How to Combat NSA Surveillance (And Keep Fighting for Privacy!)
Posted on
by
Lysa Myers
I was reminded this morning that a recent year was dubbed the “year of privacy,” meaning that it was the year that people began to understand how much surveillance was happening, and how much it could affect their daily lives. Could that year have been 2013?
Turns out, that year was 2012. Holy cow. So, perhaps that makes 2013 the year of DUDE, WHERE’S MY PRIVACY!?!?
A recent Pew Internet study indicated that more than half of their respondents were concerned about their private information getting exposed online, up from 30 percent in 2009. Happily, 55 percent of the respondents have taken steps to elude surveillance, though 59 percent didn’t think it’s possible to be completely anonymous online. And 68 percent felt that current laws weren’t sufficient to protect their online privacy.
Upon reading this, my reaction was hopeful: “They get it.” According to the Pew Internet study, it’s possible that a majority of people finally get that privacy has been dealt a huge blow; they’re realistic about whether they can truly be anonymous online, and that laws are not sufficiently dealing with the problem.
The latest revelation in the ongoing NSA scandal is that their surveillance efforts include subverting encryption. That is to say, rather than necessarily breaking the encryption, they’re doing things to get around encryption, like encouraging the use of weaker standards or putting backdoors in place so that they see the traffic before it gets encrypted. Once again, we turn to xkcd for an illustration of this principle.
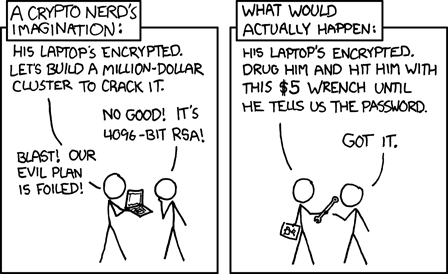
Why spend billions of dollars and CPU cycles breaking encryption, when you can just talk someone out of the keys?
Cryptographer and security specialist Bruce Schneier suggested that rather than worry about the NSA’s surveillance capabilities, we simply make the cost of accumulating information on us more expensive.
The NSA has turned the fabric of the Internet into a vast surveillance platform, but they are not magical. They’re limited by the same economic realities as the rest of us, and our best defense is to make surveillance of us as expensive as possible.
This is much the same tactic that we’ve been suggesting in terms of security. If you make it too costly to get into your machine, attackers will look elsewhere. To help you combat NSA surveillance in this way, Schneier offers several tips.
In short:
- Use Tor’s hidden services to hide your traffic
- Use encryption
- Use an “air gap” when you need to transfer particularly important data
He also gives several tips specific to how to choose the best types of encryption:
- Choose open-source over proprietary algorithms
- Choose symmetric cryptography over public-key cryptography
- Choose conventional discrete-log-based systems over elliptic-curve systems
Granted, that last suggestion may be over most folks’ heads. Do what you can, as you’re simply aiming to make your traffic harder to read than average. Think of it like the analogy of not having to outrun a bear to avoid getting eaten: you don’t have to be fastest, you just have to run faster than the slowest guy.
Keep in mind this isn’t where we should stop our measures to improve privacy. Right now, privacy is not adequately being protected by the law. If we want this to change, we must tell our legislators that this concerns us. In addition to improving the protection of our personal information, we can keep fighting for privacy by contacting our government representatives to let them know that this is an issue of great importance.
