Apple Neglects to Patch Two Zero-Day, Wild Vulnerabilities for macOS Big Sur, Catalina
Posted on
by
Joshua Long
![]()
Update: After 6.5 weeks—and significant public pressure resulting from this article—Apple finally released patches for macOS Big Sur and macOS Catalina on May 16 that address these actively exploited vulnerabilities.
Apple has chosen to leave an estimated 35–40% of all supported Macs in danger of actively exploited vulnerabilities.
Last week, on March 31, Apple patched two “actively exploited” (i.e. in-the-wild, zero-day) security vulnerabilities for macOS Monterey.
After nearly a week, Apple still has not released corresponding security updates to address the same vulnerabilities in the two previous macOS versions, Big Sur (aka macOS 11) and Catalina (aka macOS 10.15).
Both of these macOS versions are ostensibly still receiving patches for “significant vulnerabilities”—and actively exploited zero-day vulnerabilities certainly qualify as significant. Apple has maintained the practice of patching the two previous macOS versions alongside the current macOS version for nearly a decade. But now, Apple has neglected to patch both Big Sur and Catalina to address the latest actively exploited vulnerabilities.
Let’s break down what the problem is, and what Apple needs to do to remedy this serious issue.
In this article:
- Which Apple operating systems remain vulnerable?
- How many Macs are affected by the new vulnerabilities?
- Has anything like this ever happened before?
- Frequently asked questions
- How can I learn more?
Which Apple operating systems remain vulnerable?
Apple’s macOS Monterey 12.3.1 update, released last week, included fixes for two actively exploited vulnerabilities: CVE-2022-22675 (a bug in AppleAVD) and CVE-2022-22674 (a bug in Intel Graphics Driver). The former remains unpatched for macOS Big Sur, and the latter appears to affect both Big Sur and Catalina.
This is the first time since the release of macOS Monterey that Apple has neglected to patch actively exploited vulnerabilities for Big Sur and Catalina. The previous three actively exploited vulnerabilities were each patched simultaneously for Monterey, Big Sur, and Catalina.
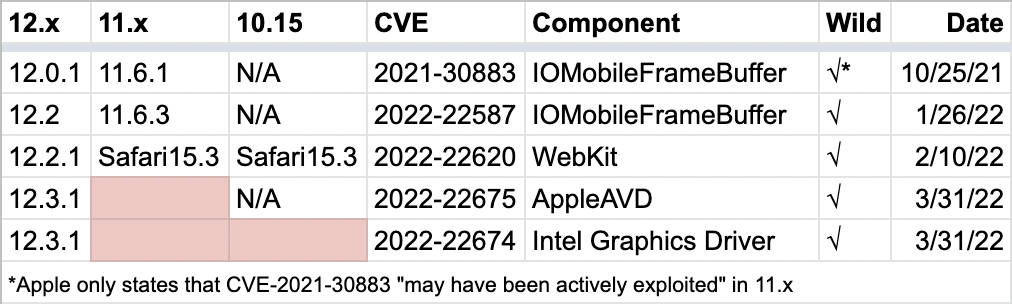
List of all macOS Monterey-era vulnerabilities that Apple has identified as actively exploited (i.e. zero-day vulnerabilities used in in-the-wild attacks). Until now, Apple had patched them simultaneously for all three supported macOS versions. Credit: Intego.
Big Sur: CVE-2022-22675
Intego has confirmed that macOS Big Sur remains vulnerable to CVE-2022-22675, an actively exploited vulnerability in the AppleAVD component.
Last week, Mickey Jin—one of the top reporters of OS vulnerabilities to Apple—reverse engineered Apple’s patch for macOS Monterey. He then verified that macOS Big Sur does indeed still contain the same vulnerability. Jin observed that M1-based Macs running macOS Big Sur remain vulnerable to CVE-2022-22675.
We have inquired of Apple several times about this over the past week. Apple has not responded to any of our questions. It remains a mystery why Apple seems to have deliberately left macOS Big Sur susceptible to this actively exploited vulnerability. It is also unknown whether or not a patch may come eventually (either because Apple was already planning to, or due to public pressure).
Meanwhile, macOS Catalina does not contain the vulnerable component, AppleAVD, so Catalina is unaffected by CVE-2022-22675 specifically.
Incidentally, according to Jin, it appears that iOS 14 and iPadOS 14 are also vulnerable to CVE-2022-22675. However, Apple officially (albeit quietly, and without warning) stopped supporting iOS and iPadOS 14 in January 2022, so it is no surprise that users must upgrade to the latest version of iOS 15 or iPadOS 15 to continue getting security updates. Last week’s iOS and iPadOS 15.4.1 updates—which are compatible with all devices running iOS or iPadOS 14—provide a fix for CVE-2022-22675.
