Recommended + Security & Privacy
8 Things to Do Right Now if You’ve Been Hacked
Posted on
by
Kirk McElhearn

You wake up in the morning and you read the news: Another major website or cloud service has been hacked. You yawn, make a cup of coffee, and then all of a sudden realize that you have an account there. Your email, photos, and personal data are now at risk. What do you do?
Unfortunately, data breaches are a common occurrence. From the revelation that 500 million Yahoo user accounts were hacked, to the illegal distribution of Jennifer Lawrence’s photos that had been stolen from her iCloud account, this sort of event is no longer a surprise.
In some cases, millions of people’s accounts are compromised at once—and you may be one of the many victims. So what do you do if this happens to you? Here are eight things you should do right away.
1. Change Your Passwords
The first thing you need to do right away is change your password on the service that has been hacked. This may be a single website, or, in the case of Apple’s iCloud or Google, this password may be the key that opens access to all sorts of personal data. Make sure the new password is secure; if your previous one wasn’t, take advantage of this warning to make sure the new one is harder to crack.
If you were the hacking target, then you need to change passwords on all your accounts. Obviously, this doesn’t include random forums and websites where you’ve signed up for newsletters. But you need to reset your passwords for any account where you have entered financial data, or store personal data of any kind.
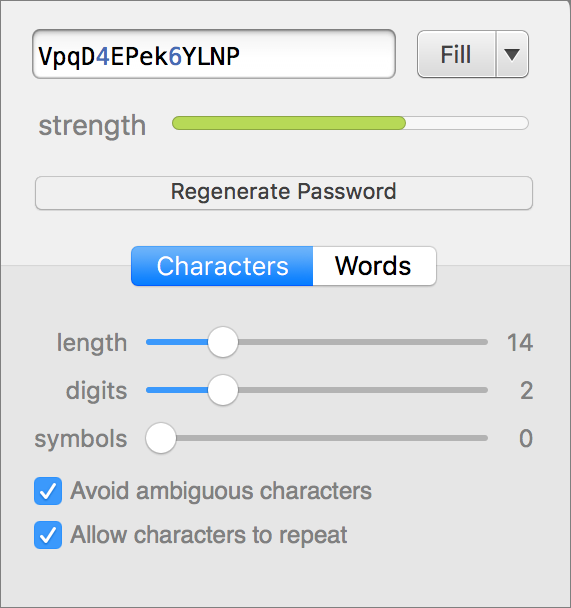
2. Use a Password Manager
The best password is one like this: JovUCB#2yVJ6Rk&A. Or this: icing-3terminal-Sconce. But these are not easy to remember. If you use a password manager, you can create secure passwords for all your needs without having to remember them. The only password you need to recall is a single, very secure password that lets you access your password manager.
There are several password managers for Mac, and my favorite is 1Password (see also our article about how to choose the right password manager for you). Not only does it store your passwords, credit card numbers, bank account information, and more, but it can create passwords for you when you need to set up a new account. I used 1Password to create the two passwords in the paragraph above, using two different options: random characters or words.
Using a password manager helps you use different passwords for different accounts. Since it can be hard to remember all the passwords you need, you may have defaulted to using something like “password123” for lots of accounts. Or you may be using a more secure password, but using it for all your accounts. Get out of that habit: With a password manager, you can create unique secure passwords for each of your accounts.
There are lots of password management apps and solutions out there, and for obvious reasons, it’s important to choose one from a reputable developer. If you mainly use Apple devices, or at least an iPhone, iCloud Keychain is one free password manager that may work for you. Alternatively, you could choose one of several popular password managers that meet high standards of quality and reliability; we’ve reviewed a few of them here.
See also:
4 Best Password Managers in 2024: How to choose the right one for you
3. Turn on Two-Factor Authentication
Many services offer two-factor authentication, which lets you secure your account not only with a user name and password, but also with a device, usually your smartphone. Services such as iCloud, Google, Amazon, Dropbox, Facebook, Twitter, Instagram, and others, offer this feature. You should turn this on for every account where it is available. This article gives you more information about two-factor authentication.
Two-Factor Authentication: How It Works and Why You Should Use It
4. Delete Any Sensitive Data from the Hacked Account
It may already be too late, but just in case, delete any really sensitive data from the account that was hacked. Just because someone has access to your account doesn’t mean they have trawled through all your data or files yet, or they may not have copied everything. So if you’re worried about any important files, especially those that contain personal information, delete them immediately. This is especially the case for services like Dropbox, Google Drive, and iCloud Drive. If you store important files on these cloud services, clear out your folders now.
5. Tell Your Friends
If your account gets hacked, it’s important that you tell your friends and family right away, because a common scam is for people who have access to your email to get in touch with some of your contacts pretending to be you. The scammer may say that you are in some different country and were robbed, and that you need money. Since your friends will think that the emails are really coming from you, they may be inclined to send you money via Western Union, PayPal, or some other service.
Also, a hacker may make malicious posts on Facebook, Twitter, or other social media services in your name. Make sure your friends know that these posts are not from you.
