Silver Sparrow: 40,000 Macs Infected by Mysterious M1-native Malware
Posted on
by
Joshua Long

A new family of Mac malware dubbed Silver Sparrow (detected by Intego and others as OSX/Slisp) has apparently infected at least 40,000 Macs, according to reports. It is also one of the first pieces of Mac malware that runs natively on Apple’s new M1 processors. These facts combined have propelled Silver Sparrow into the mainstream media spotlight.
Let’s explore everything you need to know about the latest Mac malware threat.
In this article:
- How does Silver Sparrow malware spread?
- What potential harm can Silver Sparrow do to Macs?
- Is Silver Sparrow really malware, or a mere proof of concept (PoC)?
- Silver Sparrow is the second M1-native Mac malware discovered
- Silver Sparrow is (at least) the sixth major Apple notarization failure
- Silver Sparrow uses JavaScript during installation
- Silver Sparrow has had wide distribution, but its goal is unknown
- How can one remove or prevent Silver Sparrow and other threats?
- Indicators of compromise (IoCs)
- How can I learn more?
How does Silver Sparrow malware spread?
As of this moment, malware researchers have not yet conclusively identified how Silver Sparrow installation packages have made their way onto Macs.
There are some indications that end-users may have encountered the malware via poisoned Google search results, meaning results leading to legitimate sites that had been compromised by a threat actor, and/or malicious sites that rank highly for particular searches.
Katie Nickels, a representative from Red Canary (the company that discovered the malware), suggested in a live stream on Monday that another possible source of infection may have been malicious browser extensions.
.@likethecoins and @ForensicITGuy are about to chat all things Silver Sparrow. Bring your questions! https://t.co/wSX2i1c41E
— Red Canary (@redcanary) February 22, 2021
What potential harm can Silver Sparrow do to Macs?
At this time, the malware installer packages will no longer run. Apple addressed the two known variants of Silver Sparrow by revoking the developer’s code-signing certificates. Because the malware is no longer signed by an authorized Apple Developer ID, the two known variants of the malware won’t be able to run anymore if someone tries to install them today.
However, it’s worth noting that Apple’s mitigation efforts may not necessarily remove all existing malware infections, and may not block potential future Silver Sparrow variants that would presumably be signed with yet another Apple Developer ID.
Before Apple’s revocation of the code-signing certificates, the malware would install a LaunchAgent as a “persistence” method (i.e. a way for the malware to continue running, even after a victim restarts their Mac).
The LaunchAgent would check an Amazon AWS S3 bucket for further instructions and a potential additional malicious payload, but so far researchers have not yet observed the malware downloading any final payloads. It appears that Amazon may have shut down the S3 buckets that were associated with the two known Silver Sparrow variants.
Theoretically, before revocation of their Apple certificates and cancelation of their S3 buckets, it’s possible that a final payload may have been available for a short period of time, or may have only been made available to certain victims. However, this is only speculation, and this theory unfortunately cannot be confirmed based on the currently available evidence.
Is Silver Sparrow really malware, or a mere proof of concept (PoC)?
There are a couple of indicators that have caused some to speculate that Silver Sparrow might have just been a proof of concept that somehow became widely distributed. Let us examine that speculation.
Proponents of the proof-of-concept theory point out that researchers have not yet observed the malware installing any further malicious payloads. In other words, after the malware gets installed, it has not yet been observed to download and install additional components that can cause further harm or enhance its functionality, as the malware appears designed to do.
Furthermore, the first sample actually installs an app that, if opened, displays a message saying, “Hello, World!”—which is normally a shorthand way for a programmer to say, “This is my first attempt at making this app, and if you’re seeing this message, then the app works!”