By contrast, macOS Monterey and macOS Big Sur each dropped support for certain Mac hardware, so some Mac users cannot upgrade beyond Catalina or Big Sur to receive security updates that are currently only offered in Monterey.
Big Sur and Catalina: CVE-2022-22674
It is highly likely that macOS Big Sur and macOS Catalina are both vulnerable to CVE-2022-22674, the other actively exploited vulnerability that was fixed for only macOS Monterey last week.
Intego is actively working to confirm that Big Sur and Catalina are affected. Unfortunately, Apple has neither issued a statement nor responded to our inquiries. Apple’s patch notes indicate that CVE-2022-22674 was reported by an “anonymous researcher,” making it difficult to independently and conclusively confirm whether the vulnerability affects previous macOS versions without reverse engineering Apple’s Monterey patch.
However, we have high confidence that CVE-2022-22674 likely affects both macOS Big Sur and macOS Catalina. Nearly all vulnerabilities in the Intel Graphics Driver component in recent years have affected all versions of macOS.
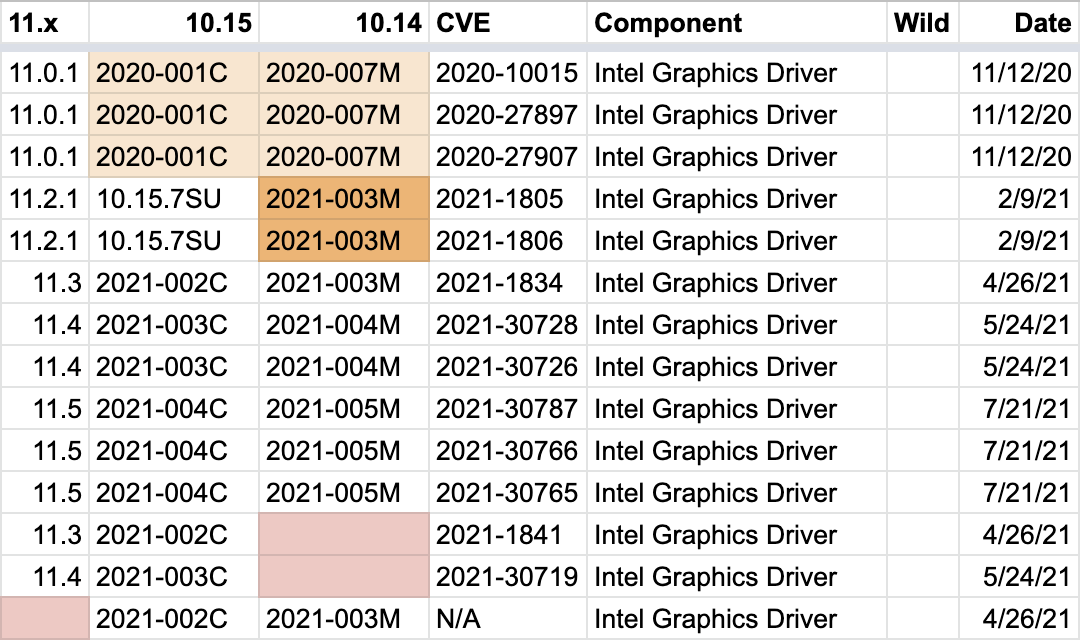
For reference, a list of Intel Graphics Driver vulnerabilities that Apple patched while Big Sur was the latest macOS. Apple’s patches indicate that nearly all Intel Graphics Driver vulnerabilities were present in all macOS versions. Credit: Intego.
Until Apple’s Monterey patch for CVE-2022-22674 can be reverse-engineered, past experience is a strong indicator that the vulnerability is highly likely to be present in both Big Sur and Catalina. The lack of patches for these operating systems leaves them highly susceptible to attacks that target this actively exploited vulnerability.
Other vulnerabilities in Big Sur and Catalina
The main focus of this article is to point out the existence of the two new, actively exploited vulnerabilities in macOS Big Sur and Catalina. However, it’s worth mentioning that there are also dozens of vulnerabilities that Apple has not identified as actively exploited, that remain in macOS Big Sur and Catalina.
Quick update: #Safari 15.1 was released for Big Sur & Catalina yesterday, & its release notes indicate that 5 of the 7 #WebKit vulnerabilities were fixed. Two appear to remain unpatched for 11.x and 10.15.x: CVEs 2021-30823 (Gullasch @0x41414141) & 2021-30861 (@_r3ggi & Pickren).
