Malware + Recommended + Security News
iWorm Botnet Uses Reddit as Command and Control Center
Posted on
by
Derek Erwin

A new day, and a new threat to Mac OS X. Virus hunters have discovered a sophisticated botnet targeting Mac OS X computers and using a novel technique to operate. The malware has infected about 18,500 Macs, according to recent statistical analysis.
The Mac malware, called iWorm, uses a complex multi-purpose backdoor, through which criminals can issue commands that get the malicious program to carry out a wide range of instructions on the infected Macs.
According to researchers, the backdoor makes extensive use of encryption in its routes. It is capable of discovering what other software is installed on the infected machine and sending out information about it (operating system), opening a port on it, downloading additional files, relaying traffic, and sending a query to a web server to acquire the addresses of the C&C servers, essentially turning your Mac into a zombie.
Installing iWorm
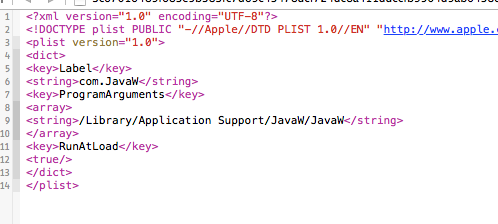
During installation, the malware first installs a backdoor into the directory /Library/Application Support/JavaW, after which the dropper generates a p-list file, so that the backdoor is launched automatically. Furthermore, it disguises itself as the application com.JavaW and sets itself to autostart via /Library/LaunchDaemons/.
Analysis indicates that the malware begins to seed itself into your Mac upon initial launch, saving its configuration data in a separate file and attempts to read the contents of the /Library directory to determine which of the installed applications the malware won’t be interacting with. If the bot cannot find ‘unwanted’ directories, according to reports, it uses system queries to determine the home directory of the Mac OS X account under which it is running, checks the availability of its configuration file in the directory, and writes the data needed for it to continue to operate into the file.
How Reddit.com played its part
Many types of malware use command and control servers that they connect to, in order to get instructions from the creators of the malware. The problem with using these servers is that their IP addresses are specified in the malware code, and the servers can generally be taken down.
What’s particularly interesting about iWorm is that the botnet uses a novel technique to operate: it uses reddit.com. Infected Macs receive commands from servers under the control of cybercriminals, using information posted in messages on Reddit in order to acquire a control server address list:
Then Mac.BackDoor.iWorm opens a port on an infected computer and awaits an incoming connection. It sends a request to a remote site to acquire a list of control servers, and then connects to the remote servers and waits for instructions.
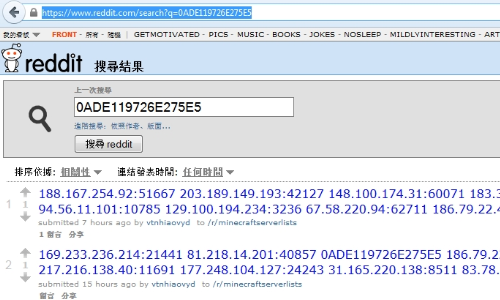
Interestingly, in order to acquire a control server address list, the bot uses the search service at reddit.com. It sends a search query that specifies hexadecimal values of the first 8 bytes of the MD5 hash of the current date. The reddit.com search returns a web page containing a list of botnet C&C servers and ports published by criminals in comments to the post minecraftserverlists under the account vtnhiaovyd.
The bot picks a random server from the 29 addresses on the list and sends queries to each of them. Search requests to acquire the list are sent to reddit.com in 5-minute intervals, according to Dr. Web’s report.
While establishing a connection to the server whose address is picked from the list using a special routine, the backdoor attempts to determine whether the server address is on the exceptions list and engages in a data exchange with the server to employ special routines for authenticating the remote host. If successful, the backdoor sends the server information about the open port on the infected machine and its unique ID and awaits directives.
It’s important to note that Reddit is not directly at fault, and it appears that reddit.com/r/minecraftserverlists has been shut down. (Intego malware researchers are unable to get persistent files on their systems due to the page being shut down.) If that is the only source criminals are using for the C&C, then they’re dead in the water.
However, as Graham Cluley noted on his blog, there is nothing to stop the hackers from using an alternative service, such as Twitter, to communicate with the Mac botnet. Graham wrote:
And it’s important to stress that Reddit isn’t spreading the infection – it’s simply providing a platform that is helping the botmasters communicate with the Mac computers they have managed to infect.