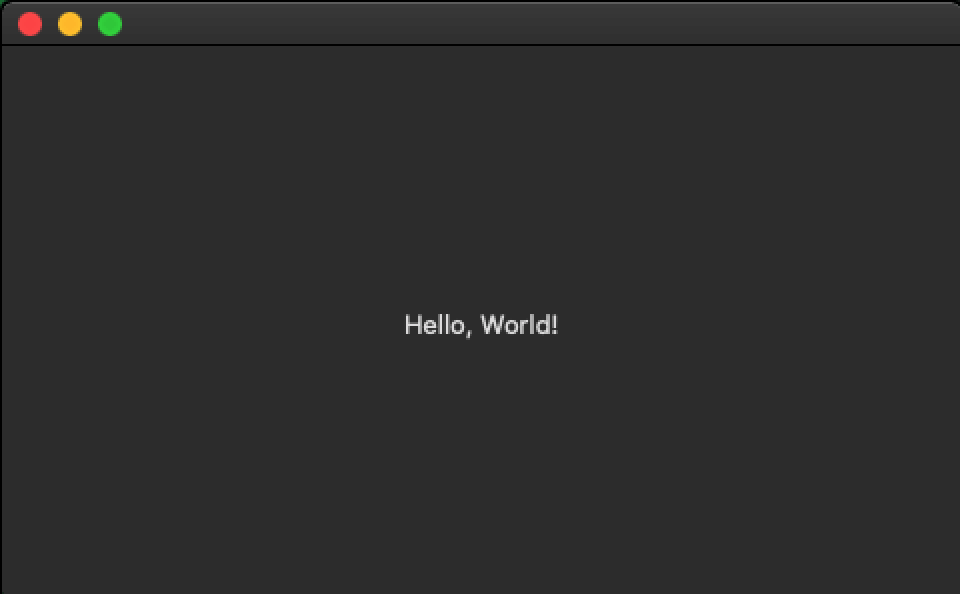
“Hello, World!” message from OSX/Slisp variant 1. Image credit: Erika Noerenberg via Red Canary
However, there are good reasons to think that Silver Sparrow is not merely a proof of concept. For example, there’s the fact that at least tens of thousands of Macs have been hit with this malware. Given that the malware has not been observed to have self-propagating functionality like a worm or virus, its maker would have had to put an inordinate amount of effort into widely distributing a mere proof of concept Trojan horse.
I had several people ask me if – or assert that – Silver Sparrow was a proof-of-concept malware. IMO, there’s no evidence of that. A PoC _virus_ that gets out of control could hit the number of machines we’ve seen infected, but a PoC Trojan spreading that far is highly unlikely.
— Thomas Reed (@thomasareed) February 23, 2021
And yet, we still don’t know what Silver Sparrow’s ultimate goal was, or who made it—hence the word “mysterious” frequently being used to describe the malware campaign.
So what makes Silver Sparrow different from other Mac malware? It has a few unusual characteristics that make it noteworthy.
Silver Sparrow is the second M1-native Mac malware discovered
The main thing that seems to be grabbing headlines is that one of the two discovered Silver Sparrow variants runs natively on new Apple silicon Macs with M1 processors, as well as running natively on Intel-based Macs. Apple’s terminology for an app that runs natively on both architectures is “Universal Binary.”
There are actually two known versions of Silver Sparrow; the first one was compiled for Intel Macs, and the second was compiled as a Universal Binary for both Intel- and M1-based Macs.
It’s worth noting, however, that M1 Macs can often run Mac malware compiled only for Intel, due to Apple’s Rosetta technology which enables Intel binaries to run on M1 (aka Apple silicon or ARM-based) Macs. Therefore, much of the malware designed to run on Intel Macs can also run on M1 Macs.
However, Silver Sparrow is actually the second known Mac malware family to be compiled as a Universal Binary.
Credit for the first published report about M1-native malware goes to independent Mac security researcher Patrick Wardle, who published his analysis of “GoSearch22,” an OSX/Pirrit variant, about four days before Red Canary published its write-up of Silver Sparrow. Intego VirusBarrier’s existing protection against Pirrit preemptively blocked the new variant found by Wardle.
Related: Intego’s 2018 interview of Pirrit’s original discoverer, Amit Serper
We can expect that virtually all Mac malware from this point forward will be designed to run on both architectures. Apple makes it easy for developers to write cross-architecture Mac apps, which is usually a good thing, but is unfortunate in the case of malware.
