Month in Review: Apple Security in August 2017
Posted on
by
Joshua Long

In the wake of the Black Hat and DEF CON events in July, one might expect that August 2017 might be completely devoid of any interesting Apple security news, but not so!
We’ve got the scoop on the latest in Mac and iOS security, including the exposition of Touch ID’s Secure Enclave firmware, a Counter-Strike “pony” that hijacks your Mac… and what the heck is Mughthesec? Read on for more details.
Touch ID Secure Enclave Processor Firmware Allegedly Decrypted
On Apple devices with a built-in fingerprint reader, the “Secure Enclave” handles Touch ID transactions.
In mid-August, a hacker claimed to have decrypted and then published online the firmware for Apple’s Secure Enclave Processor (SEP), along with the decryption key and tools for working with them.

Apple takes pride in the security of Touch ID and the Secure Enclave. Image credit: Kārlis Dambrāns
So what does this mean? In theory, this could make it a lot easier for attackers to find weaknesses or vulnerabilities in the Secure Enclave. The hacker argues that since anyone can now analyze the firmware, the long-term effect should be that Apple’s Secure Enclave will only become stronger as Apple is forced to improve upon it.
 But in the mean time, does this mean that users’ fingerprints and passwords can be obtained? Evidently the answer is no, at least for now.
But in the mean time, does this mean that users’ fingerprints and passwords can be obtained? Evidently the answer is no, at least for now.
Speaking to TechRepublic, an Apple spokesperson said, “There are a lot of layers of security involved in the SEP, and access to firmware in no way provides access to data protection class information.”
Expect to hear more about the Secure Enclave over the next several months as hackers take a closer look at Apple’s SEP firmware.
New Mac Malware: OSX/Pwnet.A
Last week, SentinelOne reported on a supposed hack for the Mac version of the game Counter-Strike: Global Offensive that turned out to be a Trojan horse (or… pony).
The malware (OSX/Pwnet.A, pronounced with a vaguely French pronunciation so as to sound like “pony”) attempts to hijack the victim’s system for the purpose of mining cryptocurrencies.

Pony Strike: Download a Counter-Strike hack, get pwned. Image credit: FilipinoNinja95
As a rule of thumb, avoid downloading cracks, hacks, and other questionable software. It’s not worth potentially infecting your computer and putting your security and privacy at risk.
Apple Updates XProtect; Blocks “Mughthesec,” Other Adware
XProtect is a nickname for Apple’s bad-download blocker; a very rudimentary, incomplete, and infrequently updated form of malware protection that’s built into macOS.
Last week, Apple updated its XProtect signatures for the first time in a month, adding signatures for OSX.AceInstaller.B, OSX.AdLoad.A, OSX.AdLoad.B, OSX.Bundlore.B, OSX.Genieo.G.1, and OSX.Mughthesec.A. It’s interesting to note that these signatures all relate to harmful or undesirable adware.
Perhaps the most interesting addition is OSX/Mughthesec.A.
According to Patrick Wardle’s detailed analysis in early August, zero of the 58 anti-virus products on VirusTotal detected the sample that he obtained. Moreover, the disk image and the installer contained therein even had a valid Apple Developer ID signature.
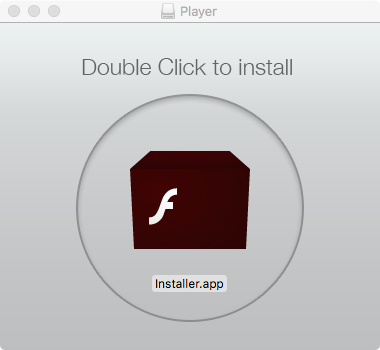
Mughthesec masquerades as a Flash Player installer. Image credit: Patrick Wardle
Mughthesec disguises itself as a Flash Player installer, but it’s definitely not an authorized installer from Adobe. It bundles adware and other potentially unwanted programs, such as a Safari search hijacker and a “cleaner” program that pops up scary alerts.
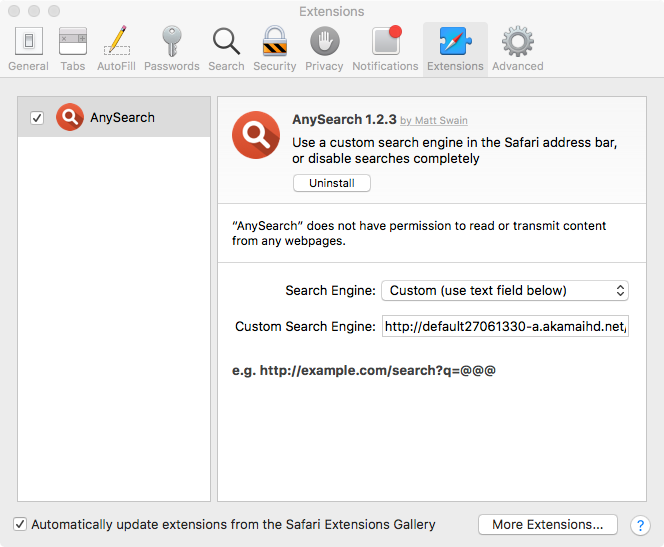
Mughthesec installs a creepy custom search engine in Safari. Image credit: Patrick Wardle
These days, with Adobe phasing out Flash, and with a version of the player being built into Google Chrome, most users can probably avoid installing the antiquated plugin altogether.
