Phishing Dangers in Business and How to Avoid Getting Hooked
Posted on
by
Kirk McElhearn
Gone are the days when malware simply rendered a computer useless or deleted files. Instead of creating malware to show off, hackers are now in it for the money. Because of this, most malware these days are designed to collect personal information, such as user names and passwords. Cyber-criminals leverage this information to hack accounts, such as email, Twitter and Facebook accounts, to spam your friends.
But the real jackpot is when hackers can trick you into giving up your banking information or credit card numbers. When that happens, they can drain your money, at least until you block the accounts.
The main way online thieves get these credentials is through “phishing,” or sending out emails that look exactly like official emails from your bank, credit card company, PayPal, Amazon or other online companies or services.
Falling for these scams can be detrimental to individuals, but they are even more harmful to businesses. If one of your employees gets fooled by phishing and inadvertently gives up the credentials for your company’s accounts, the results could be disastrous. Here’s how to detect phishing emails and make sure that you don’t get hooked.
If It Looks Real, It Must Be Real?
You probably have already seen phishing emails. Phishing emails can look very real, and sometimes these bogus emails are so well crafted they can fool busy professionals who juggle hundreds of emails a day. The reality is that it’s not hard to make these emails look authentic. They’re sent as HTML—just like web pages—and anyone can copy the code that a real company uses in emails and tweak it for their own nefarious plans.
Here’s one example:
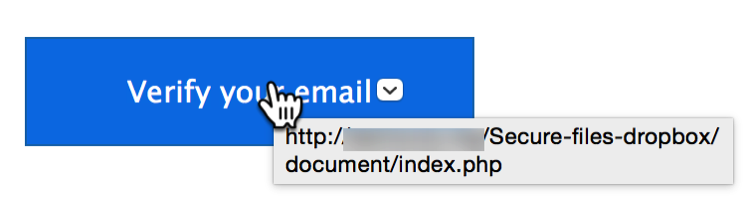
This looks like the standard email that you may get often from colleagues or clients, telling you that someone has shared files with you on Dropbox. If you click the link to “Verify your email,” you’ll get taken to a web page that looks authentic. If you log in, you have just given your credentials to hackers, and your company’s Dropbox can be pilfered.
For a business, this could be fatal. You may store marketing documents for new products, financial documents and more, which could benefit your competitors. Often, the cyber-criminals will simply change the Dropbox password and hold to ransom until you make a juicy payment; yet, even then, they may not change it back.
You need to make sure that any such email is authentic. There’s an easy way to do this: hover your cursor over the link in the email and you’ll see a popup showing the URL, as you can see below. I’ve blurred the domain in the link, so as not to show a compromised server, but it’s not dropbox.com.
Look closely when you check these links in potential phishing emails. Sometimes you’ll see a server such as dropbox.something.com; this is glaring red flag, because that’s not Dropbox. Any company that sends real emails like this will use their domain, such as apple.com, amazon.com, or similar; companies will never use a subdomain.
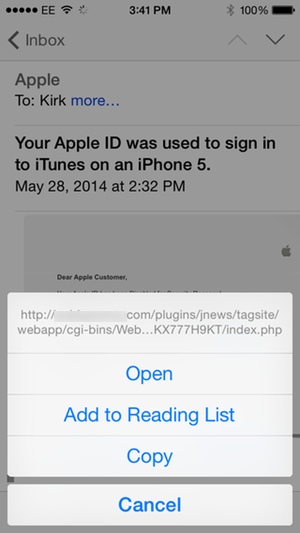
If you get this kind of email on an iPhone or iPad, you can still view the link. Just tap and hold the link in an email until a sheet displays. Here’s an example with a different phishing email, one purporting to be from Apple:
When you look at links in phishing emails, you’ll see that they generally go to small servers. Hackers exploit the poor security on such servers, and hide their files deep in their hierarchy. If you look at the link just above, you can see that it’s abbreviated because it’s so long, but also that the index.php file, which you would load if you tapped the link, is hidden many levels down on the server.
Best Practices to Avoid Phishing Scams
So, when you get any email asking you to log into any website, think before you click or tap. Your bank will never send you an email with such a link; they’ll direct you to log in the normal way on their server. Some sites, such as Amazon, PayPal or eBay, will contain links to their site, but you can check the links as explained above. They should always be paypal.com/something, and not paypal.com.something. When in doubt, don’t click; log in on the website in the usual way.
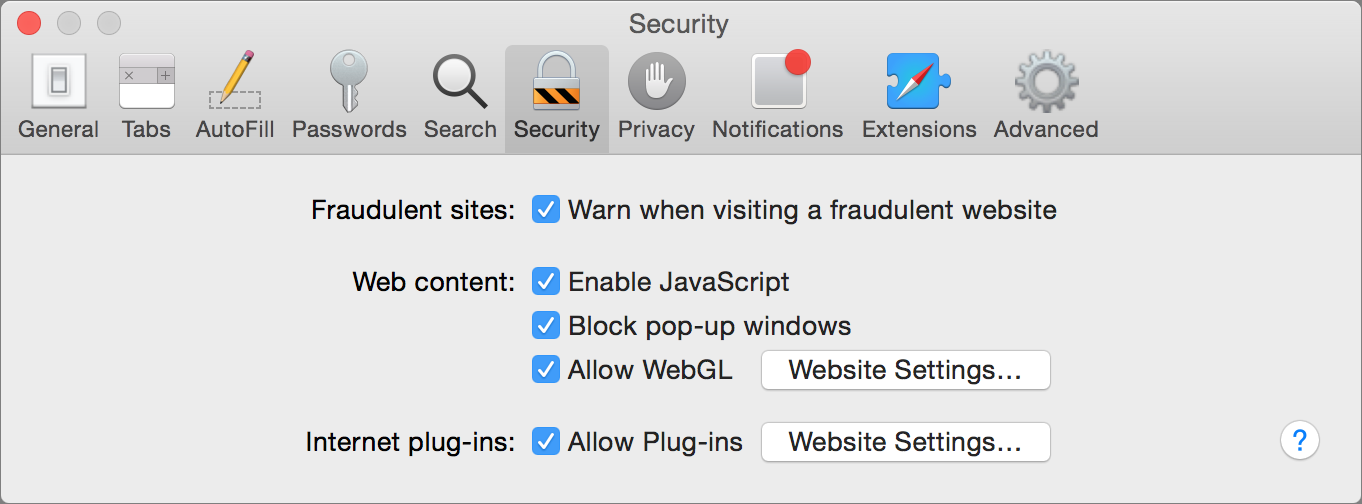
Another way to stay safe is to turn on fraudulent site warnings in your web browser. These generally use a Google database of known fraudulent websites, and phishing sites are often flagged very quickly by the security community.
- In Safari, go to Preferences > Security, and check Warn when visiting a fraudulent website.
- In Chrome, go to Preferences > Settings, then click Show Advanced Settings. In the Privacy section, check Enable phishing and malware protection.
- In Firefox, go to Preferences > Security, and check Block reported web forgeries.
Phishing is a scourge, but it’s avoidable. If you know what to look for, and if you’re careful what you click, you can protect yourself. Take some time to teach all your employees how to deal with phishing emails and your company will be protected.
Shoring Up Your Business’ Defenses
Do you manage the security of your company? We encourage you to download our security white paper, where we analyze the biggest threats facing small businesses and provide expert tips for shoring up your defenses.
Download our white paper today!
Cyber-security is essential for businesses of all sizes, whether you’re a Fortune 500 company or a small business. With more business activities taking place on computers, over networks and in the cloud, businesses can no longer ignore the threats they face.