— Josh Long (the JoshMeister) (@theJoshMeister) October 28, 2021
A preliminary assessment of just the first round of patches at macOS Monterey’s release in October 2021 indicated that there may have already been well over a dozen vulnerabilities that were not patched for previous macOS versions.
Apple has never fully disclosed its patching policies for macOS. Apple once publicly commented—way back in 2003—that “it is Apple’s policy to quickly address significant vulnerabilities in past releases of Mac OS X wherever feasible.” Since September 2012, Apple’s practice has been to release patches for the current and two previous major macOS versions, usually simultaneously. Only recently did Intego’s research bring to light Apple’s inconsistency and lack of parity between the company’s macOS security patches (more on this below).
How many Macs are affected by the new vulnerabilities?
We estimate that roughly 35–40% of all Macs in use today are likely affected by one or both of the new actively exploited vulnerabilities.
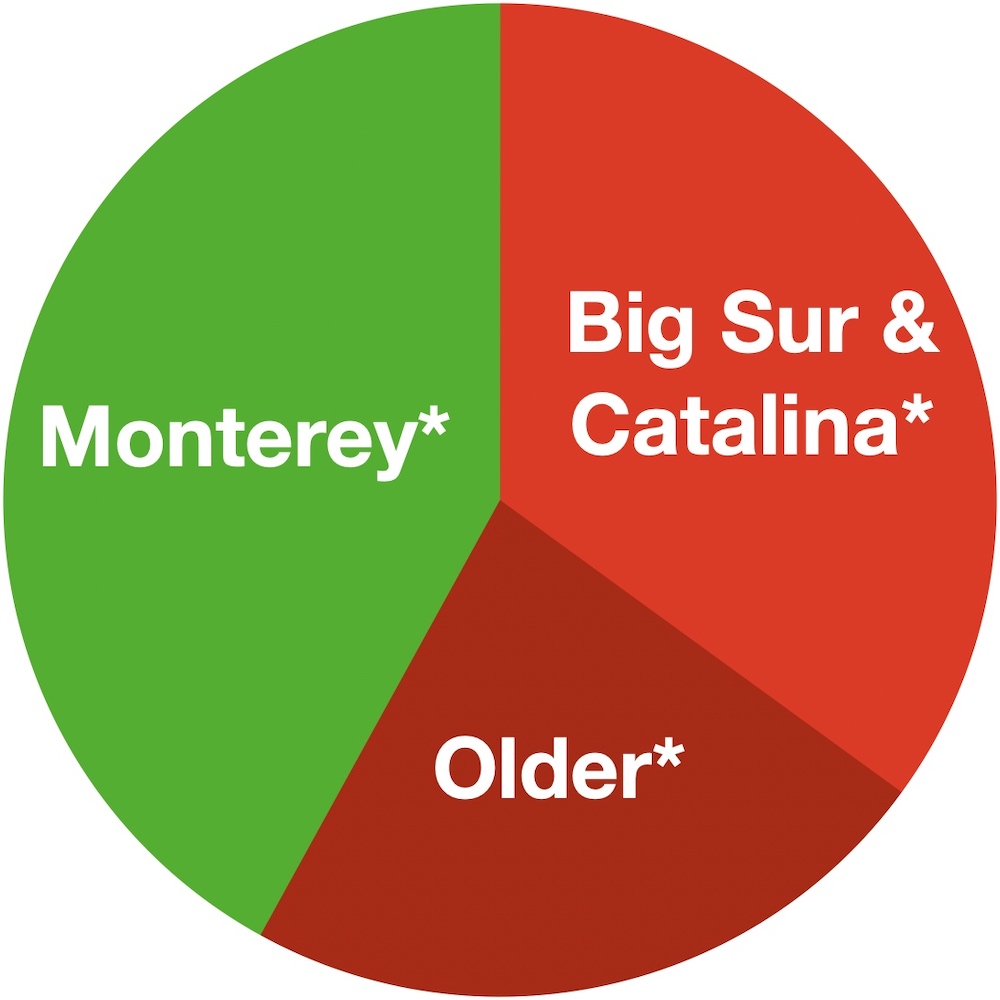
Best estimate of current macOS version market share.
Apple has made it difficult to determine the current macOS version market share with precision. Since macOS Catalina, Apple no longer distinguishes between macOS versions in browser User Agent strings; all macOS versions, including Big Sur and Monterey, now self-identify to Web servers as Catalina. Our best estimates, therefore, are based on pre-Catalina (e.g. 2019, 2018) macOS adoption rates around the same point in the OS release cycle.
