New Targeted Attack on Tibetan Activists Using OS X Discovered
Posted on
by
Lysa Myers
Once again, another round of targeted attack on Tibetan activists which drops a backdoor trojan has been found (the last attack on Tibetan activists was OSX/Dockster.A). There’s a possibility this one was created by the same group that was using the Tibet trojans. At this time, the threat is considered low risk. The trojan comes as a DOC file, which uses a fairly old Microsoft Word exploit to attempt to drop its payload. This was picked up with older VirusBarrier virus definition updates as W97/CVE-2009-0563.gen. The backdoor is a very simple one – it only gives the attacker the capability to run commands on the local machine and is steals a copy of the affected user’s contact information.
The backdoor can come with different file names, but one example is “2013-02-04 – Deported Uyghurs.doc” (file size 151612 bytes). If it’s successfully run, it attempts to connect to a command and control center at update.googmail.org, which is still operational at time of writing. It will then send the user’s contact information, to identify the affected user.
It creates the following files:
In the Home User’s folder:
- ~/Library/LaunchAgents/apple.plist
- ~/Library/LaunchAgents/.systm (hidden file)
In order to maintain root permission access for the backdoor after reboot, it copies these files to the LaunchDaemons folder with the sudo command:
- /Library/LaunchDaemons/apple.plist
- /Library/LaunchDaemons/.systm
It creates the following temporary files:
- /tmp/tmpAddressbook.vcf (the user’s contact information)
- /tmp/__system (the backdoor)
If this trojan is run on Mountain Lion, it will prompt the user that the backdoor is trying to access a user’s contacts.
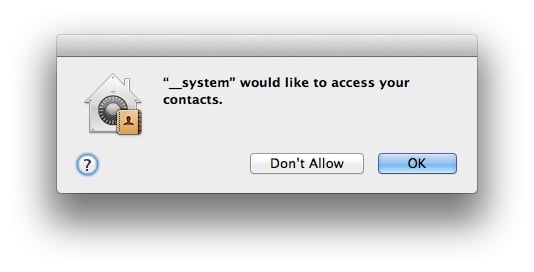
It’s clear from the construction of the file that this threat is targeted at users who are using OS X 10.4 or older. OS X Tiger was released in 2005 and now has less than a quarter of a percent of the total desktop market share and less than 2% of OS X market share.
Microsoft patched the vulnerability used by this trojan on June 09, 2009. If a user has updated their software since then, the backdoor will not drop. And likewise, if a user has updated their virus definition updates since that time, VirusBarrier will detect the compromised DOC file as W97/CVE-2009-0563.gen. Intego VirusBarrier users with up-to-date virus definitions will detect the backdoor as OSX/CallMe.A.