystem. As you have seen above, once one device is authorized to use your account, it can authorize other devices. This gives you a great deal of power, because data can be shared across authorized devices, and because Apple is aware of all your devices. If a device is lost or stolen, or if you sell it or give it away, can easily sign out of it on the Apple ID website, or from one of your devices, removing it from the chain of trust. You can also remove Apple Pay from a device at any time, or lock or erase a device using the Find My app on one of your other devices.
This can all seem a bit complicated, but the Apple ID ecosystem and Apple’s tightly integrated hardware and software enable unique authentication technologies that leverage multiple devices to enhance your security.
How can I learn more?
 We further discuss Apple’s chain of trust on the Intego Mac Podcast, episode 111. Be sure to subscribe to make sure you never miss the latest episode!
We further discuss Apple’s chain of trust on the Intego Mac Podcast, episode 111. Be sure to subscribe to make sure you never miss the latest episode!
Also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
And make sure you’re following Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the ? to get notified about new videos).