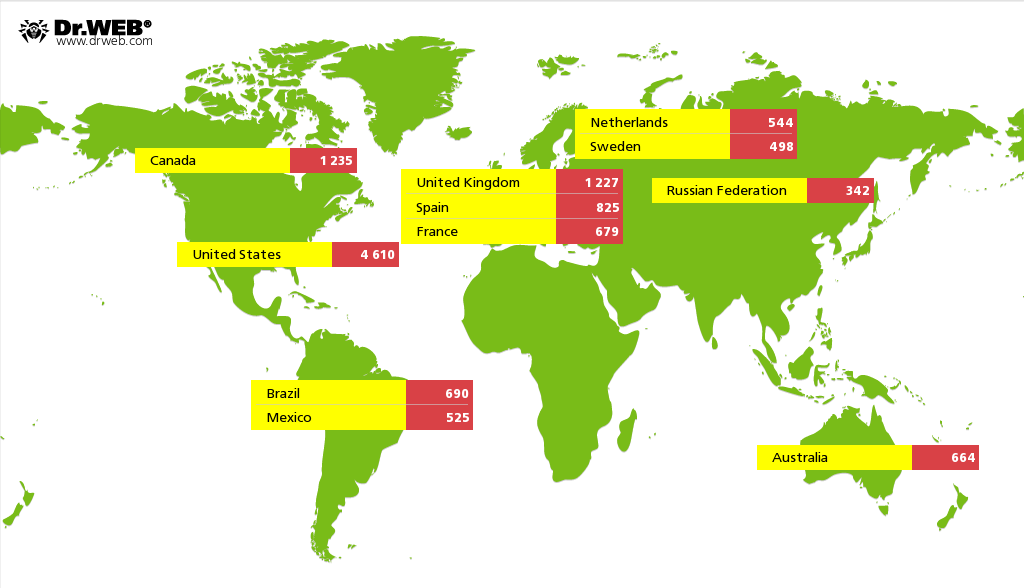
Information collected by Doctor Web’s researchers shows that most of the infected Macs—4,610, representing 26.1% of the botnet—reside in the United States. Canada ranks second, and the United Kingdom ranks third in terms of infected Macs.
How to check if you are infected
According to research, the iWorm botnet installs itself to the following two locations:
/Library/Application Support/JavaW /Library/LaunchDaemons
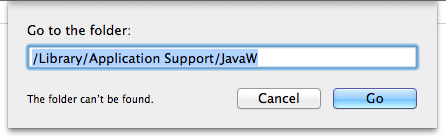
To check to see if you are infected, open the Finder window and select the Go menu, and then choose “Go to Folder.”
Copy and past the following into the window that opens:
/Library/Application Support/JavaW
Then, click the Go button. If the window displays the message, “The folder can’t be found,” in the bottom left corner, then you should be safe.
However, as mentioned by Thomas Reed over at The Safe Mac, if a Finder window opens showing the contents of this folder, then you are infected.
Stay a step ahead
If after running the test above you find that you are not infected, you can take precautionary steps that enable you to receive a pop-up alert if a new item gets added to any of the locations that the iWorm malware installs itself to.
To do so, open the Finder, choose Go to Folder from the Go menu, and then copy and paste the following path into the window that pops up:
/Library/LaunchDaemons
Then, click the Go button.
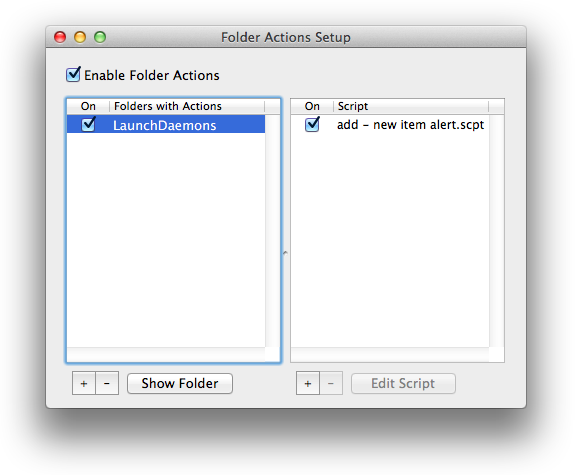
You will be taken to the LaunchDaemons folder; right-click on the folder, and choose Folder Actions Setup.
Choose the script “add – new item alert.scpt” and click the Attach button.
Then, select the checkbox to Enable Folder Actions.
If possible, repeat these steps for /Library/Application Support/JavaW.
Now, if a new item gets added to any of these locations, you will get a pop-up alert. Note that when adding alerts to the folders, not every file added is an indication of iWorm or malware in general. You need to inspect the file and see if there’s any references to JavaW.
If after inspecting the file you come to find a reference to JavaW, take immediate measures to eradicate the malware.
How to eradicate iWorm malware
As the Mac security threat landscape evolves, it’s ever so important to protect your computer using a layered approach to security. Yes, Macs get malware, so you should invest in Mac anti-virus software to protect your computer. In fact, it’s a good idea to get anti-virus and a firewall, as a layered defense will protect you much more effectively than any one layer by itself.
Intego VirusBarrier with up-to-date virus definitions detects and eradicates this malware, which it identifies as OSX/iWorm.