6. De-Authorize Apps on Facebook, Twitter, Google, etc.
Some social media services let you link apps to your account. These apps are able to post for you, as well as read and write information about your account. You may have authorized a number of apps to use Facebook or Twitter, but hackers may plant their own apps thinking that you may not notice, and use them at a later date.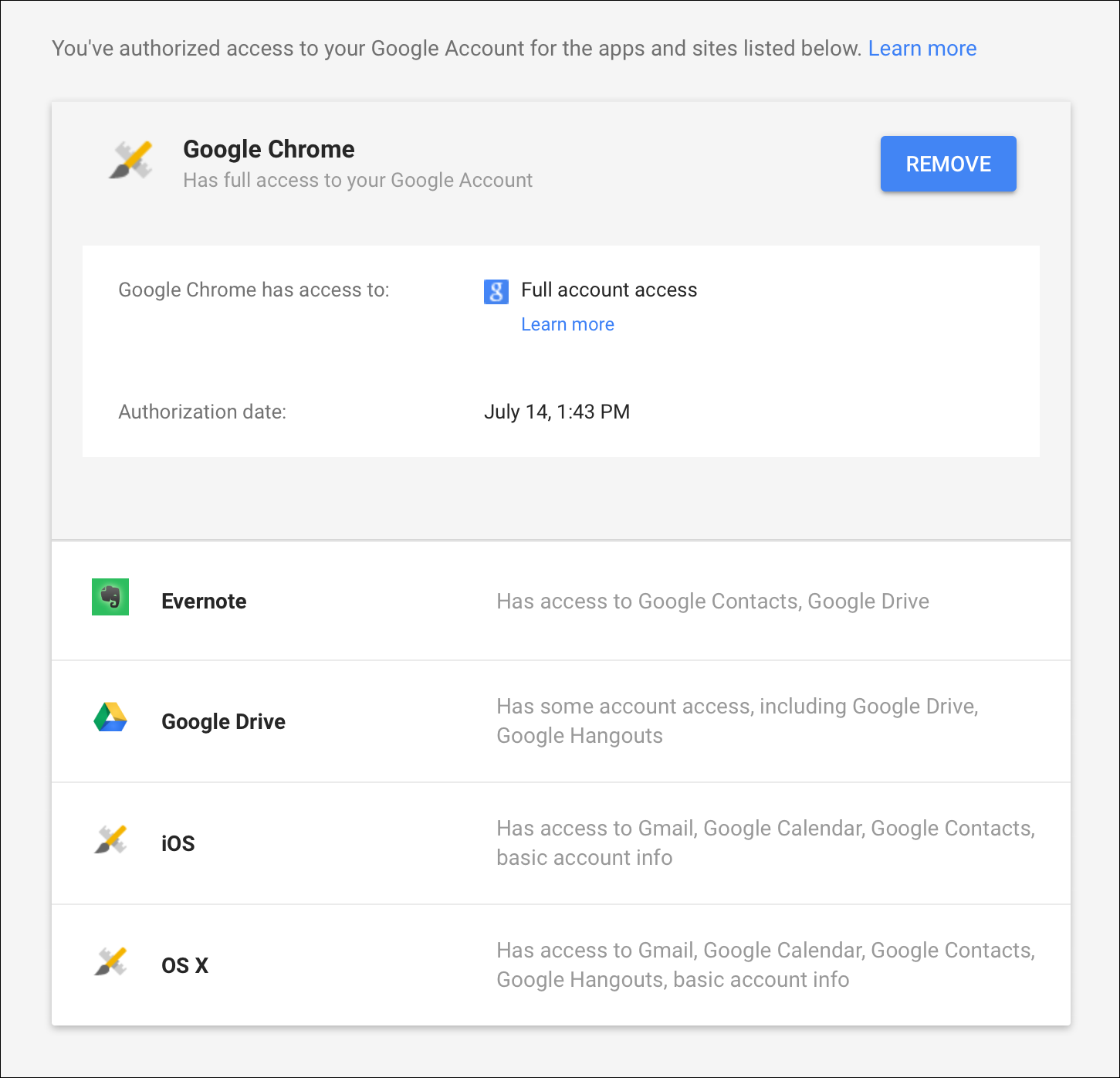
Check the social media platforms you use and, if you don’t recognize any authorized apps, revoke their access. Use these links to check Facebook, Twitter, and Google.
7. Check Your Bank Statements
One of the main reasons why cybercriminals hack Internet accounts is to make money. If someone can get ahold of your credit card information, they will attempt to make purchases until that card is blocked. If they can get into your PayPal account, they will try to transfer money to an account they control.
You should immediately alert your bank, or other financial institution, and if you think your credit card details have been compromised, have your bank cancel the card. But keep your eyes on your bank accounts just in case. Charges don’t always appear immediately, so you may not see anything for a few days.
8. Scan Your Computer
If just your account was hacked—not millions of people on a website or cloud service—then you should be concerned about how this was done. It may have been social engineering: that’s when someone figures out how to pretend they are you and get access to your account. Often this involves people guessing the answers to your security questions.
But it may also have been malware. Your computer may be infected. You should scan your Mac or PC and any external storage devices you have, such as hard drives or USB thumb drives, using trusted antivirus software. For macOS, we recommend VirusBarrier, which is part of Intego’s Mac Premium Bundle, and for Windows, we recommend Intego Antivirus for Windows.
The reason should be fairly obvious: if there is malware on your computer, it may have intercepted keystrokes or copied files, and it may be able to do so again unless proper protections are in place.
There’s a lot to do if you get hacked. But if you haven’t been hacked, you can learn a lot from these eight steps. Use the techniques described above to secure your accounts, making it harder for hackers to get access. Do it now, before you need to do it in a hurry!
How can I learn more?
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()