Apple Fails to Properly Fix Gatekeeper Security Hole, Claims Researcher
Posted on
by
Graham Cluley

Anyone who remembers those “I’m a PC, I’m a Mac” ads from some years back will surely remember that a key message that Apple wants to get across to potential customers was this: PCs have a malware problem, Macs don’t.
Of course, that message was partly spin — there had been malware for Apple computers, even before it had existed for PCs.
And, in recent years, although the vast majority of malicious code is written for Windows and Android rather than OS X, there have been outbreaks and most Mac owners realise today the importance of protecting their precious computers from attack.
Apple, naturally, wants to reduce the chances of malware becoming a widespread problem on OS X — and one of the ways it has tried to deal with that is by incorporating Gatekeeper into the operating system, a means to stop unverified, unsigned apps from making their way onto your iMacs and MacBooks.
But, as we reported last October, serious security holes have been found in Gatekeeper that could allow malware to completely bypass Gatekeeper’s checks.
Patrick Wardle, the researcher who uncovered that vulnerability (known as CVE-2015-7024), claims that despite twice attempting to permanently fix the security flaw, Apple’s solution continues to contain cracks that could allow a malicious hacker to wreak havoc on Apple computers.
The slides in Wardle’s presentation make clear that he doesn’t have the highest opinion of OS X’s built-in security.
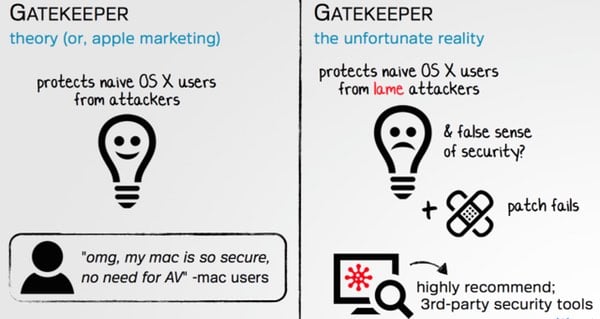
Generally, in my opinion, Gatekeeper does a reasonable job.
If an app is developed by an unknown developer, or has been tampered with en route to your computer via a man-in-the-middle attack over an unencrypted HTTP connection, then Gatekeeper is supposed to spot it and block it.
But, as Wardle showed last year at the Virus Bulletin conference in Prague, there exists a way to waltz past Gatekeeper even if you had configured your Mac to use the maximum “App Store-only” security setting.
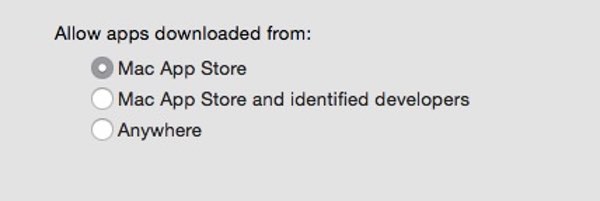
The trick Wardle used was to use a legitimate app that already successful passes Apple’s Gatekeeper check, but that loads or runs code from the same folder, and bundling both into a disk image.
As the legitimate app has already been digitally-signed, Gatekeeper failed to check other content in the disk image that may have a malicious impact.
Clearly this was a problem that had to be fixed — and Apple issued patches to address the issue last October, and again last week.
The problem appears to be that Apple’s fixes have been targeted specifically at the proof-of-concept exploits that Wardle has shared with the engineers in Cupertino, blacklisting particular binaries rather than creating a more comprehensive solution to the issue.
As a result, Wardle claims he has been able to bypass Gatekeeper’s protection — even with the patches in place — within minutes.
The researcher says he will present his full findings at the Shmoocon security conference in Washington DC today, and will release a tool to help plug the gaps that Apple has continued to leave open.
Let’s hope that Apple can learn something from Wardle’s research, and build their own comprehensive fix, that will benefit all of us who rely on computers running Mac OS X.
photo credit: flickr photo shared by micadew under a Creative Commons ( BY-SA ) license