With these assumptions in mind, an estimated 55–60% of all actively used Macs today are likely running macOS Big Sur or older, and therefore remain vulnerable to unpatched in-the-wild vulnerabilities. Roughly two-thirds of that 55–60% (i.e. roughly 35–40% of all actively used Macs today) likely run either Big Sur or Catalina specifically.
The only way to ensure that your Mac is as safe as possible from known vulnerabilities is to upgrade to macOS Monterey (assuming that your Mac is compatible with it). The average person would never know this, because Apple still releases patches for Big Sur and Catalina (most recently just three weeks ago, on March 15); it isn’t obvious to most people that Apple’s patches for these macOS versions are incomplete and leave their Macs vulnerable to serious—and in some cases actively exploited—security bugs.
Has anything like this ever happened before?
This isn’t the first time that we’ve observed Apple neglecting to patch serious vulnerabilities, or even actively exploited ones.
Last year, Intego’s Chief Security Analyst, Josh Long, did a deep-dive analysis of macOS vulnerabilities addressed over a year’s worth of patches. At the time, macOS Big Sur was the latest Mac operating system.
Long found that while approximately 48% of the over 400 vulnerabilities were patched for all three supported operating systems (which at the time were Big Sur, Catalina, and Mojave), about 16% were only patched for the current and the one previous (Big Sur and Catalina), and about 34% were only patched for the then-current macOS, Big Sur.
Drilling down specifically into the 15 “actively exploited” vulnerabilities during that timeframe, Long found that six (40%) were patched for all three macOS versions, four (27%) were only patched for Big Sur and Catalina, and five (33%) were only patched for Big Sur, the then-latest version.
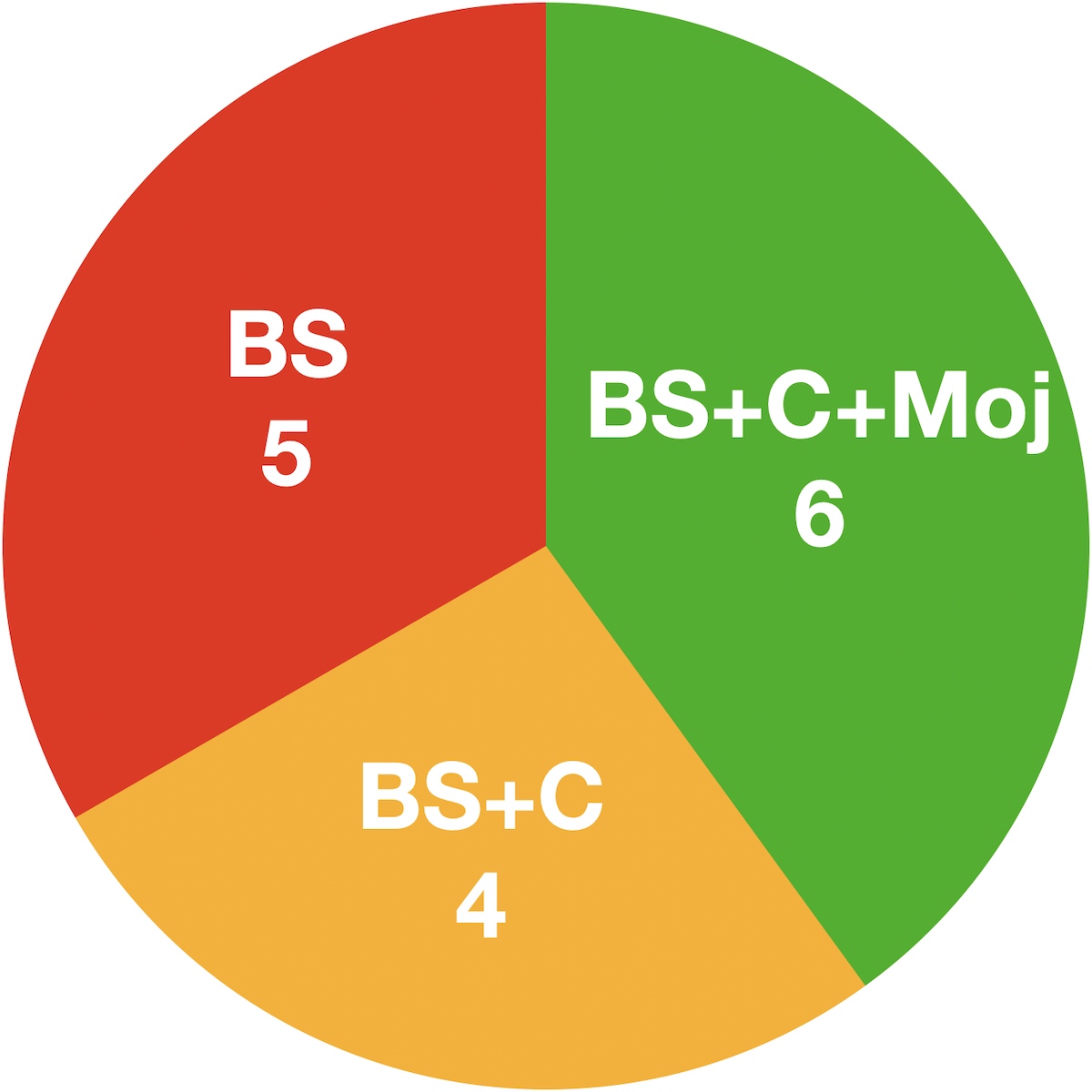
Chart of Big Sur-era actively exploited vulnerabilities. Apple has a history of leaving supported macOS versions in danger from actively exploited vulnerabilities. Credit: Intego.
