Apple + Security & Privacy + Security News
Everything you need to know about the FaceTime spying bug
Posted on
by
Joshua Long

UPDATE 2: On Thursday, February 7, Apple fixed the FaceTime vulnerabilities in iOS 12.1.4 and a Supplemental Update for macOS Mojave 10.14.3.
On Monday, January 28, a serious flaw in FaceTime came to light that could allow a FaceTime caller to spy on a call recipient, even if the recipient ignored or declined the call. Apple has taken temporary measures to mitigate the flaw and has promised a complete fix “later this week.” UPDATE 1: Apple issued a statement on Friday morning, formally apologizing for the FaceTime security bug and announcing that the promised client-side software update has been delayed until next week.
The flaw affects all devices running iOS 12.1 or later, and all devices running macOS Mojave 10.14.1 or later—in other words, devices capable of participating in Group FaceTime calls. It is unclear whether Apple Watch or HomePod, which also support Group FaceTime, are affected.
Now you can answer for yourself on FaceTime even if they don’t answer?#Apple explain this.. pic.twitter.com/gr8llRKZxJ
— Benji Mobb™ (@BmManski) January 28, 2019
As seen in various videos demonstrating the flaw, an attacker using an iPhone could initiate a FaceTime call with a victim, and while the call was still ringing, the attacker could swipe up, tap “Add Person” and select themself as a recipient, and FaceTime would immediately begin streaming audio from the victim’s device. No user interaction was required on the victim’s side.
But this attack isn’t limited to just audio; it was also possible to spy on the victim’s camera.
FaceTime video camera spying in action. Credit: MacRumors
If a victim attempted to decline the FaceTime call by pressing their iPhone’s power button, the victim’s device would instead immediately begin streaming video from their front-facing camera to the attacker. On the victim’s device, it would still appear as though the call was waiting to be answered, with no visual indicator that video was being streamed from their device. (Unlike Macs, iPhone and iPad notably lack an indicator light that shows when the camera is in use.)
On Monday evening, Apple took its Group FaceTime feature offline as a temporary mitigation for the problem. Meanwhile, the company promised to eliminate the spying bugs via a software update that will be released “later this week.”
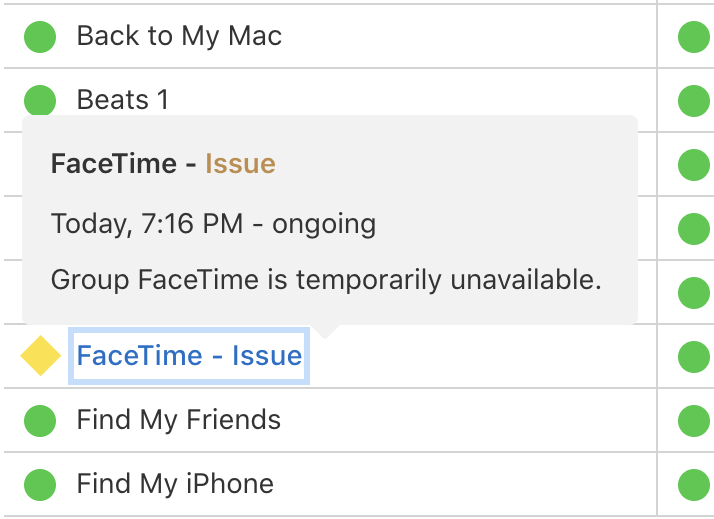
Apple’s temporary fix is to disable Group FaceTime worldwide.
The issue hasn’t gone unnoticed outside of geek and social media circles.
New York governor Andrew Cuomo issued a “consumer alert” about the issue, saying he was “deeply concerned by this irresponsible bug that can be exploited for unscrupulous purposes,” and he urged Apple “to release the fix without delay.”
MORE: NY Gov. Cuomo issues “consumer alert” on Apple FaceTime bug, calling for users to “temporarily disable the app until Apple issues a fix.” https://t.co/j1YZcXAO8E pic.twitter.com/UxCaYqpsGw
— ABC News (@ABC) January 29, 2019
Although some media reports, as well as Governor Cuomo’s alert, have called on users to disable FaceTime until a fix is made available, this should no longer be necessary now that Apple has taken the Group FaceTime service offline server-side until a software update can be made available for affected devices.
How can I learn more?
 We discuss the FaceTime flaw on this week’s edition of the Intego Mac Podcast, so be sure to subscribe to make sure you don’t miss any episodes.
We discuss the FaceTime flaw on this week’s edition of the Intego Mac Podcast, so be sure to subscribe to make sure you don’t miss any episodes.
Also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for updates.
And make sure you’re following Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).