So while M1-native malware may seem novel for the moment, soon most new macOS malware will be M1 native.
Silver Sparrow is (at least) the sixth major Apple notarization failure
 According to our research, the discovery of Silver Sparrow marks at least the sixth major time that Apple’s notarization process has failed to detect malware families that have either been distributed in the wild or uploaded to VirusTotal.
According to our research, the discovery of Silver Sparrow marks at least the sixth major time that Apple’s notarization process has failed to detect malware families that have either been distributed in the wild or uploaded to VirusTotal.
Notarization is specifically supposed to identify and block new malware before it can ever infect Macs, but Apple’s automated notarization process has repeatedly notarized dozens of malware samples that Apple has failed to detect as malicious.
Silver Sparrow uses JavaScript during installation
Another novel thing about Silver Sparrow is its use of JavaScript code within the macOS installer during the pre-installation phase.
Malware that installs via Apple’s Installer app typically prefers to rely on preinstall shell scripts (similar to typing commands in the Terminal, but run in the background without the user’s knowledge) instead of JavaScript.
Silver Sparrow has had wide distribution, but its goal is unknown
Most malware has a clear purpose, such as spying on victims, holding victims’ files for ransom, or injecting advertisements or mining for cryptocurrency in an attempt to make a profit for the malware distributor.
Silver Sparrow’s wide distribution, in spite of its lack of an obvious raison d’être, is therefore a bit puzzling.
According to the original report about Silver Sparrow, one antivirus company found evidence of nearly 30,000 Macs having been infected as of February 17. By February 23, less than a week later, that number had reached nearly 40,000.
Given that this data is based on observations from a single antivirus vendor—and given that a significant percentage of Mac users don’t run antivirus software at all—it’s quite likely that the actual number of Macs hit by Silver Sparrow is much higher.
These numbers are primarily based on the existence of a particular zero-byte file left behind by the malware after it uninstalls itself. In fact, of Macs with Silver Sparrow detections, 99.5% seemed to only have that one harmless file remaining.
Intego has been monitoring this threat, and we can corroborate that very few Macs seem to have an active Silver Sparrow infection as of today.
In lab analyses, Silver Sparrow malware has not yet been observed downloading a final malicious payload, so it is unclear what the malware maker’s intentions were, or whether it ever did anything beyond install a method of persistence (a LaunchAgent that allows the malware to get loaded back into memory after a reboot), and eventually uninstall itself.
How can one remove or prevent Silver Sparrow and other threats?
Given that Apple has frequently notarized Mac malware, and Apple’s other threat mitigation features such as Gatekeeper, XProtect, and MRT do not block many types of threats, it is evident that Apple’s own macOS protection methods are insufficient by themselves.
Related: Do Macs need antivirus software?
 Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate this malware. VirusBarrier detects Silver Sparrow as OSX/Slisp.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate this malware. VirusBarrier detects Silver Sparrow as OSX/Slisp.
VirusBarrier is designed by Mac security experts, and it protects against a much wider variety of malware than Apple’s mitigation methods.
Although some reports have suggested that users can “vaccinate” their Macs by creating a blank file at ~/Library/._insu (which could theoretically prevent the malware from installing, or cause the malware to remove itself), and at least one company actually created a script to assist users in doing so, we do not recommend this for several reasons, as follows.
Apple has already effectively disabled the two known variants of this malware, so it should not be possible for it to install anymore. Additionally, any potential future versions of this malware would likely avoid installing itself based on the existence of a file whose path is now widely known to the public. Moreover, installing your own empty file at ~/Library/._insu can lead to false-positive detections from some anti-malware products, which can make it more difficult for those companies to determine the actual reach of the malware.
If you believe your Mac may have been infected, or to prevent future infections, it’s best to use antivirus software from a trusted Mac developer that includes real-time scanning, such as VirusBarrier X9—which also protects Macs from the first known M1-native malware, a variant of OSX/Pirrit. VirusBarrier proactively blocked the new Pirrit variant before it was even discovered.