So, in fact, Apple has an unfortunate history of knowingly leaving “supported” macOS versions unprotected from some in-the-wild, actively exploited attacks. This type of scenario where a vendor chooses not to release a patch is sometimes referred to as a “perpetual zero-day.”
We had hoped that Apple had since improved for the better, but the lack of patches for the current actively exploited vulnerabilities seem to indicate otherwise.
Frequently asked questions
Q. Has Apple confirmed that Big Sur and Catalina are vulnerable?
A. No, Apple has not responded to any of our inquiries, and we don’t expect that they will. Apple often ignores inquiries from press and security researchers.
However, we have confirmed that macOS Big Sur is indeed vulnerable to CVE-2022-22675, the actively exploited vulnerability in AppleAVD.
There is a strong likelihood that macOS Big Sur and macOS Catalina are both vulnerable to CVE-2022-22674, the actively exploited vulnerability in Intel Graphics Driver; most similar vulnerabilities found to date have affected every version of macOS.
Q. Does Apple plan to release updates for Big Sur and Catalina?
A. Apple has neither responded to our inquires nor made any public statement about this. We do not know whether or not Apple will eventually make a patch available for Big Sur or Catalina (either because Apple was already planning to, or due to public pressure resulting from this attention).
Q. Is there any indication of which threat actor or APT group has exploited these vulnerabilities? Are they related to the Russia-Ukraine conflict?
A. Apple does not make public statements about such details, and little information is available elsewhere. However, now that Apple has released patches for Monterey and iOS 15 that can be reverse-engineered, additional threat actors may attempt to exploit these vulnerabilities. This makes it all the more urgent for Apple to release patches for Big Sur and Catalina.
Q. Why else is this a serious problem?
A. Apple is providing a false sense of security by providing inconsistent security updates—and not patching every highly critical (or even every zero-day) vulnerability—for two widely used macOS versions comprising an estimated 35–40% of all Macs in use today. Apple has never publicly acknowledged that it neglects to patch all highly critical vulnerabilities in the two previous macOS versions.
Q. What is the purpose of drawing attention to this issue?
A. First, we hope to encourage Apple to make things right by patching the still-vulnerable “supported” macOS versions—and continuing to do so proactively (without third parties like us having to call them out on it) in the future.
Second, we hope to raise awareness among consumers and IT professionals that Apple’s current practices leave the two previous macOS versions vulnerable to serious security flaws, including ones actively exploited in the wild. Mac users should be aware that Apple’s security patches for the two previous macOS versions are inconsistent and incomplete, and thus it’s generally safest to use the most recent major edition of macOS (currently Monterey). Apple should, at minimum, clearly communicate this to its customers, but the company has never done so.
How can I learn more?
For additional information about Intego’s past research into macOS vulnerabilities and Apple’s patching policies, see this related article: Apple’s Poor Patching Policies Potentially Make Users’ Security and Privacy Precarious.
Apple’s Poor Patching Policies Potentially Make Users’ Security and Privacy Precarious
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, security and privacy stories, and offer practical advice on getting the most out of your Apple devices.
In episode 233, Josh and Kirk discussed why iOS updates—including ones containing critical security fixes for actively exploited vulnerabilities—can take up to four weeks to roll out to users. Be sure to follow the podcast to make sure you don’t miss any episodes!
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()