New Java Zero-Day Exploit Shows Multi-Platform Development
Posted on
by
Lysa Myers
Update September 10, 2012
This exploit has been patched by Oracle and Apple. You can find more information about the update here.
____
Update August 29, 2012
The exploit has been has now been given a reference number in the Common Vulnerability and Exposures List: CVE-2012-4681
____
There is a new Java zero-day exploit that was discovered last night, which is currently being used in targeted attacks against Windows users to deliver the Poison Ivy Remote Access Trojan. While this is in the wild, this is not being widely used at this time. What is more worrisome is the potential for this to be used by other malware developers in the near future.
The exploit in all major browsers and appears to work on some versions of Linux, OS X 10.7 and higher, as well as Windows, if you’re using the latest version of Java.
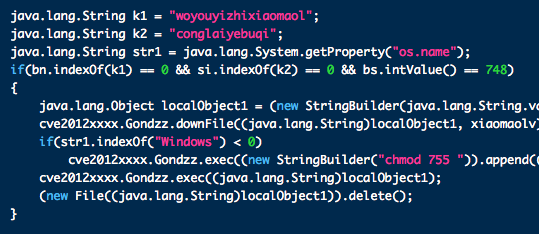
At this time there is no patch available for this exploit, so it’s highly recommend that you disable Java until this vulnerability has been fixed.
Java is a popular vehicle for malware authors – an unpatched Java flaw was largely responsible for the success of Flashback earlier this year. Additionally, Java applets have been part of the installation process for almost every malware attack on OS X this year. Oracle is on a quarterly patch schedule, which means the next likely patch will not be released until October 16. In malware terms, several weeks is quite a huge gap in protection. As source code for this exploit is already being distributed, the odds are very good that we’ll see more working malware in the wild before this is patched. Given the interest lately in multi-platform malware and the fact that this vulnerability works on Linux and OS X, it is particularly important that we take preventative measures to protect ourselves.
Detection for the existing threat and the proof of concept (now included in the MetaSploit tool) are included in today’s virus definitions. Intego VirusBarrier users are advised to update as soon as possible – this may not protect against all possible implementations of this exploit, but it is a generic detection that may help proactively protect against new variants based on the known implementation.