Note: Intego customers running VirusBarrier X8, X7, or X6 on older versions of Mac OS X are also protected from these threats. It is best to upgrade to the latest versions of VirusBarrier and macOS, if possible, to ensure your Mac gets all the latest security updates from Apple.
Indicators of compromise (IoCs)
Following are some specific ways to identify whether a Mac may have been infected by Silver Sparrow.
This malware has used the generic-sounding filenames “update.pkg” and “updater.pkg” for the initial installation. The existence of a file with one of those names in the ~/Downloads (i.e. /Users/username/Downloads) folder may be a possible sign of infection.
Apple has since revoked the Developer IDs that were used for signing and requesting notarization of this malware. The developer names and Team IDs of the revoked dev accounts are:
Julie Willey (MSZ3ZH74RK) Saotia Seay (5834W6MYX3)
The following SHA-256 file hashes belong to known OSX/Slisp files associated with this malware campaign.
1decb4070db4dfe5d68ba502cf3a67de96a69ea6f3acfa4454795f96472ccc0d 38c9b858c32fcc6b484272a182ae6e7f911dea53a486396037d8f7956d2110be* 3950ff488c66db167d5c80d8138edfdbf326af5a42475726b6ebc44b94efd866* 77f7ecb56081c77f0348180def2985120b10b929e570b05b4f152aa7b9de2c71 8f484a978016cb44b25fd8d9b61250c25caf69aadc891f04c4e310a590650d9f ae82807fd98ea552469dd29182e307935a8319867e45346516fd90998faf2d65* c153eb1bb88c86e08d12bb49a661fbe54dab2eff7dcf69c87a1b1bc0ee2777ef c7dd06b20b64b64d3b155b6b77c2778a08ef6a6c0396d7537af411258e57af1e *first reported by Intego
The following file and directory paths have been associated with this malware. The existence of these files or folders on a Mac could be a possible sign of an infection, or a past infection in the case of the “._insu” file:
~/Downloads/update.pkg ~/Downloads/updater.pkg ~/Library/._insu (most common; 0-byte file) ~/Library/Application Support/agent_updater/ ~/Library/Application Support/verx_updater/ ~/Library/LaunchAgents/agent.plist ~/Library/LaunchAgents/init_agent.plist ~/Library/LaunchAgents/init_verx.plist ~/Library/LaunchAgents/verx.plist /Applications/updater.app/ /Applications/tasker.app/ /tmp/agent.sh /tmp/version.json /tmp/version.plist /tmp/verx
A copy of the /tmp/verx file has not yet been obtained by any malware researchers. If you find a copy of it, please submit it to Intego for analysis.
The apps dropped into the /Applications folder may have one of the following Bundle IDs:
com.hello.tasker - first reported by Intego com.tasks.updater
The following domains have been observed to have ties with this malware:
api.mobiletraits[.]com api.specialattributes[.]com mobiletraits.s3.amazonaws[.]com specialattributes.s3.amazonaws[.]com update-v3a98x2.s3.amazonaws[.]com
Any recent network traffic to or from any of these domains (from mid-August 2020 to present) should be considered a possible sign of an infection.
How can I learn more?
For additional details about Silver Sparrow, you can refer to the original write-up by Tony Lambert as well as later write-ups by Phil Stokes and Thomas Reed.
 We discussed Silver Sparrow malware on episode 176 of the Intego Mac Podcast. Be sure to subscribe to make sure you don’t miss any episodes! You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
We discussed Silver Sparrow malware on episode 176 of the Intego Mac Podcast. Be sure to subscribe to make sure you don’t miss any episodes! You’ll also want to subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news.
You can also follow Intego on your favorite social and media channels: Facebook, Instagram, Twitter, and YouTube (click the 🔔 to get notified about new videos).
Silver Sparrow header image based on “House Sparrow (Passer domesticus)” by Mathias Appel (CC0); modified by Joshua Long, Intego.