Malware + Security & Privacy + Security News
Don’t Jailbreak Your iPhone if You Want to Avoid the Cloud Atlas Malware
Posted on
by
Graham Cluley

Cloud Atlas is the latest purported example of sophisticated state-sponsored malware, said to have snooped on diplomats, oil industry workers and the financial industry, intercepting communications and recording phone calls.
And iPhone and iPad users don’t escape entirely unscathed.
According to detailed reports published by Blue Coat and Kaspersky, victims in Russia and other countries around the globe would be duped into opening documents and clicking on links—believing they were going to read an advert for an old diplomatic car or click on a link to an upgraded version of WhatsApp.
The devices which were probably most likely to have been affected by the malware attack, which exploited vulnerabilities in the Word Rich Text Format (RTF), were regular Windows computers, who might find themselves on the receiving end of decoy documents claiming to come from “Mrs World” (seemingly with words taken from a Russian news site), adverts for diesel engine parts or files called “Diplomatic Car for Sale.doc.”

But the good news is that if you haven’t jailbroken your iOS device, Cloud Atlas isn’t likely to give you much cause for concern.
The simple truth can’t be ignored that there is much much more malware for Windows and Android than there is for Macs and iPhones.
That doesn’t mean, of course, that you can afford to be glib when it comes to protecting your Apple devices—but the majority of malware that is created is written for operating systems that weren’t developed in Cupertino.
And the sophisticated Cloud Atlas malware (also called “Inception” by some security vendors, but detected by Intego products as iOS/CloudAtlas) infects Windows computers, BlackBerrys and Android devices, appears to be no different.
It can only exploit Apple’s iOS iPhones and iPads if they have been jailbroken.
And, I have to wonder, is jailbreaking as popular today with iPhones and iPads as it was in the past? The addition of new features into iOS 8 (such as share extensions and custom keyboards) has surely chipped away at the attraction of cracking open the operating system and allowing apps from beyond the walled garden of the App Store to be installed.
None of this, of course, makes it any less attractive for a determine hacker (or a foreign government interested on spying on the secrets of others) from attempting to infect whatever brand of mobile phone their target might choose to carry. And that probably explains why security researchers found the iOS malware on the same server that was hosting the Android and BlackBerry trojans.
Blue Coat researchers observed that links to the mobile versions of the Cloud Atlas spyware would be distributed by bogus mailshots, such as this one claiming to be a new version of WhatsApp sent to a Paraguayan government email address:
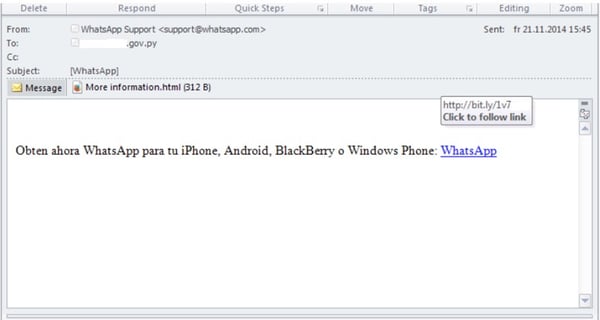
Once installed on a jailbroken iOS device, the malware can collect a wide variety of information and transmit it to an FTP account under the attackers’ control.
None of this, though, will be successful if you left your iPhone or iPad in its factory state, and declined to jailbreak it to allow unvetted third-party apps to have free reign over your device.
The message is simple: You may have lots of reasons why you want to jailbreak your iPhone, but you are putting yourself at greater risk of compromise via government spyware.