If for some reason you really do need the Flash Player plugin for Safari or Firefox, be sure to obtain it by going to Adobe’s official site via a bookmark; never accept any Web site’s unsolicited invitation to install it.
RELATED: How to Tell if Adobe Flash Player Update is Valid
Reports of iOS Fake Virus Warnings
Anecdotal evidence suggests that there may have been a recent increase in fake virus alert messages when browsing sites on iOS devices (iPhone, iPad, or iPod touch).
An NBC affiliate news station based in St. Louis, Missouri reported earlier this month on these fraudulent mobile alerts. The news segment suggested that iOS users can avoid seeing some of these fake virus alerts by turning off pop-ups for the mobile version of Safari via the Settings app.
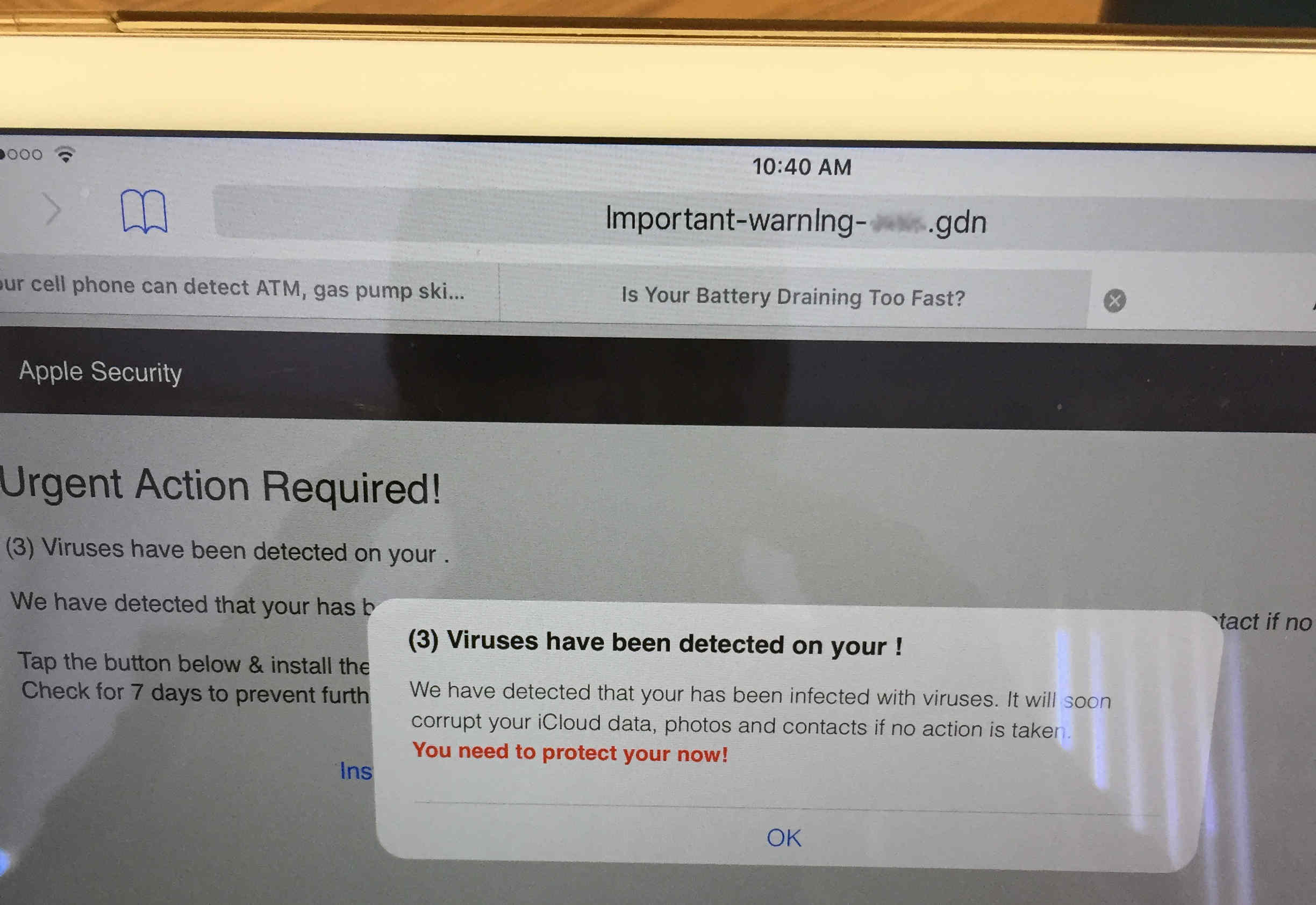
Don’t be alarmed by “virus” warnings on your iPhone or iPad. Image credit: anonymous reader
If you do see fake alerts such as these, whether on your mobile device, laptop, or desktop, be careful to avoid tapping or clicking on anything on the page; it’s best to find the actual close button (watch out for fake ones) to close the browser tab or window.
