Recommended + Security & Privacy
How Malicious Plugins Can Compromise Your Mac
Posted on
by
Jay Vrijenhoek
I cannot remember a time in which my browsers did not have a few plug-ins installed. My Safari has three and my Firefox has seven; they’re the first thing I install on a new system, and I really dislike browsing the Web without them. Plug-ins (also called extensions or add-ons) are not always useful enhancements though, and may even be installed without your knowledge — some of which may even be malicious and can compromise your Mac.
So what are some things you should look out for when using plugins? And how can you tell if they’re legit or malicious plugins? It’s not always easy to tell, but there are tried and true methods to help you navigate the Web more safely. In this article, we will cover some best practices for the use of plug-ins and how you can stay safe when using them.
Get plug-ins only from a trusted source
If you need to use a plug-in, it’s best to only get it from a trusted source. For example, if you want the Adblock plug-in for Safari, you should get it from the official Adblock website or from the Safari Extensions web page hosted by Apple.
Do not get plug-ins from a web page or a pop-up that prompts you to install it! These potentially harmful prompts are most often seen in the form of fake Flash Player updates. If you do see a pop-up that suggests a plug-in you might actually want to install, close the pop-up window and get that plug-in from a trusted source. (RELATED: How to Tell if Adobe Flash Player Update is Valid)
Note: While blocking ads makes my browsing experience much better overall, I do unblock websites that show a normal amount of ads that are relevant to the site’s content. Ads pay the bills for a lot of websites, so I’m happy to contribute to sites I frequent often.
Plug-ins to avoid
Flash Player, Java, Silverlight and Acrobat are most often exploited and should be avoided if you can. That said, each plug-in that you install increases the potential attack surface, so don’t install a plug-in unless you really need it.
Keeping your plug-ins up to date
Your browser should be doing this for you, but you can verify your browser is set up for auto-updating plug-ins. Here are steps to keep your plug-ins up-to-date in Safari and Firefox:
Safari
Open the Preferences, and then click the Extensions tab. At the bottom of that window, you will see a checkbox that will enable the automatic updating of extensions; make sure it’s checked.
![]()
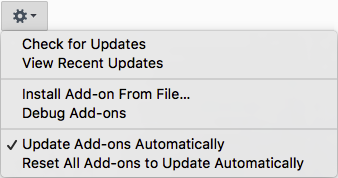
Firefox
From the Tools menu, select Add-ons. Click on the button with a cog wheel in it and make sure “Update Add-ons Automatically” is checked.
How your Mac and browsers protect you
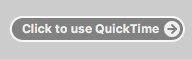
Every major browser has implemented a system where plug-ins are activated only if you tell it to activate. This way you can choose to let one website use a plug-in while every other website cannot access it. A website that requires one of your plug-ins to work will display a message similar to this one:
And when you click that button, the browser will show an additional warning and asks you to confirm.
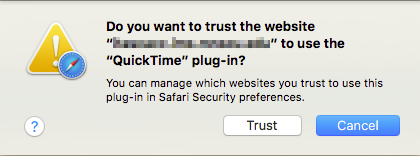
This gives you two chances to really consider the choice you’re making, and unless it’s content you really need from a site you trust, will likely make you think twice before granting the site access to that plug-in.
macOS disables known vulnerable versions of plug-ins for you as well, through its XProtect mechanism. Though it mostly focuses on Flash Player, in the past it has been used to set a minimum required version for Java and Silverlight as well. Unless you have the version Apple recommends or newer, the plug-ins do not work on your system. While a nice additional security measure, it has a very narrow focus when it comes to plug-ins and is not updated to keep up with all threats.
How a plug-in can compromise your Mac
There are two types of plug-ins that can compromise your Mac: vulnerable plug-ins and malicious plug-ins.
Vulnerable plug-ins: These are plug-ins that are not designed with any malicious intent, but they have vulnerabilities that can be exploited by a malicious website or script. In some cases, such as with Flash Player, these vulnerable plug-ins have been riddled with vulnerabilities for so long, they should be labeled as intentionally malicious just for being stubborn and keeping it available; but, that’s just my two cents. Vulnerabilities can happen to any plug-in and, if exploited, can allow a maliciously crafted website or script to gain access to more data than it should. Saved browser passwords or even data on your hard drive are at risk; it depends on the type of plug-in and the vulnerability.
Malicious plug-ins: These plug-ins are specifically designed to put your system or your information at risk. These are the plug-ins that are typically installed by malware or a PUA (Potentially Unwanted Application) and cause advertisements to be injected on webpages that you visit. They can also be installed through malicious websites that prompt you to install “this amazing plug-in” and end up giving you a plug-in that does something completely different. One such example is Awesome Screenshot from some years ago. Genieo is another adware that typically gets installed through application installers that come from dodgy websites. You think you’re downloading VLC Player, MPlayer X or UnRarX, but the installer also puts plug-ins in your browser, so it can start injecting ads on pages you visit. InstallCore is another such adware. Malicious plug-ins are not built to provide the best quality in terms of code and quality control, so they likely introduce several vulnerabilities that can be exploited by other 3rd parties as well.
When it comes to malicious plug-ins, Intego VirusBarrier has you covered. Intego’s anti-virus for Mac blocks the malware/PUA/Plug-in before it gets installed, and if you’ve recently joined the Intego family, it keeps you safe by neutralizing whatever malicious software was already on your system. As for non-malicious but vulnerable plug-ins, use the tips above to either stay away from them completely or at least make sure they stay up-to-date and only activate when you explicitly tell them to.
Happy browsing! 🙂