 If you use either a Mac or an iPad with a physical keyboard, the safest way to close the current browser tab or window is to use the Command+W keystroke (hold Command and press W).
If you use either a Mac or an iPad with a physical keyboard, the safest way to close the current browser tab or window is to use the Command+W keystroke (hold Command and press W).
Don’t be too concerned about virus alerts on iOS; there are currently no actual viruses in the wild for iPhones and iPads. (Do exercise caution, though, because iOS is not invincible, and be sure to always update to the latest version of iOS.)
You can keep your Macs protected from viruses and other forms of malware by installing a trusted protection suite from a reputable company, such as Intego VirusBarrier.
Multi-platform Adware Campaign Spreading via Facebook Messenger
August is apparently adware month! Securelist reports of an ongoing investigation into a campaign spreading adware via Facebook Messenger.
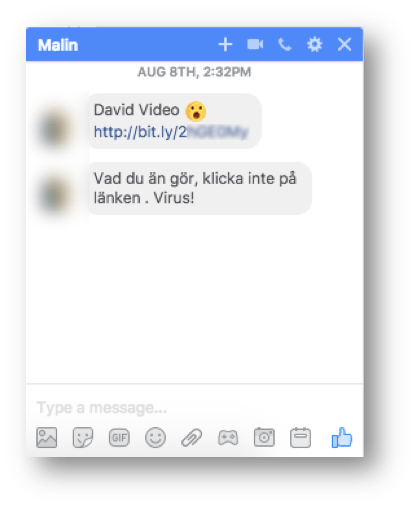
If a random contact sends you a link, avoid clicking on it. Image credit: Securelist
It’s unknown exactly how the campaign leverages Facebook accounts, whether through stolen or leaked account login credentials, browser hijacking, or clickjacking.
If a recipient were to click on the unsolicited link, they may be redirected to a PDF file hosted on Google Docs that, if clicked, begins a chain of rapid redirections that may lead to adware, malware, or advertisements that make money for the initiator of the campaign.
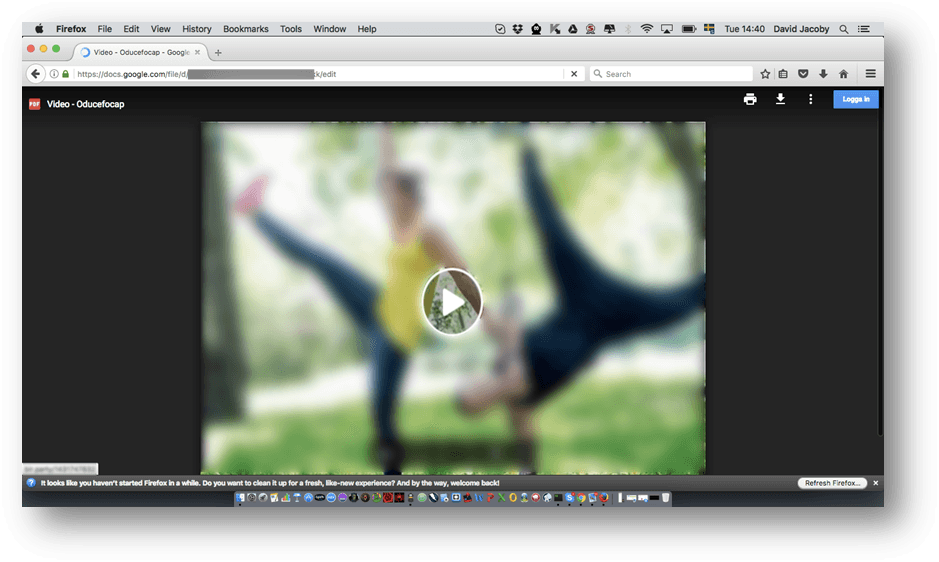
Stop! If you accidentally clicked on a rogue link in a Facebook message, don’t click any further or your computer may end up infected. Image credit: Securelist
The redirections are targeted depending on the platform you’re using, whether Mac or Windows (or potentially iOS or Android). Mac users will likely end up with a fake Flash Player installer or other scam or ad-laden software, similar to the Mughthesec adware installer described earlier.
Stay Tuned! Subscribe to The Mac Security Blog
Be sure to subscribe to The Mac Security Blog to stay informed about Apple security throughout each month.
If you missed Intego’s previous Apple security news roundups for 2017, you can check them out here.
Have something to say about this story? Share your comments below!